Source: www.techrepublic.com – Author: Lance Whitney
Someone who gains physical access to an iPhone or Android phone could use the Phone Link app to spy on the user’s text messages, phone calls and notifications, says Certo.

A Microsoft app that helps people use their Windows PC and iPhone or Android phone in tandem could also be abused by cyberstalkers to snoop on personal information. In a report released Thursday, software maker Certo explains how Microsoft’s Phone Link app could be used against iPhone owners and how they can protect themselves against this type of threat.
Jump to:
- How a cyberstalker could access an iPhone through Phone Link
- What Apple and Microsoft could and should do
- What steps iPhone users should take
How a cyberstalker could access an iPhone through Phone Link
How the Windows Phone Link app works
Windows Phone Link is a free Microsoft app that lets people view and access phone calls, text messages and notifications from their smartphone directly on their Windows 10 or 11 PC. In the past, the app has supported just Android phones, but a recent update from Microsoft allows Windows 11 users to set up Phone Link to work with certain models of iPhones.
Setting up Phone Link requires physical access to the phone and to a Windows computer. The risk here is that a person who’s able to even temporarily grab someone else’s phone could enable Phone Link on their own Windows PC and use the app to spy on the victim’s phone calls and text messages without their knowledge or permission.
Activating Phone Link is a relatively simple process, even with an iPhone. In Windows 11, the person would launch the app and then scan its QR code from their phone to automatically connect and pair the phone and PC. Drilling down into the Bluetooth setting on the phone lets you sync contacts and notifications from the phone with Windows (Figure A).
