Source: heimdalsecurity.com – Author: Bianca Soare
The increase of cybersecurity incidents brings along a higher demand for enhanced security protections. Thus, in the attempt of preventing unauthorized third parties from accessing their accounts and sensitive data, companies are increasingly turning to biometric authentication. Contemporary Identity and Access Management (IAM) technologies have moved beyond basic login methods based on usernames and passwords. Now, IAM systems also include the use of a wide range of biometric features, such as fingerprints, irises, ears, palms, gaits, voices, and even DNA.
The growing popularity of biometrics is projected to build up an industry valued at $68.6 billion by 2025.
However, biometric authentication does carry with it quite a few security challenges and the main reason is obvious: once a biometric characteristic becomes compromised, it can’t be substituted.
For malicious hackers, biometrics and other personal data contained within digital identification and access control systems can be easy prey. And while biometrics are indispensable to a cybersecurity profile, from a privacy perspective, the sensitive details an account holds might well become a nuisance.
In this post, I will provide some tips on how to minimize risks and concerns related to privacy and security when gathering your staff’s personal identifiers, while also enhancing your enterprise’s cybersecurity with the latest biometric techniques.
The definition of biometrics
First, I would like to establish some basics. To begin with, I will briefly outline what biometrics are and list the most common examples of biometric authentication methods.
The International Organization for Standardization (ISO) defines Biometric Recognition (Biometrics) as follows:
“Automated recognition of individuals based on their biological and behavioral characteristics”.
In addition, as per the same source, a Biometric Characteristic is considered to be a:
“Biological and behavioral characteristic of an individual from which distinguishing, repeatable biometric features can be extracted for the purpose of biometric recognition.”
Types of biometrics include:
Chemical
DNA Matching: Identifying individuals through DNA segment analysis.
Visual
Ear: Distinguishing individuals through ear shape analysis.
Iris Recognition: Finding individuals by examining their iris’ features.
Retina Recognition: Analyzing veins in the back of the eye to achieve identification.
Face Recognition: The study of facial features or patterns in order to authenticate or recognize the identity of a person. Eigenfaces or local feature analysis are used by most facial recognition systems.
Visual/Spatial
Fingerprint Recognition: Employing ridges and valleys located on the surface tips of fingers to recognize a person.
Hand Geometry Recognition – Using geometric features of the hand to recognize an individual, such as the length of fingers and the hands’ width.
Finger Geometry Recognition – Conducted through the use of 3D finger geometry to establish one’s identity.
Visual/Behavioral
Signature Recognition: Establishing a person’s identity through the analysis of their handwriting (particularly through their signature) using sophisticated algorithms to validate two scanned signatures.
There are two major forms of handwritten signature authentication: Static and Dynamic.
The visual contrast between a scanned signature and another scanned signature, or a scanned signature versus an ink signature, is most often Static. As ceremony data is collected along with the X, Y, T, and P coordinates from the signing unit, Dynamic is becoming more common.
Behavioral
Gait: Using people’s manner of walking to identify them.
Typing Recognition: Leveraging the use of the exclusive characteristics of a person’s typing for finding his/her identity.
Olfactory
Odor: Using an individual’s scent for discovering his/her identity.
Vein
Vein Recognition: Identifying people based on the vein patterns in their finger or palm.
Auditory
Voice – Speaker Identification – Identification of the speaker is a 1:N (many) match in which the voice is contrasted with N models.
Without the user’s awareness, speaker recognition systems may also be applied to identify speakers in a conversation, notify automated systems of speaker changes, verify if an individual is already engaged in a system, etc.
Voice – Speaker Verification/Authentication: Using a speaker’s voice as a means of finding his/her identity for access control. The voice is used to verify if the speaker’s identity matches the one he/she claims to have. The investigation is conducted through a 1:1 match where the voice of one speaker is checked against a template. To ensure access to a secure system, speaker verification is generally used as a “gatekeeper”.
