Source: securityaffairs.com – Author: Pierluigi Paganini.
Legion is an emerging Python-based credential harvester and hacking tool that allows operators to break into various online services.
Cado Labs researchers recently discovered a new Python-based credential harvester and hacking tool, named Legion, which was sold via Telegram. At this time, the sample analyzed by Cado Labs has a low detection rate of 0 on VirusTotal.
Legion is a modular tool that can be used by crooks to hack into various online services. The researchers reported that the tool has modules to support the following functionalities:
- enumerating vulnerable SMTP servers,
- conducting Remote Code Execution (RCE),
- exploiting vulnerable versions of Apache,
- brute-forcing cPanel and WebHost Manager (WHM) accounts,
- interacting with Shodan’s API to retrieve a target list (providing you supply an API key) and
- additional utilities, many of which involve abusing AWS services
Legion is similar to a tool detailed in December by Lacework researchers, which was named AndroxGh0st.
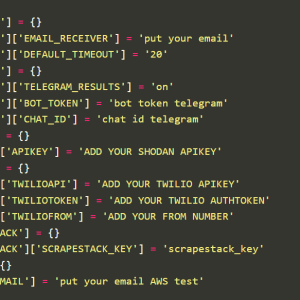
The sample analyzed by Cado Labs is a Python3 script of 21015 lines, it includes configurations for integrating with services such as Twilio and Shodan.
The malware can exfiltrate collected data via Telegram chat using the Telegram Bot API.
The developer behind the tool operates a YouTube channel named “Forza Tools”, which included a series of tutorial videos for using the Legion script. The experts believe that the tool is widely distributed and is likely paid malware.
Legion exploits web servers running Content Management Systems (CMS), PHP, or PHP-based frameworks such as Laravel.
“From these targeted servers, the tool uses a number of RegEx patterns to extract credentials for various web services. These include credentials for email providers, cloud service providers (AWS), server management systems, databases and payment systems – such as Stripe and PayPal. Typically, this type of tool would be used to hijack said services and use the infrastructure for mass spamming or opportunistic phishing campaigns.” reads the analysis published by Cado Labs.
The tools can also be used to implant webshells, perform brute-force attacks on CPanel or AWS accounts and send SMS messages to a list of dynamically-generated US mobile numbers.
Below is the list of the services the malware attempts to extract credentials:
| Services Targeted |
| Twilio |
| Nexmo |
| Stripe/Paypal (payment API function) |
| AWS console credentials |
| AWS SNS, S3 and SES specific credentials |
| Mailgun |
| Plivo |
| Clicksend |
| Mandrill |
| Mailjet |
| MessageBird |
| Vonage |
| Nexmo |
| Exotel |
| Onesignal |
| Clickatel |
| Tokbox |
| SMTP credentials |
| Database Administration and CMS credentials (CPanel, WHM, PHPmyadmin) |
When used to target insecure or misconfigured web servers, Legion attempts to retrieve AWS credentials and sends out SMS spam messages to users of U.S. mobile carriers such as AT&T, Sprint, T-Mobile, SunCom, US Cellular, Verizon, and Virgin.
The tool is able to deliver SMS spam messages to users of mobile networks in the United States. The malware retrieves the area code for a US state of the user’s choosing from the website www.randomphonenumbers.com.
“Since this malware relies heavily on misconfigurations in web server technologies and frameworks such as Laravel, it’s recommended that users of these technologies review their existing security processes and ensure that secrets are appropriately stored. Ideally, if credentials are to be stored in a .env file, this should be stored outside web server directories so that it’s inaccessible from the web.” concludes the report that also provides Indicators of Compromise (IoCs). “AWS users should be aware of Legion’s targeting of IAM and services such as SES.”
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections:
- The Teacher – Most Educational Blog
- The Entertainer – Most Entertaining Blog
- The Tech Whizz – Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Legion)
Original Post URL: https://securityaffairs.com/144888/hacking/legion-python-tool-credential-harvester.html
Category & Tags: Breaking News,Hacking,cloud computing,Cybercrime,hacking news,information security news,IT Information Security,Legion hacking tool,Pierluigi Paganini,Security Affairs,Security News,Telegram – Breaking News,Hacking,cloud computing,Cybercrime,hacking news,information security news,IT Information Security,Legion hacking tool,Pierluigi Paganini,Security Affairs,Security News,Telegram
Views: 2