Figure A
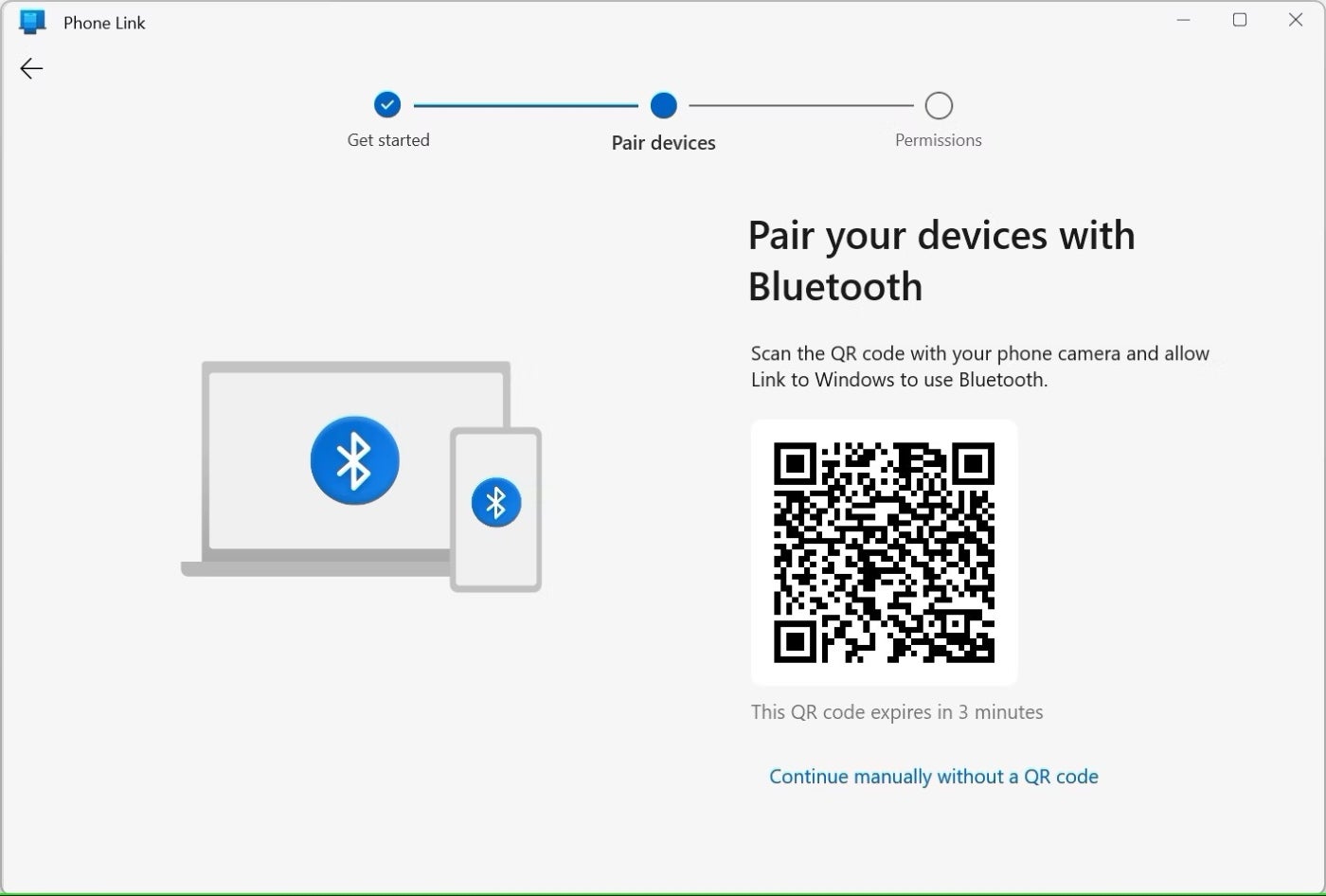
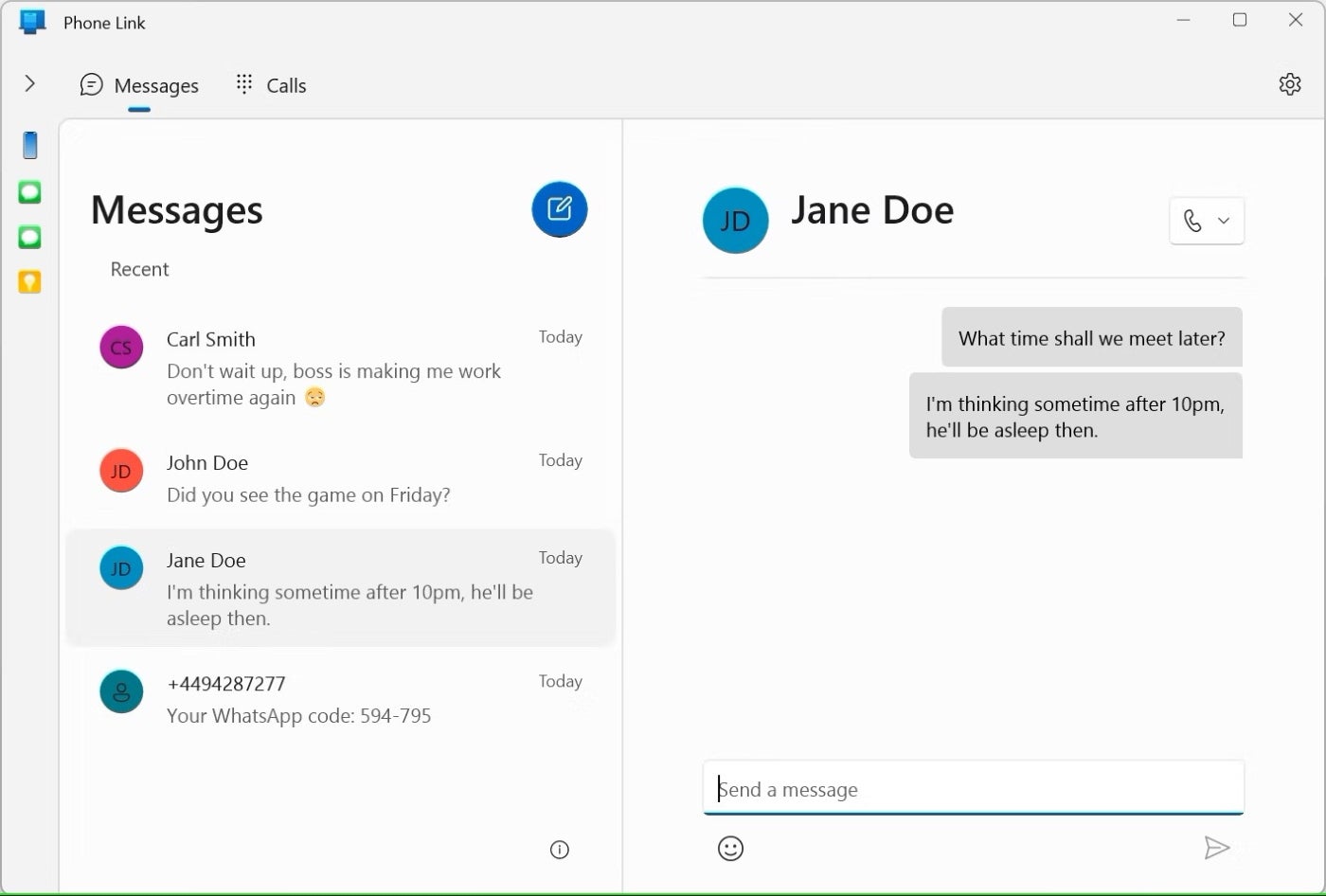
Once the person has set up Phone Link on their own computer and someone else’s phone, they no longer need the phone. But now, they would be able to view sent and received messages, send new messages to contacts, view a history of phone calls, make phone calls, and view all notifications. Beyond accessing personal information, someone could potentially view work information, thereby putting the victim and the victim’s organization at risk (Figure B).
Figure B
How Android phones can be exploited this way
Android phones can also be exploited this way; however, there are a couple of differences between Android and iOS devices.
“This method can also be used against Android phones, and you can see more data from the phone too, for example, Photos,” Certo co-founder Simon Lewis said. “However, it’s much easier to spot on Android for a few reasons. Firstly, the Link to Windows app must be installed from the Play Store. Secondly, a notification is shown on the phone when a connection to a computer is active.”
To be clear, this isn’t a process that could be done remotely — it does require that the person have physical access to the victim’s phone. Therefore, this is not a threat posed by anonymous cybercriminals. Rather, this is more something that a stalker could potentially pull off, meaning a family member, spouse or significant other who wants to spy on someone they know.
What Apple and Microsoft could and should do
Though the Phone Link app for both Windows and iOS is designed to help users, there is this potential for abuse. With that in mind, Certo suggests a couple of steps that both Apple and Microsoft can take to warn users of a potential threat.
