Source: heimdalsecurity.com – Author: Alina Georgiana Petcu
For the most part, today’s modern workplace has grown accustomed to cyberattacks directed by third parties that are external to the organization. But what can you do when the call is coming from inside the house? How can you successfully discover and mitigate a malicious insider threat before it’s too late?
In the following lines, I will explain what a malicious insider is, as well as what their motivation is. I will also tell you more about how you can recognize one and back everything up with quite a few real-life teachable examples. Finally, I will also tell you everything about preventing a malicious insider threat, so if it’s actionable advice you are looking for, make sure to read until the end.
What is a Malicious Insider?
A malicious insider is a type of insider threat that is specifically motivated by ill intent, as the name suggests. According to the Australian Cyber Security Centre (ACSC), it can consist of either current or former employees, as well as business associates and any other third party with legitimate access to your corporate network. What defines their entry into your system as malicious is the fact that they use it to destroy or otherwise sabotage your data and property.
How to Recognize a Malicious Insider
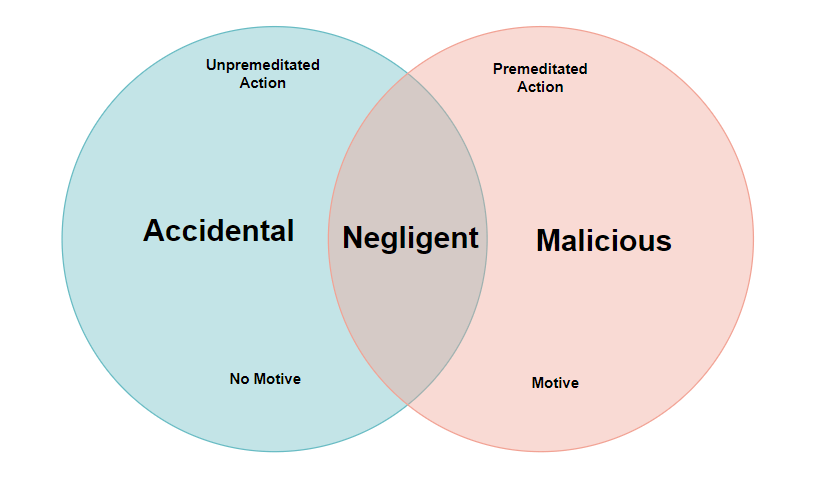
As further explained by the ACSC, the malicious insider threat does not include well-intentioned employees who accidentally put the company’s cybersecurity at risk. To better understand the difference between this type of situation and one with ill intent behind it, let’s have a look at the three main types of dicey workplace behavior:
- Accidental, which describes an unpremeditated action with no motive attached to it. Benign workflow mistakes and unconscious human errors such as inadvertently opening a phishing attachment or unknowingly giving away login credentials fall into this category. It is not an ideal scenario, but the person responsible for it most likely didn’t have any nefarious gain from it.
- Negligent, which is at the borderline between accidental and malicious. The staff member at the center of negligent behavior is not necessarily a cyberattacker, but their intentions are not pure either. Unreliable employees that just don’t care about their job anymore are usually those accountable for this category of incident.
- Malicious, which portrays a premeditated action backed up by ulterior motive. Disgruntled employees or resentful contractors are the ones in charge of malicious insider cyberattacks. Their purpose is to steal your data and either perform further damages themselves or sell it on the Dark Web to allow others to do so.
Malicious Insider Motives
As mentioned above, a major driving force behind malicious insider attacks is that of ulterior motives. There are many reasons why a discontented employee or contractor might try to infiltrate your network, and they include:
- revenge,
- coercion,
- ego,
- ideology,
- or financial gain.
These purposes can have several outcomes for the targeted company:
- damaged brand reputation,
- system malfunctioning,
- stolen business secrets,
- illegal trading,
- or malware infections.
Malicious Insider Threat Indicators
Now that we’ve established what a malicious insider is and what motivates them, it’s time to find out how to spot one in your network. There are three main indicators that a malicious insider is wreaking havoc in your corporate system, and they all consist of various instances of anomalous activity. You will find them explained below, in no particular order:
- Unusual traffic spikes when it comes to network data transfers usually means that someone is in there trying to steal your confidential information.
- Activity at odd hours is another dead giveaway. When an employee logs in at three in the morning or any other weird moments outside of office hours, they’re up to no good.
- Retrieving uncommon data or accessing strange resources that have nothing to do with the general workflow means that a member of your company’s staff has a nefarious ulterior motive.
Malicious Insider Scenarios and Examples
a. Gaining Profit from Privileged Data
A malicious insider with financial gain in mind might use your company’s privileged data for profit. This usually involves a larger profit scheme with at least two actors, namely someone with access to confidential information and someone to purchase it. Here are few famous instances of this scenario that have been covered by reputable media outlets.
In 2004, America Online (AOL) software engineering Jason Smathers abused his access rights into the company’s database by stealing its subscriber list and selling it to malspam operators. The list in question contained 92 million email addresses belonging to AOL customers. Smathers was arrested and charged for his offense.
