Source: securityaffairs.com – Author: Pierluigi Paganini
Iranian Peach Sandstorm group behind recent password spray attacks
Pierluigi Paganini
September 16, 2023

Iran-linked Peach Sandstorm APT is behind password spray attacks against thousands of organizations globally between February and July 2023.
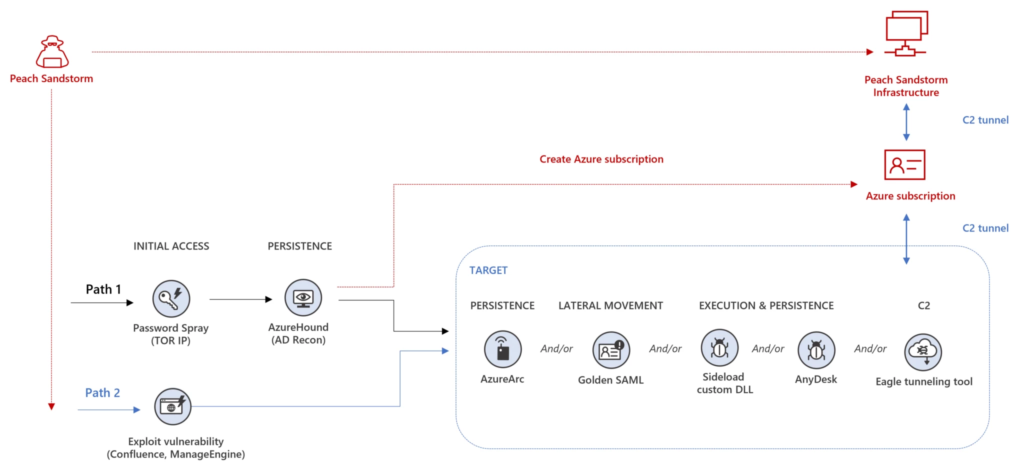
Microsoft researchers observed a series of password spray attacks conducted by Iran nation-state actors as part of a campaign named Peach Sandstorm (aka Holmium, APT33, Elfin, and Magic Hound).
The APT33 group has been around since at least 2013, since mid-2016, the group targeted the aviation industry and energy companies with connections to petrochemical production. Most of the targets were in the Middle East, others were in the U.S., South Korean, and Europe.
The campaign targeted thousands of organizations worldwide between February and July 2023. The cyber espionage activity attacks are aimed at organizations in the satellite, defense, and pharmaceutical sectors.
“Since February 2023, Microsoft has observed password spraying activity against thousands of organizations carried out by an actor we track as Peach Sandstorm (HOLMIUM). Peach Sandstorm is an Iranian nation-state threat actor who has recently pursued organizations in the satellite, defense, and pharmaceutical sectors around the globe.” reads the report published by Microsoft. “Microsoft assesses that this initial access campaign is likely used to facilitate intelligence collection in support of Iranian state interests.”
Password spraying is a type of brute force attack where the attackers carry out brute force logins based on a list of usernames with default passwords on the application. In this attack scenario, threat actors use one password against many different accounts on the application to avoid account lockouts that would normally trigger when brute forcing a single account with many passwords.
Once authenticated to an account, Peach Sandstorm threat actors used publicly available and custom tools to look for information of interest, to maintain persistence, and perform lateral movement. In a limited number of intrusions, the threat actors were observed exfiltrating data from the compromised environment.
The researchers pointed out that unlike password spray operations, which are noisy by definition, the recent post-compromise activity conducted has been stealthy and sophisticated.

Activity observed in late May and June occurred almost exclusively between 9:00 AM and 5:00 PM Iran Standard Time (IRST). The recent password spray campaign was unique, the APT group conducted the attacks from TOR IPs and used a “go-http-client” user agent.
Microsoft observed the group using AzureHound or Roadtools to conduct reconnaissance in Microsoft Entra ID (formerly Azure Active Directory). The attackers used AzureHound to collects data from Microsoft Entra ID and Azure Resource Manager through the Microsoft Graph and Azure REST APIs. The attackers used the Roadtools framework to access Microsoft Entra ID.
The group installed the Azure Arc client on a device in the compromised environment and connected it to an Azure subscription controlled by Peach Sandstorm. Using the tool, threat actors can control devices in a target’s on-premises environment from their cloud.
The Peach Sandstorm APT was also observed attempting to exploit security flaws in Zoho ManageEngine (CVE-2022-47966) and Atlassian Confluence (CVE-2022-26134) to access targets’ environments.
“The capabilities observed in this campaign are concerning as Microsoft saw Peach Sandstorm use legitimate credentials (gleaned from password spray attacks) to authenticate to targets’ systems, persist in targets’ environments, and deploy a range of tools to carry out additional activity.” Microsoft concludes. “Peach Sandstorm also created new Azure subscriptions and leveraged the access these subscriptions provided to conduct additional attacks in other organizations’ environments.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Iran)
Original Post URL: https://securityaffairs.com/150868/intelligence/iranian-peach-sandstorm-password-spray.html
Category & Tags: APT,Breaking News,Cyber warfare,Intelligence,Hacking,hacking news,information security news,Iran,IT Information Security,password spraying,Password Spreay,Peach Sandstorm,Pierluigi Paganini,Security Affairs,Security News – APT,Breaking News,Cyber warfare,Intelligence,Hacking,hacking news,information security news,Iran,IT Information Security,password spraying,Password Spreay,Peach Sandstorm,Pierluigi Paganini,Security Affairs,Security News
Views: 1