Source: securityaffairs.com – Author: Pierluigi Paganini
Deadglyph, a very sophisticated and unknown backdoor targets the Middle East
Pierluigi Paganini
September 24, 2023

Researchers discovered a previously undocumented sophisticated backdoor, named Deadglyph, used by the Stealth Falcon group for espionage in the Middle East
ESET researchers discovered a very sophisticated and unknown backdoor, named Deadglyph, employed by the Stealth Falcon group for espionage in the Middle East.
Stealth Falcon is a nation-state actor active since at least 2012, the group targeted political activists and journalists in the Middle East in past campaigns. In 2016, researchers from the non-profit organization CitizenLab published a report that describes a campaign of targeted spyware attacks carried out by the Stealth Falcon. The attacks have been conducted from 2012 until 2106, against Emirati journalists, activists, and dissidents.
In January 2019, Reuters published a report into Project Raven, a campaign allegedly conducted by former NSA operatives and aiming at the same types of targets as Stealth Falcon.
The name Deadglyph comes from artifacts found in the backdoor (such as 0xDEADB001) and the presence of a homoglyph attack.
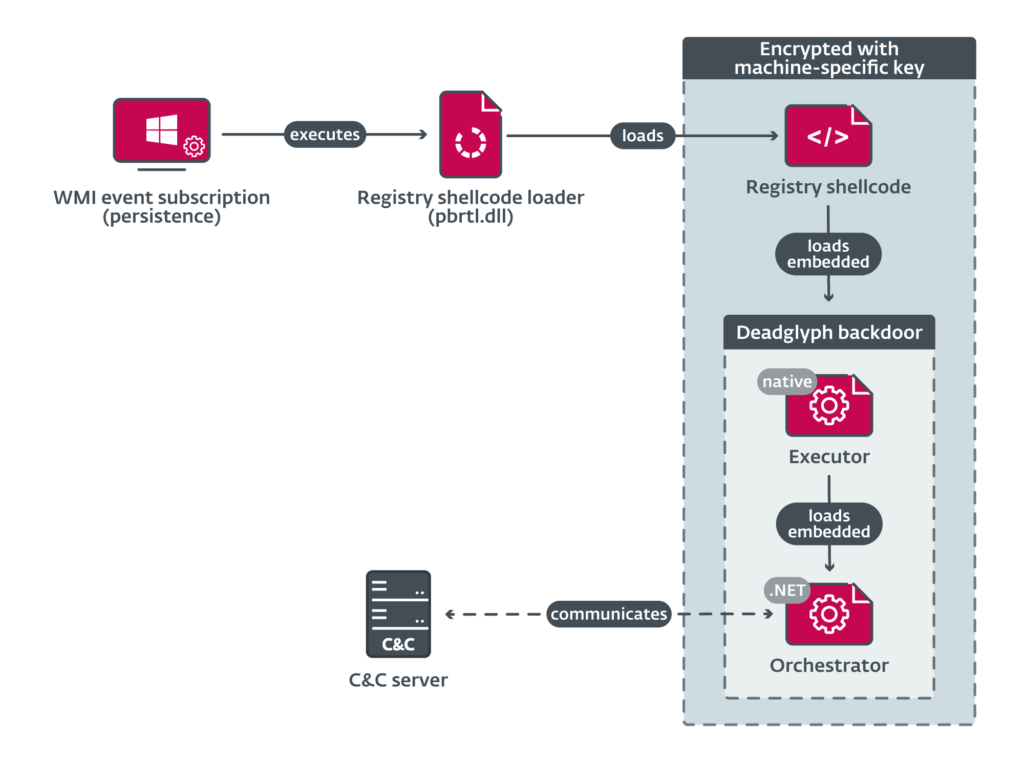
The Deadglyph’s architecture is composed of cooperating components, a native x64 binary and other .NET assembly.
The researchers explained that unlike other malware typically using components written in only one programming language, Deadglyph uses distinct programming languages.
The authors used different languages to hinder analysis, researchers explained.
Unlike other backdoors that receive commands implemented in their binary, Deadglyph dynamically received the commands from the C2 in the form of additional modules. The malware also supports multiple evasion capabilities.
ESET analyzed a successful attack on a governmental entity in the Middle East, but they also discovered on VirusTotal a sample of the same malware that was uploaded from Qatar.
The researchers have yet to determine the exact method used to deliver the backdoor.
“The initial component is a registry shellcode loader, which loads shellcode from the registry. This extracted shellcode, in turn, loads the native x64 part of the backdoor – the Executor. The Executor subsequently loads the .NET part of the backdoor – the Orchestrator.” reads the analysis published by ESET. “Notably, the only component on system’s disk as a file is the initial component, which is in the form of a Dynamic Link Library (DLL). The remaining components are encrypted and stored within a binary registry value.”
The Orchestrator accepts commands from the C2 in the form of tasks, then the malicious code organizes them into three categories: orchestrator tasks, executor tasks, and upload tasks.
Orchestrator tasks are used to manage the configuration of the Network and Timer modules, and also to cancel pending tasks. Executor tasks are used to manage the backdoor and execute additional modules.
Upload tasks are used to upload the output of commands and errors.
While investigating Deadglyph, the researchers discovered a control panel (CPL) file signed with an expired certificate, The file was uploaded to VirusTotal from Qatar and acted as a multistage shellcode downloader. The researchers noticed code similarities with Deadglyph.
The shellcode retrieved from the C2 likely acts as the installer for Deadglyph.
“Notably, Deadglyph boasts a range of counter-detection mechanisms, including continuous monitoring of system processes and the implementation of randomized network patterns. Furthermore, the backdoor is capable of uninstalling itself to minimize the likelihood of its detection in certain cases.” concludes the report.
“Additionally, our investigation led us to the discovery of a compelling multistage shellcode downloader chain on VirusTotal.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Deadglyph)
Original Post URL: https://securityaffairs.com/151298/malware/deadglyph-backdoor-middle-east.html
Category & Tags: Breaking News,Hacking,Intelligence,Malware,Deadglyph,hacking news,information security news,IT Information Security,malware,Middle East,Pierluigi Paganini,Security Affairs,Stealth Falcon – Breaking News,Hacking,Intelligence,Malware,Deadglyph,hacking news,information security news,IT Information Security,malware,Middle East,Pierluigi Paganini,Security Affairs,Stealth Falcon
Views: 0