Researchers have discovered a previously undocumented Android dropper, dubbed BugDrop, that’s still under development.
Recently, researchers from ThreatFabric discovered a previously undetected Android dropper, dubbed BugDrop, which is under active development and was designed to bypass security features that will be implemented in the next release of the Google OS.
The experts noticed something unusual in the latest sample of the malware family Xenomorph, it was an improved version of the threat that included RAT capabilities by using “Runtime modules”. The Runtime modules allow the malware to perform gestures, touches, and other operations.
The new version of Xenomorph was dropped by the BugDrop malware which is able to defeat security measures that Google will introduce to prevent malware requesting Accessibility Services privileges from victims.
The dropper was developed by a cybercriminal group known as Hadoken Security, which is the same threat actor that is behind Xenomorph and Gymdrop Android malware.
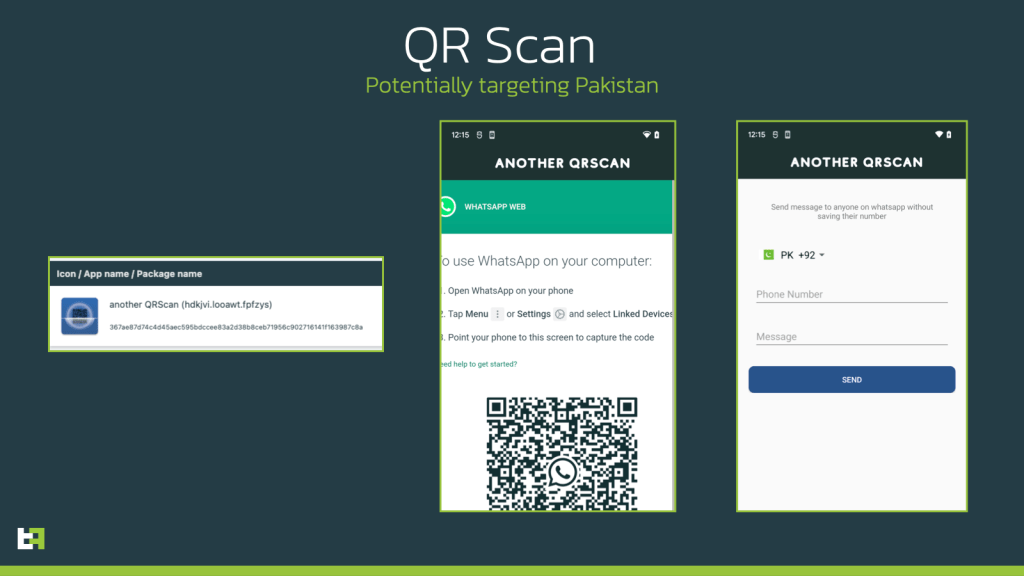
The malicious application spotted by the researchers poses as a QR code reader.
Upon launching the application it will request the Accessibility Services access to the user to perform gestures and touches on behalf of the victim.
“Once granted, while showing a loading screen, the dropper initiates a connection with its onion.ws C2, which relies on the TOR protocol, obtaining back its configuration and the URL of the payload to download and install.” reads the analysis of the experts. “Throughout the course of our investigation, this URL changed from being one of the samples in the open folder, to an external URL again referring to QR code scanners functionalities, which used a endpoint very similar to what was used by Gymdrop samples that we observed in the wild in the last few months.”
The presence of instructions in the dropper code to send error messages back to the C2 suggests it is still under development.
The experts noticed that starting with Android 13, Google is blocking accessibility API access to apps installed from outside of the official app store.
However, BugDrop, attempts to bypass this security measure by deploying malicious payloads via a session-based installation process.
“In this context, it is important to remind the new security features of Android 13, which will be released in fall of 2022. With this new release, Google introduced the “restricted setting” feauture, which blocks sideloaded applications from requesting Accessibility Services privileges, limiting this kind of request to applications installed with a session-based API (which is the method usually used by app stores).” states the analysis. “With this in mind, it is clear what criminals are trying to achieve. What is likely happening is that actors are using an already built malware, capable of installing new APKs on an infected device, to test a session based installation method, which would then later be incorporated in a more elaborate and refined dropper.”
Upon completing the development of the new features, BugDrop will give attackers new capabilities to target banking institutions and bypass security solutions currently being adopted by Google.
Follow me on Twitter: @securityaffairs and Facebook
(SecurityAffairs – hacking, BugDrop)
The post Bugdrop dropper includes features to circumvent Google’s security Controls appeared first on Security Affairs.
Leer másSecurity Affairs
Views: 1