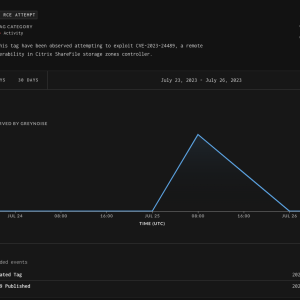
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added critical vulnerability CVE-2023-24489 in Citrix ShareFile to its Known Exploited Vulnerabilities catalog. US Cybersecurity and Infrastructure Security...
Author:
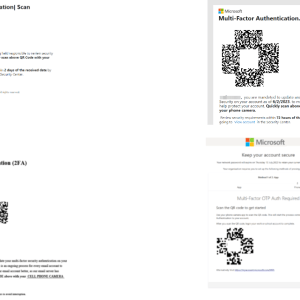
A massive phishing campaign using QR codes targets the energy sector – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A phishing campaign employing QR codes targeted a leading energy company in the US, cybersecurity firm Cofense reported. Starting from...
Two unauthenticated stack buffer overflows found in Ivanti Avalanche EMM – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ivanti Avalanche EMM product is impacted by two buffer overflows collectively tracked as CVE-2023-32560. Tenable researchers discovered two stack-based buffer overflows,...
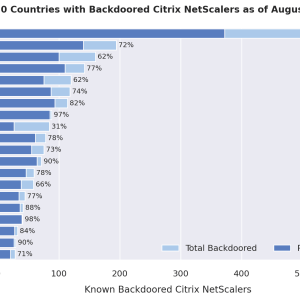
Approximately 2000 Citrix NetScaler servers were backdoored in a massive campaign – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A threat actor has compromised roughly 2,000 Citrix NetScaler servers exploiting a remote code execution tracked as CVE-2023-3519. In July...
Credentials for cybercrime forums found on roughly 120K computers infected with info stealers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers discovered credentials associated with cybercrime forums on roughly 120,000 computers infected with information stealers. Threat intelligence firm Hudson Rock...
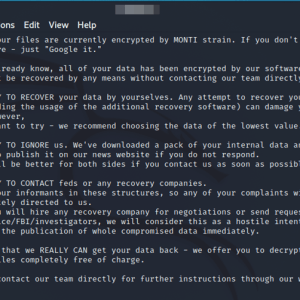
Monti Ransomware gang launched a new Linux encryptor – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Monti Ransomware operators returned, after a two-month pause, with a new Linux variant of their encryptor. The Monti ransomware operators...
Hacking ATMs by exploiting flaws in ScrutisWeb ATM fleet software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers found several flaws in the ScrutisWeb ATM fleet monitoring software that can expose ATMs to hack. Researchers from the...
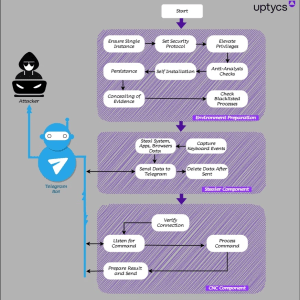
QwixxRAT, a new Windows RAT appears in the threat landscape – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini QwixxRAT is a new Windows remote access trojan (RAT) that is offered for sale through Telegram and Discord platforms. The...
Ongoing Xurum attacks target Magento 2 e-stores – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of ongoing attacks, dubbed Xurum, targeting e-commerce websites using Adobe’s Magento 2 CMS. Akamai researchers warn of ongoing...
Colorado HCPF Department notifies 4 million individuals after IBM MOVEit breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Colorado Department of Health Care Policy & Financing (HCPF) disclose a data breach after MOVEit attack on IBM. The...
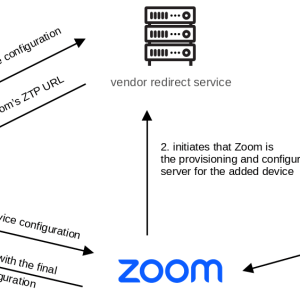
Experts found multiple flaws in AudioCodes desk phones and Zoom’s Zero Touch Provisioning (ZTP) – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple flaws in AudioCodes desk phones and Zoom’s Zero Touch Provisioning (ZTP) can expose to several attacks. Researchers from security...
Nine flaws in CyberPower and Dataprobe solutions expose data centers to hacking – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple vulnerabilities in CyberPower PowerPanel Enterprise DCIM platform and Dataprobe PDU could expose data centers to hacking. Researchers from Trellix...