In 2011, the Bank of America discovered that an anonymous Bank of America employee had turned malicious insider, stealing confidential banking data from customers and selling it to fraudsters. The information pool contained a wide array of sensitive details such as names, addresses, phone numbers, driver’s license information, birth dates, email addresses, mother’s maiden names, Social Security numbers, account numbers, PIN codes, and account balances. The incident cost the reputable institution $10 million in damages.
In 2018, the Guardian reported that Amazon employees had been handing out internal data to merchants via intermediaries in exchange for bribes. This included sales information, reviewers’ email addresses, and a tool that facilitated the deletion of negative reviews.
b. Covertly Accessing Customer Data
Sometimes, a malicious insider with an agenda of revenge or coercion might seek out blackmail materials by covertly accessing customer data. This can happen equally if your clients are celebrities or regular people. Consequences include domestic harassment, sexual harassment, stalking, voyeurism, and even exploitation.
Several well-known examples of this type of dicey behavior have been reported within the National Security Agency (NSA) over the years. In 2003, an NSA employee allegedly monitoring a woman he was having sex with. She reported him and he was investigated internally. Just one year later in 2004, another NSA employee monitored a strange number she found on her husband’s phone to see whether he was cheating on her or not.
Then, in 2011, it was discovered that a female NSA employee stationed overseas had been listening in to the calls of her foreign boyfriend, as well as those of other people she met socially in the country. She motivated her actions through her desire to ascertain the moral character of those individuals. Pretty ironic, if you ask me.
In 2019, VICE described how the employees of several departments in the social media company Snapchat had been abusing the company’s dedicated data access tools to spy on users. One such tool was referred to as SnapLion, and sources claim that it was initially designed to prevent bullying on the popular app.
c. Stealing Data for Competitive Interests
In the case of a malicious insider stealing data to satisfy competitive interests, there are two potential sub-scenarios. A former employee who wants to start their own company that rivals the one they used to work in might do this to gain an advantage over their former employer. Another possibility is of another company directly inciting the theft in exchange for an incentive of sorts.
The first example of this I want to discuss went down in Chicago in 2014. Naturalized Chinese-American citizen Xudong Yao had obtained a job with the Illinois Locomotive Company. In just two weeks, he had downloaded over 3,000 confidential records detailing the manufacturer’s process and components.
Over the next six months, Yao abused his privileges with the company and further downloaded trade secrets. This included technical documents, as well as software codes. He then sought employment with a Chinese automotive telematics service systems company. After being terminated from his position at the ILC in 2015, he traveled to China and took up work with said company. He is wanted by the FBI for his misconduct.
In 2019, Walmart accused technology vendor and partner Capucom of this type of seedy business conduct. According to a filing made by the retail giant, Capucom employees were tasked with sifting through company communications, including those of C-level executives. This allegedly gave Capucom an edge in winning the bid over other competitors. The matter was investigated by the FBI.
d. Sabotaging Data and Company Operations
Sabotage is generally the handiwork of disgruntled employees. This happens because they either know that their days at a company are numbered, or have already been terminated from their position and still mistakenly have access rights to the network.
In 2000, former network administrator at Omega Engineering Corp. Tim Lloyd unleashed a logic bomb onto the company’s network three weeks after he was fired. This successfully deleted the system that handled the company’s manufacturing operation.
In 2008, San Francisco Department of Telecommunications and Information Services (DTIS) network engineer Terry Childs was reassigned and refused to hand over the login credentials to FiberWAN, the city’s fiber-optic network. Within it were San Francisco’s most valuable and sensitive data assets. His case was prosecuted by none other than the current Vice President of the United States, Kamala Harris.
In 2015, Canadian Pacific Railway employee Christopher Victor Grupe received his termination notice from the company. Before returning his work laptop, Grupe used his still-valid access credentials to enter the corporate network and delete a wide array of data from it. His rampage included sysadmin accounts that were either deleted entirely or had their passwords changed. He then tried to conceal his actions but was (clearly) unsuccessful.
e. Compromising Data on Behalf of State Actors
The scenario of compromising data on behalf of state actors sees duplicitous staff members carrying out the instructions or interests of competing nation-states. This category of malicious insider is known as the employed spy, and the Twitter incident from 2019 is a perfect illustration of how this works.
The first case here is that of Ali Alzabarah, a 35-year old computer scientist from Saudi Arabia who climbed the ranks as a Twitter reliability engineer. During his employment, he went rogue and provided the Kingdom of Saudi Arabia and the Saudi Royal Family with confidential information on the accounts of people that have been critical of the political regime of the country.
The second case of nation-state compromise involved 41-year-old Twitter media partnerships manager Ahmad Abouammo. Being responsible for public interest accounts in the Middle East North Africa (MENA) region, Abouammo is guilty of the same crime as Alzabarah at the beckon of the Saudis.
f. Sharing Confidential Data with the Media
The line between a malicious insider sharing confidential data with the media and whistleblowing is a fine one and should be treaded lightly. In my opinion, the best way to differentiate between the two is by keeping the malicious in malicious insider at the forefront. Was the action backed by ill intent instead of an earnest desire to stop the company from committing unlawful actions? Then maybe it’s good-natured whistleblowing after all.
