Source: www.bleepingcomputer.com – Author: Ionut Ilascu

Security researchers discovered a multi-step information stealing campaign where hackers breach the systems of hotels, booking sites, and travel agencies and then use their access to go after financial data belonging to customers.
By using this indirect approach and a fake Booking.com payment page, cybercriminals have found a combination that ensures a significantly better success rate at collecting credit card information.
Next-level phishing
Typically, researchers observed info-stealer campaigns that targeted the hospitality industry (e.g. Hotels, travel agencies) using “advanced social engineering techniques” to deliver info-stealing malware.
It starts with a simple query to make a reservation, or it refers to an existing one, researchers at cybersecurity Perception Point say in a report earlier this month.
After establishing communication with the hotel, the criminals invoke a reason, such as a medical condition or a special request for one of the travelers, to send important documents via a URL.
The URL leads to info-stealing malware that “is designed to operate stealthily” and collects sensitive data like credentials or financial info.
In a new report this week, researchers at internet company Akamai say that the attack goes beyond the step described above and moves to target the customers of the compromised entity.
“After the infostealer is executed on the original target (the hotel), the attacker can access messaging with legitimate customers” – Shiran Guez, information security senior manager at Akamai
Having a direct and trusted communication channel with the final victim, cybercriminals can send their phishing message disguised as a legitimate request from the now-compromised hotel, booking service, or travel agency.
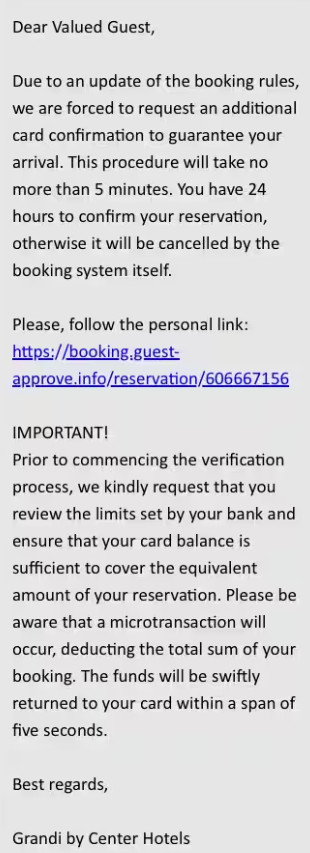
The message asks for an additional credit card verification and relies on the common ingredients of a phishing text: requires immediate action and uses sound rationale to explain it.
Guez notes that the message “is written professionally and modeled after genuine hotel interactions with their guests,” which eliminates all suspicion of a ploy.
source: Akamai
“It is important to remember that this message comes from within the booking site’s message platform itself,” the researcher highlights.
Since the communication comes from the booking site through the official channel, the target has no reason to doubt its legitimacy.
Fake Booking.com page
Guez says that the victim receives a link for the alleged card verification to keep the reservation. The link triggers on the victim machine an executable that is encoded in a complex JavaScript base64 script.
The researcher stresses that the script’s purpose is to detect information about the browsing environment and it is designed to make analysis significantly more difficult.
The attacker also included multiple security validation and anti-analysis techniques to make sure that only potential victims reach the next stage of the scam, which shows a fake Booking.com payment page.
