Source: securityaffairs.com – Author: Pierluigi Paganini
FBI, CISA warn of AndroxGh0st botnet for victim identification and exploitation

U.S. CISA and the FBI warned of AndroxGh0st malware used to create a botnet for victim identification and exploitation in target networks.
US CISA and the Federal Bureau of Investigation (FBI) released a joint Cybersecurity Advisory (CSA) to warn of AndroxGh0st malware. The malware is spreading to create a botnet for victim identification and exploitation in target networks.
The US agencies are sharing known indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with threat actors deploying the Androxgh0st malware.
“Androxgh0st malware establishes a botnet for victim identification and exploitation in vulnerable networks, and targets files that contain confidential information, such as credentials, for various high profile applications.” reads the advisory. “Threat actors deploying Androxgh0st malware have been observed exploiting specific vulnerabilities which could lead to remote code execution”
The Python-based malware AndroxGh0st was first spotted in December 2022 by the cybersecurity firm Lacework.
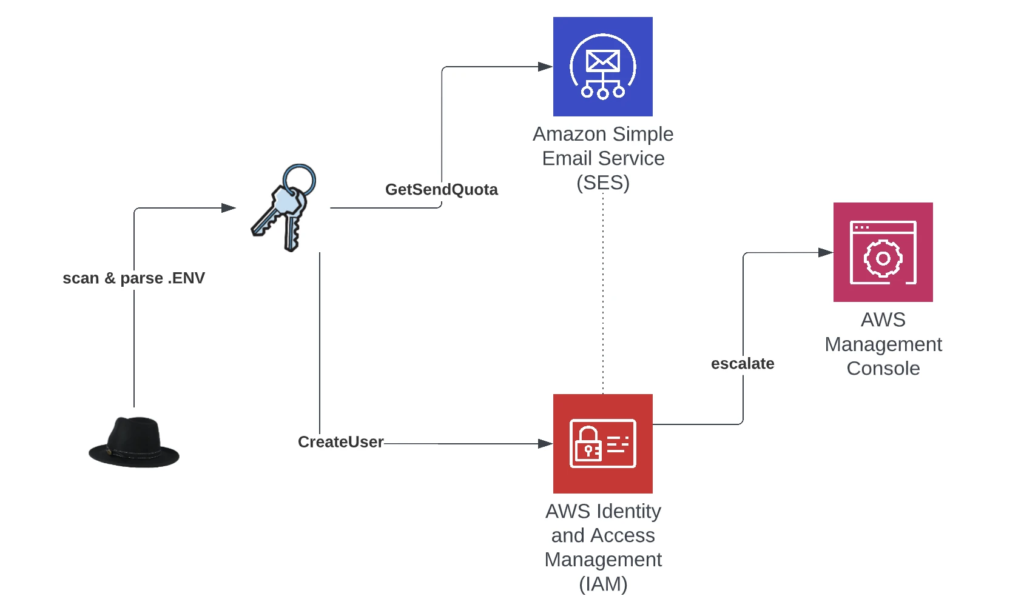
“AndroxGh0st is a “SMTP cracker” which is primarily intended to scan for and parse Laravel application secrets from exposed .env files. Note: Laravel is an open source PHP framework and the Laravel .env file is often targeted for its various configuration data including AWS, SendGrid and Twilio.” reported Lacework.

The malware supports multiple features, including scanning, exploitation of exposed credentials and APIs, and even deployment of webshells. The malware allows operators to scan for and parse AWS keys, but it has also the ability to generate keys for brute-force attacks.
According to the joint Cybersecurity Advisory (CSA), threat actors behind the Androxgh0st malware exploit the following vulnerabilities to achieve remote code execution on target systems:
- CVE-2017-9841 (PHP Unit Command)
- CVE-2021-41773 (Apache HTTP Server versions), and
- CVE-2018-15133 (Laravel applications).
Known Indicators of Compromise Associated with this malware are available here.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
Original Post URL: https://securityaffairs.com/157622/cyber-crime/androxgh0st-botnet-alert.html
Category & Tags: Breaking News,Cyber Crime,Hacking,Malware,Reports,AndroxGh0st,AndroxGh0st malware,botnet,CISA,FBI,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News – Breaking News,Cyber Crime,Hacking,Malware,Reports,AndroxGh0st,AndroxGh0st malware,botnet,CISA,FBI,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News
Views: 0