Source: securityaffairs.com – Author: Pierluigi Paganini Researchers warn that more than 3,000 unpatched Openfire servers are exposed to attacks using an exploit for a recent flaw....
Author:
DoJ charged Tornado Cash founders with laundering more than $1 billion – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. DoJ charged two men with operating the Tornado Cash service and laundering more than $1 Billion in criminal...
FBI identifies wallets holding cryptocurrency funds stolen by North Korea – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. FBI warned that North Korea-linked threat actors may attempt to cash out stolen cryptocurrency worth more than $40...
Carderbee APT targets Hong Kong orgs via supply chain attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A previously unknown APT group, tracked as Carderbee, was behind a supply chain attack against Hong Kong organizations. Symantec Threat...
TP-Link Tapo L530E smart bulb flaws allow hackers to steal user passwords – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Four vulnerabilities in the TP-Link Tapo L530E smart bulb and impacting the mobile app used to control them expose users...
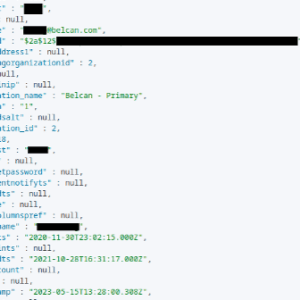
Defense contractor Belcan leaks admin password with a list of flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US Government and defense contractor Belcan left its super admin credentials open to the public, Cybernews research team reveals. Belcan...
Akira ransomware gang spotted targeting Cisco VPN products to hack organizations – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Akira ransomware gang targets Cisco VPN products to gain initial access to corporate networks and steal their data. The...
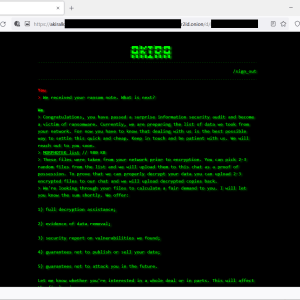
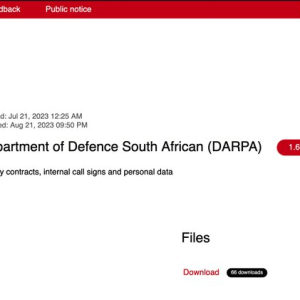
Snatch gang claims the hack of the Department of Defence South Africa – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Snatch gang claims the hack of the Department of Defence South Africa and added the military organization to its leak...
CISA adds critical Adobe ColdFusion flaw to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added critical vulnerability CVE-2023-26359 in Adobe ColdFusion to its Known Exploited Vulnerabilities catalog. US Cybersecurity and Infrastructure Security Agency (CISA)...
A cyber attack hit the Australian software provider Energy One – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Australian software provider Energy One announced it was hit by a cyberattack last week that affected certain corporate systems...
Ivanti fixed a new critical Sentry API authentication bypass flaw – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ivanti warned customers of a new critical Sentry API authentication bypass vulnerability tracked as CVE-2023-38035. The software company Ivanti released...
BlackCat ransomware group claims the hack of Seiko network – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The BlackCat/ALPHV ransomware group claims to have hacked the Japanese maker of watches Seiko and added the company to its...
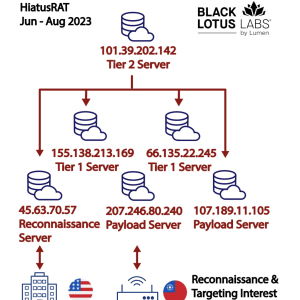
New HiatusRAT campaign targets Taiwan and U.S. military procurement system – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini HiatusRAT malware operators resurfaced with a new wave of attacks targeting Taiwan-based organizations and a U.S. military procurement system. In...
Spoofing an Apple device and tricking users into sharing sensitive data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini White hat hackers at the recent hacking conference Def Con demonstrated how to spoof an Apple device and trick users...
Israel and US to Invest $3.85 Million in projects for critical infrastructure protection through the BIRD Cyber Program – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Israel and US government agencies announced the BIRD Cyber Program, an investment of roughly $4M in projects to enhance the...
N. Korean Kimsuky APT targets S. Korea-US military exercises – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea-linked APT Kimsuky launched a spear-phishing campaign targeting US contractors working at the war simulation centre. North Korea-linked APT...
Four Juniper Junos OS flaws can be chained to remotely hack devices – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Juniper Networks addressed multiple flaws in the J-Web component of Junos OS that could be chained to achieve remote code...
