This Guide presents details about how to monitor and log cyber security events, some of which are potential indicators
of compromise (IOC) that can lead to cyber security incidents if not addressed quickly and effectively. The Guide provides
you with practical advice on how to manage logs effectively, deal with suspicious events, use cyber security intelligence
and address challenges. It is designed to enable you to prioritise and manage myriad event logs; build an effective cyber
security monitoring process and learn about where and how you can get help.
The Guide provides advice and guidance on how to:
- Identify potential indicators of compromise (IOC) at an early stage;
- Investigate them effectively; and
- Take appropriate action to reduce the frequency and impact of cyber security incidents.
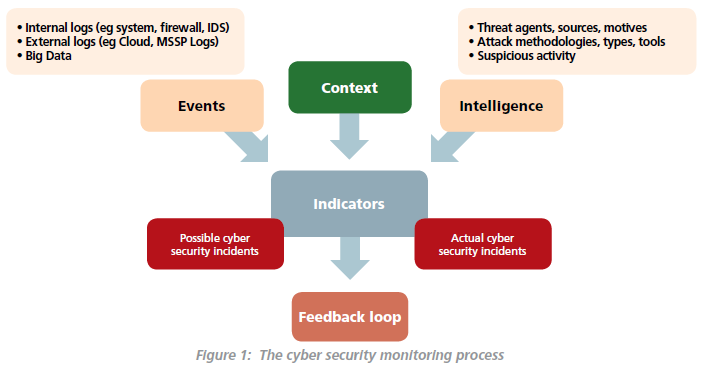
The focus of the Guide is on the overall cyber security monitoring process, supported by analysis of cyber security-related
events (typically generated from one or more logs) and cyber threat intelligence, bringing context to the process, as shown
in Figure 1 below.
The Guide then explores the benefits of using cyber security experts from commercial suppliers and run Security Operations
Centres – a key emerging trend. It also introduces a systematic, structured process that can help you select an appropriate
supplier(s) to meet your requirements.
Views: 18




















































