Source: securityaffairs.com – Author: Pierluigi Paganini
Don’t trust links with known domains: BMW affected by redirect vulnerability

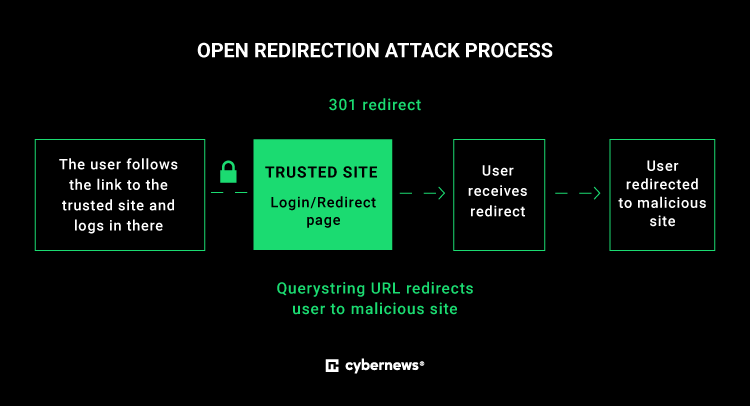
Sometimes, you can’t even trust links with your own domain. As the Cybernews research team has discovered, some BMW subdomains were vulnerable to redirect vulnerability, enabling attackers to forge links leading to malicious sites through them.
Cybernews researchers have discovered two BMW subdomains that were vulnerable to SAP redirect vulnerability. They were used to access the internal workplace systems for BMW dealers and could have been useful to attackers for spear-phishing campaigns or malware distribution.
SAP redirect vulnerability is a security issue that affects web application servers for SAP products (SAP NetWeaver Application Server Java). This means that anyone could forge a redirect link using these subdomains by adding a string such as this:
“sap/public/bc/icf/logoff?redirecturl=https://maliciouswebsite.com”
The final URL would look like this:
“https://<…>.bmw.com/sap/public/bc/icf/logoff?redirecturl=https://maliciouswebsite.com”
“It allows an attacker to redirect a user to a malicious website or inject arbitrary content into a legitimate website. This can be done by manipulating the URL parameters of the affected SAP system,” Cybernews researchers explained.
While not critical, such a vulnerability opens many creative opportunities for phishers, targeting employees or customers.
“Imagine you get an email from your CEO or manager asking you to do something. The firewall won’t block the malicious link in an email as the domain is legitimate. If you open the link and enter your credentials, attackers suddenly gain access to deploy ransomware or for other deeds. This exploit could also be used for mass phishing campaigns, targeting customers,” our researchers said.
Attackers exploit this vulnerability in the wild to steal sensitive information, such as login credentials, or to spread malware to unsuspecting users. When the victim clicks on a link that appears to be legitimate, they’re redirected to the attacker’s website, where malicious JavaScript is executed in the client’s browser or where they are prompted to enter sensitive information.
BMW fixes the vulnerability
Cybernews researchers immediately disclosed the vulnerability to BMW, and it was promptly fixed.
A BMW spokesperson assured us that information security is a top priority for the BMW Group, which applies to the company’s employees, customers, and business partners.
“After we identified the vulnerability, we acted to assess it and put the necessary actions in place to minimize a possible impact. As far as we know, the addressed vulnerability didn’t compromise BMW Group-related systems, nor was any data leaked or misused,” the spokesperson said.
They also explained that the BMW Group uses multi-level security controls when accessing internal systems, according to the principle: the more sensitive the data, the higher the security measures.
BMW is a German manufacturer of luxury vehicles headquartered in Munich.
How the redirect attacks work and how to avoid them
An SAP Redirect vulnerability and similar vulnerabilities usually cause web applications to redirect users to specified URLs. Those typically occur when web apps or components fail to properly validate or sanitize URLs before redirecting users.
This type of vulnerability, which affected BMW websites and other SAP systems, was first identified in 2012 but still poses risks to organizations even after applying security updates.
All attackers need to do is modify the URL value to redirect to a malicious site.

“Because the server name in the modified link is identical to the original site, phishing attempts have a more trustworthy appearance,” MITRE’s definition of the common weakness reads. “Whether this issue poses a vulnerability will be subject to the intended behavior of the application. For example, a search engine might intentionally provide redirects to arbitrary URLs.”
To know how to address an SAP redirect vulnerability take a look at the original post published by Cybernews researchers:
https://cybernews.com/security/bmw-affected-by-redirect-vulnerability-research/
About the author: Ernestas Naprys, Senior Journalist at CyberNews
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, cybercrime)
Original Post URL: https://securityaffairs.com/156843/reports/bmw-affected-by-redirect-vulnerability.html
Category & Tags: Breaking News,Reports,BMW,Hacking,hacking news,information security news,IT Information Security,Pierluigi Paganini,redirect vulnerability,Security Affairs,Security News – Breaking News,Reports,BMW,Hacking,hacking news,information security news,IT Information Security,Pierluigi Paganini,redirect vulnerability,Security Affairs,Security News
Views: 0