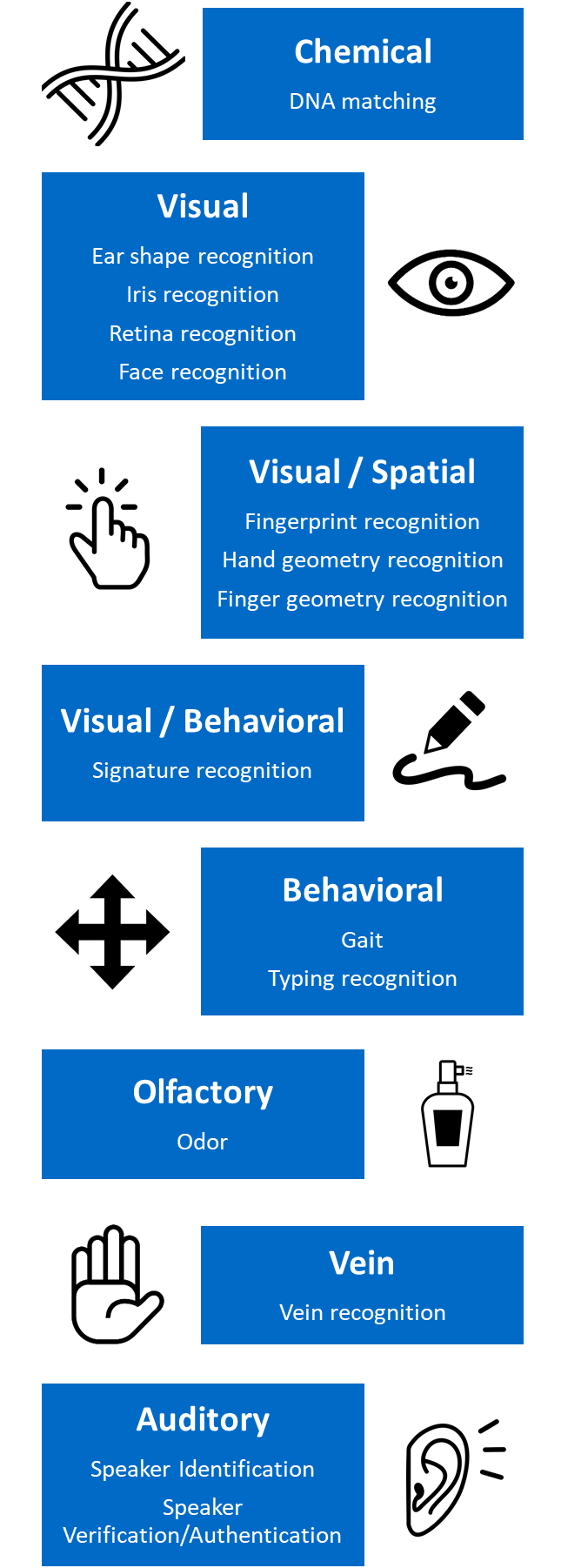
Image based on data provided by the Biometrics Institute
The Security Concerns of IAM-Driven Biometrics
There is an urgent need for new technologies to be introduced in order to build a stable, scalable, and agile IT infrastructure, as the current IAM landscape is becoming difficult to tackle using conventional approaches.
Organizations need to realize that security requirements are shifting at a rapid rate. Therefore, it is important to upgrade existing IAM tools with the latest technologies and functionalities while still maintaining compliance.
But how does one create secure and compliant Identity and Access Management (IAM)?
Solely relying on passwords has certainly become a matter of the past, with today’s IAM systems now also using biometrics and other personal details as credentials. Their purpose is to further secure accounts with the users’ own biometric characteristics. Such changes in IAM are definitely an upgrade from using a standard password, yet they can also jeopardize a company’s network, data, and overall security.
Below I’ve listed the top 3 security issues with biometrics applied within the Identity and Access Management field and tips on how to avoid them and safeguard your organization’s systems and accounts.
#1. Data accessed through IAM systems can be a prime target for malicious actors.
Ironically, the data collected to secure your environment may become exposed and allow for unauthorized access. Thus, it’s imperative to also protect this type of information against both internal and external threats. For example, in 2014, an experiment proved that the fingerprints of Germany’s defense minister could be recreated using only a few high-resolution images of the target. A recent data breach compromised approximately 184,000 traveler images from an agency’s facial recognition pilot at the Anzalduas border crossing at McAllen, Texas.