Security Affairs newsletter Round 433 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Cybersecurity: CASB vs SASE – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Understanding cybersecurity aspects addressed by Cloud Access Security Broker (CASB) and Secure Access Service Edge (SASE) In an increasingly digital...
Over 3,000 Android Malware spotted using unsupported/unknown compression methods to avoid detection – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors are using Android Package (APK) files with unsupported compression methods to prevent malware analysis. On June 28th, researchers...
WinRAR flaw enables remote code execution of arbitrary code – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A flaw impacting the file archiver utility for Windows WinRAR can allow the execution of commands on a computer by...
#OpFukushima: Anonymous group protests against the plan to dump Fukushima RADIOACTIVE wastewater into Pacific – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini #OpFukushima: The famous collective Anonymous has launched cyberattacks against Japan nuclear websites over Fukushima water plan. The hacker collective Anonymous...
Massive phishing campaign targets users of the Zimbra Collaboration email server – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A massive social engineering campaign is targeting users of the Zimbra Collaboration email server to steal their login credentials. ESET...
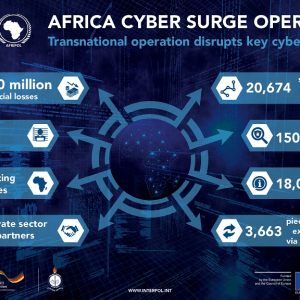
Africa Cyber Surge II law enforcement operation has led to the arrest of 14 suspects – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini An international law enforcement operation across 25 African countries has led to the arrest of 14 cybercriminals. A coordinated law...
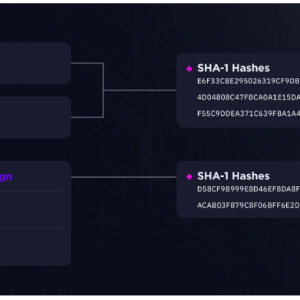
Bronze Starlight targets the Southeast Asian gambling sector – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of an ongoing campaign attributed to China-linked Bronze Starlight that is targeting the Southeast Asian gambling sector. SentinelOne...
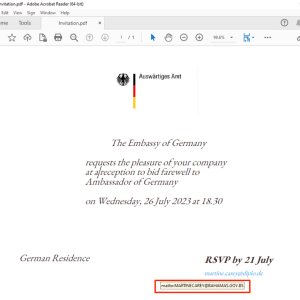
APT29 is targeting Ministries of Foreign Affairs of NATO-aligned countries – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked APT29 used the Zulip Chat App in attacks aimed at ministries of foreign affairs of NATO-aligned countries EclecticIQ researchers...
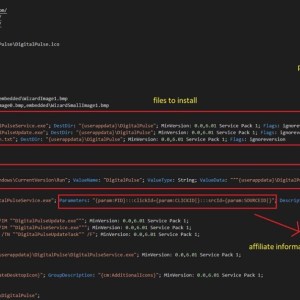
A massive campaign delivered a proxy server application to 400,000 Windows systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers discovered a massive campaign that delivered a proxy server application to at least 400,000 Windows systems. AT&T Alien Labs...
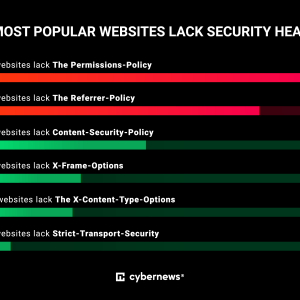
Alarming lack of cybersecurity practices on world’s most popular websites – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The world’s most popular websites lack basic cybersecurity hygiene, an investigation by Cybernews shows. Do you happen to love exploring...
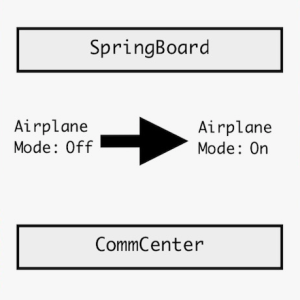
Experts devise an exploit for Apple iOS 16 that relies on fake Airplane Mode – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers detailed a new exploit for Apple iOS 16 that can allow attackers to gain access to a device even...
Cleaning Products manufacturer Clorox Company took some systems offline after a cyberattack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cleaning products manufacturer Clorox Company announced that it has taken some systems offline in response to a cyberattack. The Clorox...