There is certainly no shortage of security scanning tools when it comes to building a secure SDLC. The below architecture is really well put together, but just look at the sheer amount of different tools that can be selected (and this isn’t close to all of the options out there!):
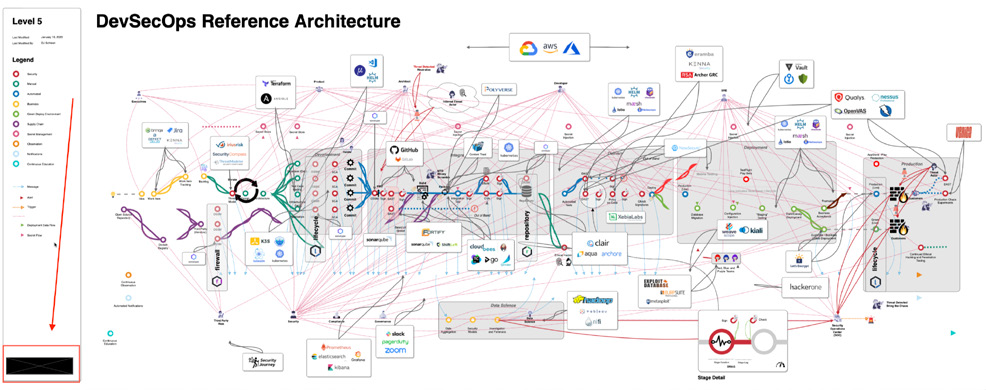
Figuring out which tool to pick for which purpose and where the tool should go in your SDLC is such
a large part of the challenge of building a secure SDLC. When trying to navigate this space, it’s really
easy to get lost really quickly and go down rabbit holes you can’t dig yourself out of. In this guide,
we’re going to cover the following about the different tools offered in each stage of a secure SDLC:
- What are the “typical” stages of a secure SDLC
- What tool types are typically used in each stage, and what do they do (e.g. DAST vs. SAST vs. CSPM vs. CWPP)
- Examples of the vendors offering those tools, along with a quick blurb about them, and a direct link to the specific vendor’s product website
- Some additional resources that can help you build a secure SDLC
What’s a Secure SDLC?
A secure SDLC is a process that companies follow to ensure that the software they develop and deploy is secure by design, and minimizes vulnerabilities and misconfigurations. The steps involved in a secure SDLC can vary depending on the specific organization, but it typically involves identifying and addressing security concerns at each stage of the software development lifecycle – from design and code (early in the SDLC) to deployment and monitoring (later in the SDLC). By following a secure SDLC, companies can reduce the risk of security & infrastructure breaches and protect their software and data from potential threats.
Views: 15




















































