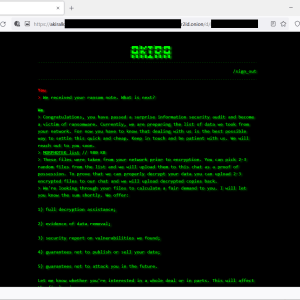
Source: securityaffairs.com – Author: Pierluigi Paganini
The Akira ransomware gang targets Cisco VPN products to gain initial access to corporate networks and steal their data.
The Akira ransomware has been active since March 2023, the threat actors behind the malware claim to have already hacked multiple organizations in multiple industries, including education, finance, and real estate. Like other ransomware gangs, the group has developed a Linux encryptor to target VMware ESXi servers.
The group now is targeting Cisco VPN products to gain initial access to corporate networks.
Sophos researchers observed in May the threat actor using compromised Cisco VPN accounts to breach target networks.
Bleeping Computer reported that information shared by the incident responder as ‘Aura’ on Twitter. Aura confirmed that threat actors targeted organizations using CISCO VPN appliances without MFA enabled.
I’m just gonna go ahead and say it. If you have:
Cisco VPN
No MFA for itYou may get a surprise knock from #Akira #Ransomware soon.
So yeah, go look at your AD auth logs for 4624/4625 from a WIN-* machine in your user VPN range.
If you have a hit, may the IR Gods help you.
— Aura (@SecurityAura) August 5, 2023
BleepingComputer also reported that SentinelOne is investigating the possibility that the Akira ransomware group is exploiting an unknown vulnerability in the Cisco VPN software. The experts speculate that this issue might allow threat actors to bypass authentication in the absence of MFA and that the group launched an ongoing campaign against Cisco VPN appliances.
SentinelOne researchers also observed Akira operators using the legitimate RustDesk open-source remote access tool to maintain access to compromised networks.
In June, cybersecurity firm Avast released a free decryptor for the Akira ransomware that can allow victims to recover their data without paying the ransom.
The threat actors responded by patching their encryptors, making it impossible for victims use them to recover data encrypted by newer versions.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Akira ransomware)
Original Post URL: https://securityaffairs.com/149770/malware/akira-ransomware-cisco-vpn.html
Category & Tags: Breaking News,Cyber Crime,Malware,Akira ransomware,Cisco VPN,Hacking,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News – Breaking News,Cyber Crime,Malware,Akira ransomware,Cisco VPN,Hacking,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News
Views: 1