A perfect example of this is that of the 2018 Apple leaks. A total of 29 Cupertino employees were caught disclosing private details about future launches to the press, 12 out of which were arrested for their actions. This type of behavior does not denounce anything immoral on the part of Apple but endangers their sales potential. Thus, it can be considered malicious because it brings prejudice to the company.
How to Prevent Malicious Insider Threat
#1 Practice the Zero Trust Model on a Large Scale
The zero trust model is essential to the mitigation of malicious insider threats. It is a cybersecurity concept that requires everyone, including employees, authenticated, authorized, and continuously validated when entering the corporate network. The term was coined by Forrester analyst John Kindervag and follows the notion of never trust, always verify.
Simply put, nobody is trusted by default in a company that applies the zero trust model. No, not even C-level executives. This is why the concept is linked to technologies such as encryption, multifactor authentication, and privileged access management (PAM).
The contemporary office needs PAM tools to automate the process of escalating admin rights for a limited time for every account that requests them. In lack of a reliable solution for this, system admins will occupy their precious hours with manual approvals and installs.
System admins waste 30% of their time manually managing user
rights or installations
Heimdal® Privileged Access
Management
Is the automatic PAM solution that makes everything
easier.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
The zero trust model is an additional layer of security that is particularly critical for scalability as your company grows. Increasing the number of endpoints within your corporate network and expanding your infrastructure to include cloud and servers is necessary for proper development but poses increasingly difficult challenges as well. Our Privileged Access Management can help with that.
The only solution on the market to provide de-escalation of admin rights when a threat is detected, Heimdal`s Privileged Access Management will allow your sysadmins to streamline the approval process. This will save the entire enterprise a considerable amount of time, money, and resources, as well as increase security and prevent malicious insiders from exploiting your data.
#2 Prevent Privilege Creep on User Accounts
While we’re on the topic of privileged access management, another essential concept to consider when preventing malicious insider threats is privilege creep. The term refers to the accumulation of superfluous access rights, permissions, and privileges by individual users over time. While this might seem harmless, it is actually a serious security threat.
Unfortunately, privilege creep is also quite common in companies that don’t properly control the separation of duties and management of accounts. To combat it, I recommend practicing the principle of least privilege (PoLP), which involves limiting user access to the bare minimum that is necessary for a task to be performed.
#3 Deactivate the Access Rights of Former Employees
Do you know what’s more dangerous than an employee with accumulated access rights to the entire network? A former employee who still has valid login credentials for your company’s system. If you’ll only take away one thing from the malicious insider scenarios I presented above, let it be this: when a staff member leaves your organization or is reassigned, make sure to immediately deactivate their access rights.
In addition to this, you ought to also change any shared passwords or access codes that employee might have known, such as:
- alarm codes,
- Wi-Fi passwords,
- bank account passwords,
- admin account passwords,
- or remote access codes.
#4 Thoroughly Control Data Transfer Procedures
A malicious insider with an agenda to steal your data for their own gain might be furtively trying to transfer files from your network. On the authority of the ACSC, there are two main methods you should consider in this case:
- external storage devices
- outbound emails
Therefore, you should control who can connect removable media disks such as USB sticks to your corporate network, as well as what other types of devices can be connected. Smartphones, tablets, and other Bluetooth/Wi-Fi/3G/4G devices need to be closely monitored.
More modern attackers might resort to sending confidential data to themselves over email. What you can do to prevent this is to first of all block emails that contain passwords or other sensitive keywords. In addition to this, you can also stop the usage of unauthorized cloud computing services such as personal webmail.
#5 Improve the Company Culture as a Whole
At the end of the day, technical controls will only take your cybersecurity so far. To further mitigate the malicious insider threat in your company, you need to also focus on the human factor. Company culture plays a huge role in how employees choose to act on the job. The more you not only promote but practice integrity yourself as a business owner, the harder it will be for staff members to act dishonestly.
Employees that feel happy and valued in their position are far less likely to act out against the company they work for. On top of this, they will also feel more encouraged to practice whistleblowing and help you discover any malicious insider that managed to weasel their way in despite your best efforts.
Wrapping Up…
Regardless of how well-protected you think you are, a malicious insider might be hiding in the midst of your enterprise. To protect your business from unsavory individuals, you should focus on two main aspects: technical controls and the human factor. With the right cybersecurity tools and procedures, as well as a strong company culture based around honesty, you will be able to successfully prevent this from happening to you.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Have you ever dealt with a malicious insider threat in your company? How did you handle the problem? Let me know in the comments below!
Original Post URL: https://heimdalsecurity.com/blog/malicious-insider/
Category & Tags: Access Management,Cybersecurity Basics – Access Management,Cybersecurity Basics
Views: 1





















