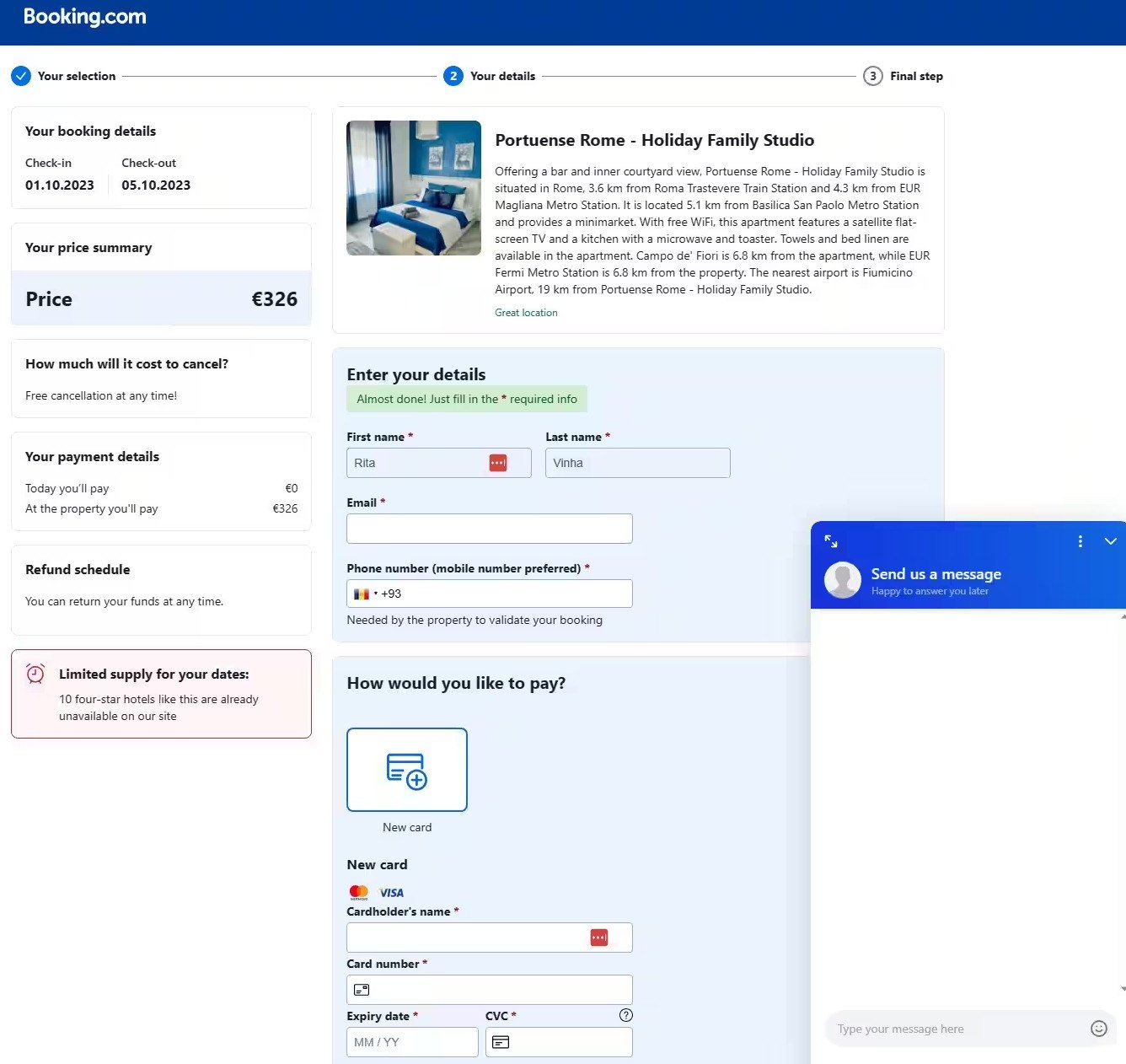
source: Akamai
Despite the more sophisticated approach that makes the trick very difficult to spot, Guez says that the regular signs indicating a potential scam could still reveal the fraud.
Users should avoid clicking on unsolicited links, even if they look legitimate, be suspicious of urgent or threatening messages asking for immediate action, and check URLs for indicators of deception.
However, to ensure you don’t fall victim to more complex phishing campaigns, the recommended action is to contact the company directly at an official email address or phone number and ask for clarifications about the message.
Original Post URL: https://www.bleepingcomputer.com/news/security/hotel-hackers-redirect-guests-to-fake-bookingcom-to-steal-cards/
Category & Tags: Security – Security
Views: 2




















































