Source: www.cybertalk.org – Author: slandau
EXECUTIVE SUMMARY:
More than 270 million people use Microsoft Teams every month, and this isn’t the first time that hackers have attempted to establish persistence through Teams.
Cyber criminals are using Teams to launch remarkably sophisticated phishing attacks. These attacks have affected 40 worldwide enterprises in sectors that include IT services, technology, government and manufacturing.
“This is a highly sophisticated phishing scam that would be almost impossible to detect to the untrained eye,” explained My1Login CEO Mike Newman.
Teams phishing attacks
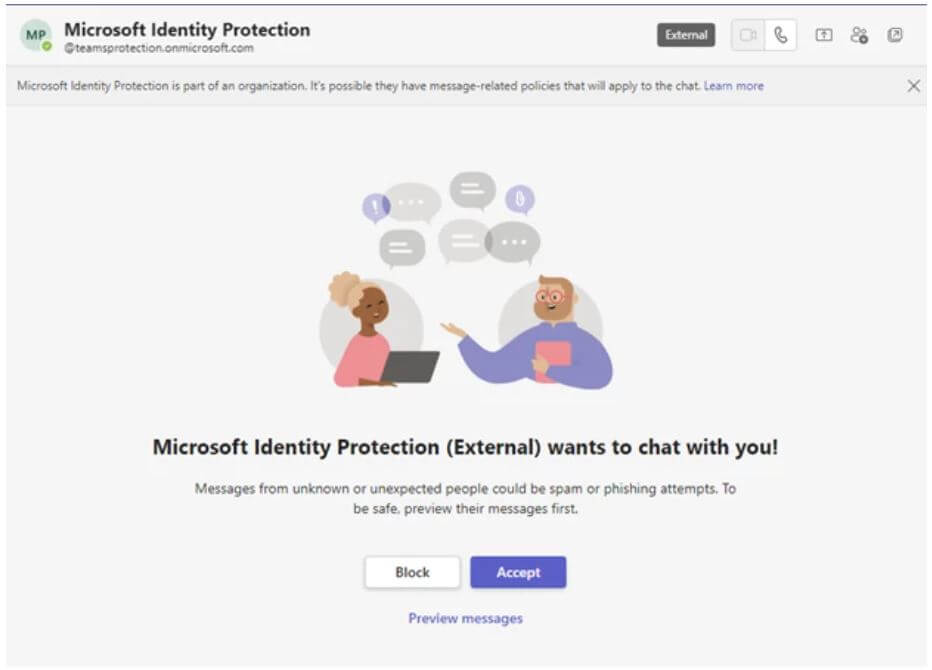
In these attacks, which began in May, cyber criminals leveraged previously compromised Microsoft 365 accounts — that were owned by small businesses — to design new domains that mimicked technical support sites. In simple terms, these cyber criminals posed as technical support groups.
Via domains from the compromised accounts, the cyber criminals weaponized Teams messages, sending lures that attempted to steal credentials from targeted employees who work for unique, global organizations.
Compromising Azure
Once credentials were obtained, the cyber criminals then renamed the compromised accounts, added new users and sent new messages to victims. In many cases, the attackers used security or product name-themed keywords in the subject lines to persuade victims to open the messages.
According to Microsoft, in terms of using compromised domains from small businesses, the threat group has been stopped. However, Microsoft is continuing to investigate the incident and the wider attempt to compromise legitimate Azure tenants.
The cyber criminals primarily attempted to steal information. In some cases, the threat actors tried to add a device to a given organization via Microsoft Entra ID (formerly Azure Active Directory), likely in an attempt to circumnavigate conditional access policies that were configured in order to limit access to specific resources (to managed devices only).
Targeted customers have been notified of the incident.
Attacker information
These attackers are notorious for identifying and implementing novel tactics, techniques and procedures (TTPs) and are believed to have executed the attack against SolarWinds.
The Teams findings emerged just days after phishing attacks targeting diplomatic entities across Eastern Europe were also attributed to the group.
Microsoft tracks the attackers as Midnight Blizzard (previously Nobelium). Other industry analysts know the group as APT29, BlueBravo, Cozy Bear, Iron Hemlock and/or The Dukes. These attackers are believed to work for a nation-state.
How to avoid Teams support scams
- Implement phishing-resistant authentication methods, including multi-factor authentication that supports a zero trust strategy.
- Use conditional access authentication strength for critical applications.
- For Microsoft 365, keep auditing enabled so that audit records can be investigated, if needed.
- On behalf of your organization, understand and select optimal access settings for external collaboration.
- Educate users about social engineering and credential phishing threats and specifically include information about refraining from entering MFA codes sent via any type of unsolicited message.
- Treat authentication requests that were not initiated by the user as malicious.
To learn more about protecting instant messaging channels, like Teams, please see CyberTalk.org’s recent coverage. Lastly, to receive more timely cyber security news, insights and cutting-edge analyses, please sign up for the cybertalk.org newsletter.
Original Post URL: https://www.cybertalk.org/2023/08/09/highly-targeted-phishing-lures-masqueraded-as-legitimate-teams-chats/
Category & Tags: TRENDING NOW,APT29,Azure,Azure Active Directory,Cozy Bear,hackers,Midnight Blizzard,Nobelium,phishing,social engineering,Teams – TRENDING NOW,APT29,Azure,Azure Active Directory,Cozy Bear,hackers,Midnight Blizzard,Nobelium,phishing,social engineering,Teams
Views: 3




















































