Source: securityaffairs.com – Author: Pierluigi Paganini
Ukraine’s CERT-UA warns of an ongoing phishing campaign aimed at distributing the SmokeLoader malware in the form of a polyglot file.
CERT-UA warns of an ongoing phishing campaign that is distributing the SmokeLoader malware in the form of a polyglot file.
Threat actors are using emails sent from compromised accounts with the subject “bill/payment” with an attachment in the form of a ZIP archive.
The JavaScript employed in the attack uses a PowerShell to download and execute an executable used to launch the SmokeLoader malware.
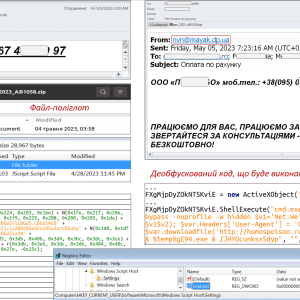
“The mentioned ZIP archive is a polyglot file containing a decoy document and a JavaScript file “pax_2023_AB1058..js” which, using PowerShell, will cause the executable file “portable.exe” to be downloaded and run. The latter, in turn, will launch the SmokeLoader malware (compilation date: 2023-04-24 11:45:17).” reads the alert published by Ukraine’s CERT.
The analysis of the domain name registration dates and the file compilation date suggests the campaign was launched in April 2023.
SmokeLoader acts as a loader for other malware, once it is executed it will inject malicious code into the currently running explorer process (explorer.exe) and downloads another payload to the system.
CERT-UA attributed the campaign to the financially motivated threat actor UAC-0006 which has been active since at least 2013. The threat actors focus on compromising accountants’ PCs (which are used to support financial activities, such as access to remote banking systems), stealing credentials, and making unauthorized fund transfers.
The CERT-UA pointed out that JavaScript loaders are typically used by this threat actor in the initial stage of an attack, for this reason, it recommends blocking the launch of wscript.exe (Windows Script Host) on the PC to temporarily minimize the probability of attack
“For this, in particular, in the registry branch “{HKEY_CURRENT_USER,HKEY_LOCAL_MACHINE}SoftwareMicrosoftWindows Script HostSettings” you need to add the entry “Enabled” (type: DWORD) with the value “0”. ” concludes the alert published by CERT.
The alert includes the Indicators of Compromise (IoCs).
A few days ago, CERT-UA warned of destructive cyberattacks conducted by the Russia-linked Sandworm APT group against the Ukraine public sector. The threat actors allegedly obtained access to Ukraine’s public networks by using compromised VPN credentials.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections where is reported Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, CERT-UA)
Original Post URL: https://securityaffairs.com/145911/malware/cert-ua-smokeloader-campaign.html
Category & Tags: Breaking News,Malware,CERT-UA,Cybercrime,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News,SmokeLoader – Breaking News,Malware,CERT-UA,Cybercrime,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News,SmokeLoader
Views: 18