Thus, as all digital systems can be vulnerable to hacking, this only means that you must never forget about the importance of maintaining good security hygiene: knowing exactly what data you collect, where you store it, periodically removing the information you no longer require, and using proper threat prevention and mitigation tools.
Secondly, be mindful of your privileged accounts. Once an account with elevated rights becomes compromised, it may lead to a wide array of cybersecurity dangers. In this regard, a top-notch Privileged Access Management tool will allow you to easily keep up with your privileged account management, keep a detailed overview of your accounts’ status, and grant admin rights to the users that need them only when they need them.
I also recommend you check out the piece entitled “PAM Security Essentials – Identity Management & Asset Protection” written by my colleague Vladimir to gain some actionable advice on how to strengthen your identity and access governance policies.
System admins waste 30% of their time manually managing user
rights or installations
Heimdal® Privileged Access
Management
Is the automatic PAM solution that makes everything
easier.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
#2. Biometrics in IAM systems may raise ethical concerns.
Although biometrics allow for more accurate identification techniques in IAM, they also raise significant ethical issues as far as the privacy of biometric characteristics is concerned. Some individuals may fear the abuse of biometrics-based surveillance, which can lead to the violation of people’s fundamental rights to privacy and data protection.
When employing biometric authentication, permanently keeping a vigilant eye over who has access to your data, performing privilege revocations upon an employee’s resignation or work transition, and periodic data sorting are highly important.
What’s more, storing personal identifiers using strong encryption methods is also critical.
At the same time, transparency is imperative. Your personnel, partners, and customers must always be aware of the authentication methods your organization is using.
#3. Sensor inaccuracy may open up security holes.
In case of sensor degradation, the consequences may range from the biometric system’s inability to properly identify an individual and deny his/her access to being unable to determine if the real owner of the account is indeed trying to access an IT system. For instance, back in 2018, Israel’s fingerprint identification system experienced “high rates of failure when used both at the country’s borders and by police”.
Consequently, the working state of biometric systems must permanently be kept under watch by their owners and fixed as soon as possible in case of failure. In this instance, alternative authentication methods must be put at people’s disposal.
The benefits of biometrics in IAM
Let’s not forget about the benefits of biometrics, as they have been introduced with the intention of solving security issues (and not creating additional ones), after all.
The main benefits of IAM-driven biometrics are:
- Security. Through the use of biometrics, unauthorized access is almost completely eliminated. A user would actually have to be present if they wanted to gain access to a system using biometrics, as their personal characteristics are truly unique and can’t be forgotten.
- Data privacy. Biometrics guarantee that sensitive data is kept away from unwanted eyes and accessible to your employees only.
- Reliability. Thanks to their non-transferable nature, biometrics are a reliable method of authentication.
- Convenience & Speed. The use of biometrics makes it possible to distinguish the correct person from millions of other people and instantly authenticate them.
Conclusion
Biometric technology – the detection of individuals using biological and behavioral characteristics – has been regarded as an identity identification solution that offers better protection and efficiency than conventional methods.
However, the use of biometrics in IAM is certainly a controversial topic – while trying to secure access, it may also lead to unnecessary threats.
Therefore, the private info needed for IAM technologies must be kept safe and aligned with any industry-specific legislation. It is also important to provide your clients and personnel with complete transparency on how your IAM data will be processed and used, particularly since this practice is required by more and more security regulations.
All in all, make sure you figure out when requiring the use of someone’s unique characteristics doesn’t overstep the mark in security and privacy and always use them responsibly.
If you enjoyed this article, follow us on LinkedIn, Twitter, Facebook, or YouTube to keep up to date with everything we post!
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
What’s your view on IAM-driven biometrics? I would like to read your thoughts in the comments section below!
Original Post URL: https://heimdalsecurity.com/blog/iam-driven-biometrics/
Category & Tags: Access Management,Endpoint security,IAM-driven biometrics – Access Management,Endpoint security,IAM-driven biometrics
Views: 17





















































