Source: securityaffairs.com – Author: Pierluigi Paganini
China-linked APT BlackTech was spotted hiding in Cisco router firmware
Pierluigi Paganini
September 27, 2023

US and Japanese authorities warn that a China-linked APT BlackTech planted backdoor in Cisco router firmware to hack the businesses in both countries.
US and Japanese intelligence, law enforcement and cybersecurity agencies warn of a China-linked APT, tracked as BlackTech (aka Palmerworm, Temp.Overboard, Circuit Panda, and Radio Panda), that planted backdoor in Cisco router firmware to access multinational companies’ networks.
BlackTech is a Chinese APT group that has been active since at least 2010 and that known for conducting cyber espionage campaigns in Asia aimed at entities in Hong Kong, Japan, and Taiwan.
The group targeted organizations in multiple sectors, including defense, government, electronics, telecommunication, technology, media, telecommunication industries.
According to a joint cybersecurity advisory from the United States National Security Agency (NSA), the U.S. Federal Bureau of Investigation (FBI), the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Japan National Police Agency (NPA), and the Japan National Center of Incident Readiness and Strategy for Cybersecurity (NISC), BlackTech has been observed modifying the firmware of Cisco routers to maintain stealthy persistence and pivoting from international subsidiaries to headquarters in Japan and the United States.
“BlackTech actors exploit trusted network relationships between an established victim and other entities to expand their access in target networks.” reads the joint advisory. “Specifically, upon gaining an initial foothold into a target network and gaining administrator access to network edge devices, BlackTech cyber actors often modify the firmware to hide their activity across the edge devices to further maintain persistence in the network.”
The Chinese APT group targets branch routers, usually smaller appliances used at remote branch offices to connect to a corporate headquarters, used them to pivot to corporate networks.
The state-sponsored hackers was observed using a custom firmware backdoor which was enabled and disabled by sending specially crafted TCP or UDP packets to the devices. The experts pointed out that this TTP is not solely limited to Cisco routers, and similar techniques could be used to enable backdoors in other network equipment.
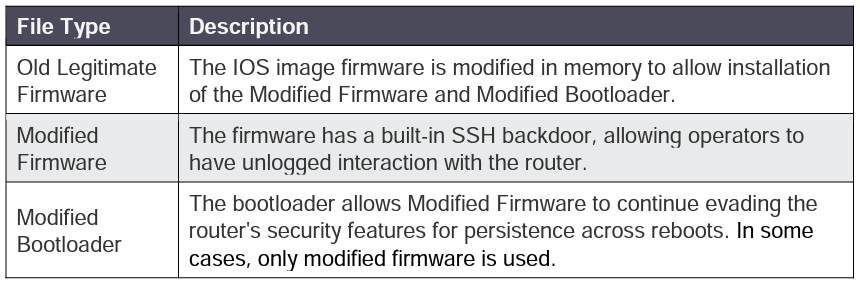
The threat actors utilize the following file types to compromise the router:

BlackTech also uses dual-use tools, and living off the land tactics, such as disabling logging on routers, to conceal their operations.
The nation-state actors employed multiple custom malware families targeting Windows, Linux, and FreeBSD operating systems. Custom malware families used by the group include BendyBear, Bifrose, BTSDoor, FakeDead (a.k.a. TSCookie), FlagPro, FrontShell (FakeDead’s downloader module), IconDown, PLEAD, SpiderPig, SpiderSpring, SpiderStack, WaterBear. The government experts state that the Chinese APT group continuously updates the tools in its arsenal to evade detection. In some cases the group signed its malicious code with stolen certificates to evade defenses.
The attacker use RDP to move laterally across a victim’s network and disable logging on the compromised routers to prevent logging of any commands issued.
“The modified firmware uses a built-in SSH backdoor, allowing BlackTech actors to maintain access to the compromised router without BlackTech connections being logged. BlackTech actors bypass the router’s built-in security features by first installing older legitimate firmware that they then modify in memory to allow the installation of a modified, unsigned bootloader and modified, unsigned firmware.” continues the advisory. “The modified bootloader enables the modified firmware to continue evading detection [T1553.006], however, it is not always necessary.”
BlackTech threat actors have hidden their activities and obscured changes made to compromised Cisco routers by concealing Embedded Event Manager (EEM) policies. EEM policies are typically employed in Cisco IOS to automate tasks triggered by specific events, including those that manipulate the Cisco IOS Command-Line Interface (CLI) command outputs.
The advisory also includes recommendations for system administrators to prevent the installation of backdoor firmware images and unusual device reboots.
Cisco attempted to reassure its customers explaining that BlackTech did not exploit any vulnerabilities in its products and that the attack technique described in the advisory only works against older products
Cisco would like to highlight the following key facts:
- The most prevalent initial access vector in these attacks involves stolen or weak administrative credentials. As outlined in the report, certain configuration changes, such as disabling logging and downloading firmware, require administrative credentials.
- There is no indication that any Cisco vulnerabilities were exploited. Attackers used compromised credentials to perform administrative-level configuration and software changes.
- Modern Cisco devices include secure boot capabilities, which do not allow the loading and executing of modified software images. For more information on secure boot, see the Cisco Trustworthy Technologies Data Sheet.
- The stolen code-signing certificates mentioned in the report are not from Cisco. Cisco does not have any knowledge of code-signing certificates being stolen to perform any attack against Cisco infrastructure devices.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, APT)
Original Post URL: https://securityaffairs.com/151587/apt/blacktech-backdoor-cisco-router-firmware.html
Category & Tags: APT,Breaking News,Cyber warfare,Hacking,Malware,backdoor,BlackTech,China,Cisco routers,Firmware,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News – APT,Breaking News,Cyber warfare,Hacking,Malware,backdoor,BlackTech,China,Cisco routers,Firmware,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News
Views: 3