Source: securityaffairs.com – Author: Pierluigi Paganini.
China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization.
Google Threat Analysis Group (TAG) team reported that the China-linked APT41 group used the open-source red teaming tool Google Command and Control (GC2) in an attack against an unnamed Taiwanese media organization.
The APT41 group, aka Winnti, Axiom, Barium, Blackfly, HOODOO) is a China-linked cyberespionage group that has been active since at least 2007.
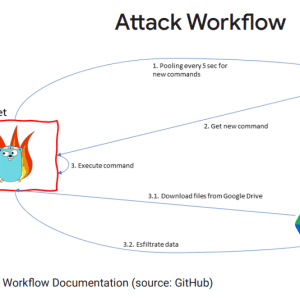
The attack took place in October 2022, threat actors sent phishing emails that contained links to a password-protected file hosted in Drive. The final payload was the Go-written GC2 tool that gets commands from Google Sheets and exfiltrates data to Google Drive.
“In October 2022, Google’s Threat Analysis Group (TAG) disrupted a campaign from HOODOO, a Chinese government-backed attacker also known as APT41, that targeted a Taiwanese media organization by sending phishing emails that contained links to a passwordprotected file hosted in Drive.” reads the Threat Horizons April 2023 Threat Horizons Report published by Google.”The payload was an open source red teaming tool called “Google Command and Control” (GC2).”
Upon installing the malware on the target system, it queries Google Sheets to obtain attacker commands. GC2 also allows operators to download additional files from Drive onto the victim system.

Google TAG experts pointed out that the Chinese group previously used GC2 in July 2022 in an attack aimed at an Italian job search website
These incidents highlighted a few key threat trends by China-affiliated threat actors. First, as opposed to developing their own custom tools, Chinese APT groups are increasingly using publicly available tooling such as Cobalt Strike and other “pentest” software available for purchase or on sites like Github. HOODOO’s use of GC2 is an example of this trend. Second, the proliferation of tools written in the Go programming language has continued to expand, likely due to the flexibility of the Go language and its convenience for adding and removing module components. Finally, the targeting of Taiwanese media illustrates the continued overlap of public sector threat actors targeting private sector organizations with limited government ties.
The researchers highlighted some key threat trends by China-linked APT groups. First, Chinese threat actors are increasingly using publicly available tooling such as GC2 and. Second, the proliferation of tools written in the Go programming language due to the flexibility of the language that allows to develop cross-platform software. Finally, the attack against the Taiwanese media shows that attackers are also targeting private sector organizations with limited government ties.
The development is notable for two reasons: First, it suggests that Chinese threat groups are increasingly relying on publicly available tooling like Cobalt Strike and GC2 to confuse attribution efforts.
Secondly, it also points to the growing adoption of malware and tools written in the Go programming language, owing to its cross-platform compatibility and its modular nature.
The report also states that cloud services are becoming a privileged target also for nation-state actor and urges organizations to improve enterprise defenses.
“Cloud providers are useful targets for these kind of operations, either as hosts for malware or providing the infrastructure for command-and-control (C2).” continues the report.
The researchers noticed that the most common attack against networks and cloud instances is the account takeover.
“Access to service account credentials can also allow attackers to span across services such as when a GCP
service account is granted domain wide delegation authority to an organization’s Google Workspace
environment.” concludes the report that also includes mitigations.
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections:
- The Teacher – Most Educational Blog
- The Entertainer – Most Entertaining Blog
- The Tech Whizz – Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, APT41)
Original Post URL: https://securityaffairs.com/144915/apt/china-apt41-tool-gc2.html
Category & Tags: APT,Breaking News,Cyber warfare,Hacking,Malware,APT41,Cyberespionage,GC2 tool,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News – APT,Breaking News,Cyber warfare,Hacking,Malware,APT41,Cyberespionage,GC2 tool,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News
Views: 1