Whether network connected or standalone, firmware is the center of controlling any embedded device. As such, it is crucial to understand how firmware can be manipulated to perform unauthorized functions and potentially cripple the supporting ecosystem’s security. To get started with performing security testing and reverse engineering of firmware, use the following Firmware Security Testing Methodology (FSTM) as guidance when embarking on an upcoming assessment. The methodology is composed of nine stages tailored to enable security researchers, software developers, consultants, hobbyists, and Information Security professionals with conducting firmware security assessments.
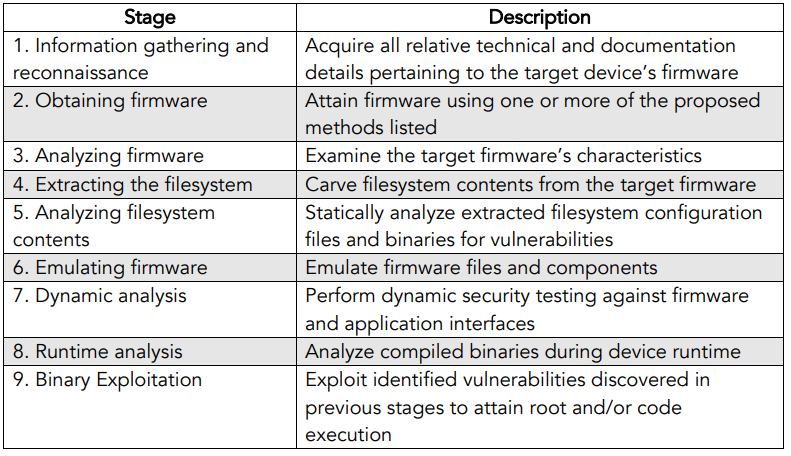
The following sections will further detail each stage with supporting examples where applicable. Consider visiting the OWASP Internet of Things Project wiki page and GitHub repository for the latest methodology updates and forthcoming project
releases.
A preconfigured Ubuntu virtual machine (EmbedOS) with firmware testing tools used throughout this document can be downloaded via the following link. Details regarding EmbedOS’ tools can be found on GitHub within the following repository https://github.com/scriptingxss/EmbedOS.
Views: 17