The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Author: Lucas Coletta
Risk in Focus 2024 Global Summary
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
RISK LEVELSELF – ASSESSMENT FINDINGS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Red Team Operating in a Modern Environment
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Radar El magazine de ciberseguridad
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ULTIMATE RACI MATRIX
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Horizons
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Privacy technology: What’s next?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Privacy Intro and Implementation Toolkits (GDPR and ISO 27701)
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Powershell Tips & Tricks for r/b/p teamers
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Position-independent code
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CHEATSHEET PORT FORWARD & TUNNELLING
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Planning Considerations for Cyber Incidents
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Pipeline Security Guidelines
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Phishing Email Analysis
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Howto Improve Your Personal Cybersecurity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Personnel Security Maturity Model
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
EXPLAINING PENETRATION TESTING
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Pentration Testing, Beginners To Expert!
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Conoce los nuevos requisitos obligatorios PCI DSS V.4
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Payment Card Industry Data Security Standard (PCI DSS) v4.0 on AWS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Process for Attack Simulation & Threat Analysis
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Passkeys: The End of Passwords?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OWASP Top 10 Mobile Risks
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OSCP Cheat Sheet
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OPERATION BLOCKBUSTER: Unraveling the Long Thread of the Sony Attack
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
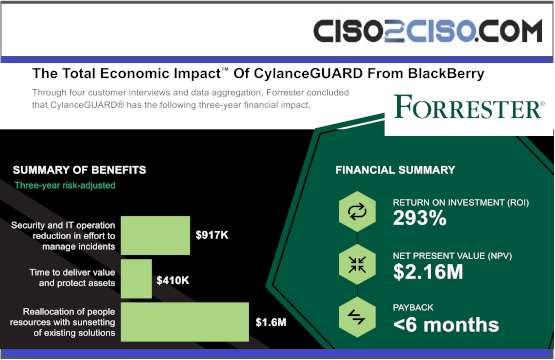
The Total Economic Impact™ Of Cylance GUARD From BlackBerry
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NIST PHISH SCALE USER GUIDE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Data Classification Concepts and Considerations for Improving Data Protection
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NIS 2A Quick Reference Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...