With iOS 14 and higher, your iPhone displays a green or orange dot at the top of the screen when your microphone or camera is being used. Apple could develop a similar visual clue that would tell people when notifications or messages are being shared with a Bluetooth-connected device. Microsoft’s options are more limited, but the company could add a warning to the Phone Link app that it should only be used with your own devices and not those of other people.
Note: I contacted Microsoft and Apple for comment, but I did not receive replies from either company prior to publication.
What steps iPhone users should take
Anyone concerned about this potential misuse of the Phone Link app can take steps to protect themselves.
One way is to turn off Bluetooth when you’re not using it. If you do need to keep Bluetooth turned on, check for any unknown devices. To do this on your iPhone, follow these steps:
- Go to Settings and then Bluetooth.
- In the My Devices section, look for any devices you don’t recognize, especially a Windows computer.
- Tap its Info icon to see if the device is set to show notifications or sync contacts.
- Tap the link for Forget This Device to sever the connection.
Another step is to make sure your iPhone is protected with a secure passcode as well as Touch ID or Face ID.
If someone else has added their facial or fingerprint recognition to your phone, and you want to remove that person, you can always reset either option, so only your own face or fingerprint will be recognized and authenticated.
Original Post URL: https://www.techrepublic.com/article/cyberstalkers-iphone-windows-phone-link-app/
Category & Tags: Android,Apple,Microsoft,Mobility,Security,Software,cybersecurity,iphone,mobile security,Windows 11 – Android,Apple,Microsoft,Mobility,Security,Software,cybersecurity,iphone,mobile security,Windows 11
Views: 0




















