Multiple flaws in CODESYS V3 SDK could lead to RCE or DoS – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini 16 vulnerabilities in Codesys products could result in remote code execution and DoS attacks exposing OT environments to hacking. Microsoft...
Security Affairs newsletter Round 432 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
The DHS’s CSRB to review cloud security practices following the hack of Microsoft Exchange govt email accounts – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The DHS’s CSRB will review cloud security practices following recent hacks of Microsoft Exchange accounts used by US govt agencies....
Police dismantled bulletproof hosting service provider Lolek Hosted – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A joint operation conducted by European and U.S. law enforcement agencies dismantled the bulletproof hosting service provider Lolek Hosted. Lolek Hosted...
Python URL parsing function flaw can enable command execution – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A severe vulnerability in the Python URL parsing function can be exploited to gain arbitrary file reads and command execution....
UK govt contractor MPD FM leaks employee passport data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini UK govt contractor MPD FM left an open instance that exposed employee passports, visas, and other sensitive data MPD FM,...
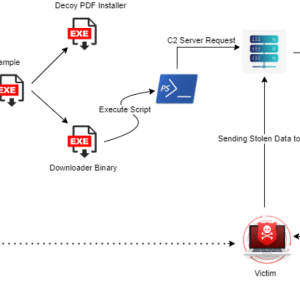
Power Generator in South Africa hit with DroxiDat and Cobalt Strike – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors employed a new variant of the SystemBC malware, named DroxiDat, in attacks aimed at African critical infrastructure. Researchers from...
The Evolution of API: From Commerce to Cloud – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini API (or Application Programming Interface) is a ubiquitous term in the tech community today, and it’s one with a long...
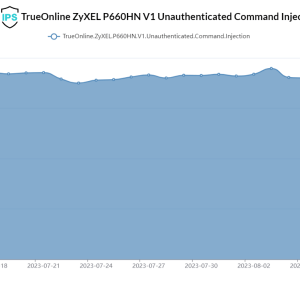
Gafgyt botnet is targeting EoL Zyxel routers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers warn that the Gafgyt botnet is actively exploiting a vulnerability impacting the end-of-life Zyxel P660HN-T1A router. A variant of...
Charming Kitten APT is targeting Iranian dissidents in Germany – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Germany’s Federal Office for the Protection of the Constitution (BfV) warns that the Charming Kitten APT group targeted Iranian dissidents...
Statc Stealer, a new sophisticated info-stealing malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn that a new info-stealer named Statc Stealer is infecting Windows devices to steal a broad range of sensitive information. Zscaler...
CISA discovered a new backdoor, named Whirlpool, used in Barracuda ESG attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. Cybersecurity & Infrastructure Security Agency (CISA) observed a new backdoor, named Whirlpool, in attacks on Barracuda ESG appliances....
CISA adds actively exploited flaw in .NET, Visual Studio to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added zero-day vulnerability CVE-2023-38180 affecting .NET and Visual Studio to its Known Exploited Vulnerabilities catalog. US Cybersecurity and...
US Govt launches Artificial Intelligence Cyber Challenge – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The US Government House this week launched an Artificial Intelligence Cyber Challenge competition for creating a new generation of AI...
Data of all serving police officers Police Service of Northern Ireland (PSNI) mistakenly published online – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Police Service of Northern Ireland (PSNI) mistakenly shared sensitive data of all 10,000 serving police officers in response to a...
Balada Injector still at large – new domains discovered – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Balada Injector is still at large and still evading security software by utilizing new domain names and using new...
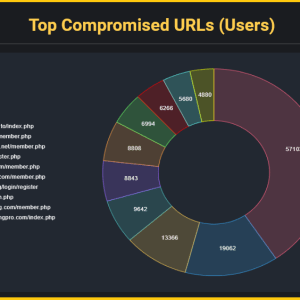
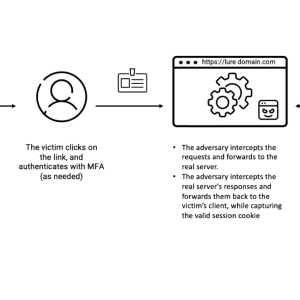
EvilProxy used in massive cloud account takeover scheme – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cloud account takeover scheme utilizing EvilProxy hit over 100 top-level executives of global organizations EvilProxy was observed sending 120,000 phishing...
Downfall Intel CPU side-channel attack exposes sensitive data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google researcher Daniel Moghimi devised a new side-channel attack technique, named Downfall, against Intel CPU. Google researcher Daniel Moghimi devised...