Source: www.bleepingcomputer.com – Author: Bill Toulas

Security researchers discovered a new malware-as-a-service (MaaS) named ‘BunnyLoader’ advertised on multiple hacker forums as a fileless loader that can steal and replace the contents of the system clipboard.
The malware is under rapid development, with updates adding new features and bug fixes. It can currently download and execute payloads, log keys, steal sensitive data and cryptocurrency, and execute remote commands.
The first version of BunnyLoader emerged on September 4. Since then, its developers added more functions, like multiple anti-detection mechanisms and extra info-stealing capabilities, releasing a second major version towards the end of the month.
Researchers at cloud security company Zscaler note that BunnyLoader is quickly becoming popular among cybercriminals as a feature-rich malware available for a low price.
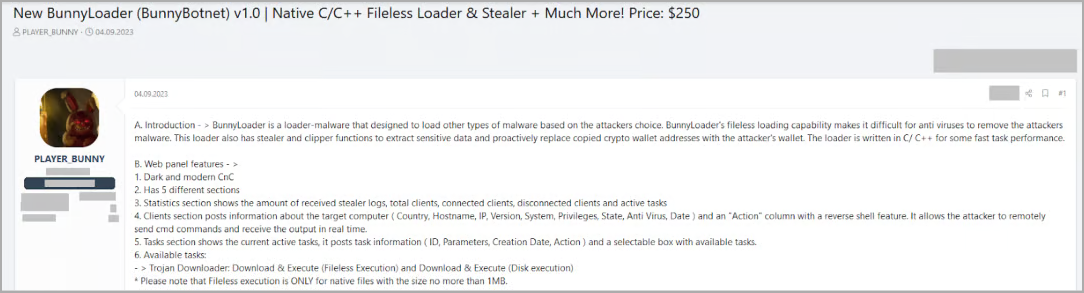
BunnyLoader overview
BunnyLoader’s command and control panel allows even low-skilled cybercriminals set a second-stage payload, enable keylogging, credential stealing, clipboard manipulation (for stealing cryptocurrency), and running remote commands on infected devices.
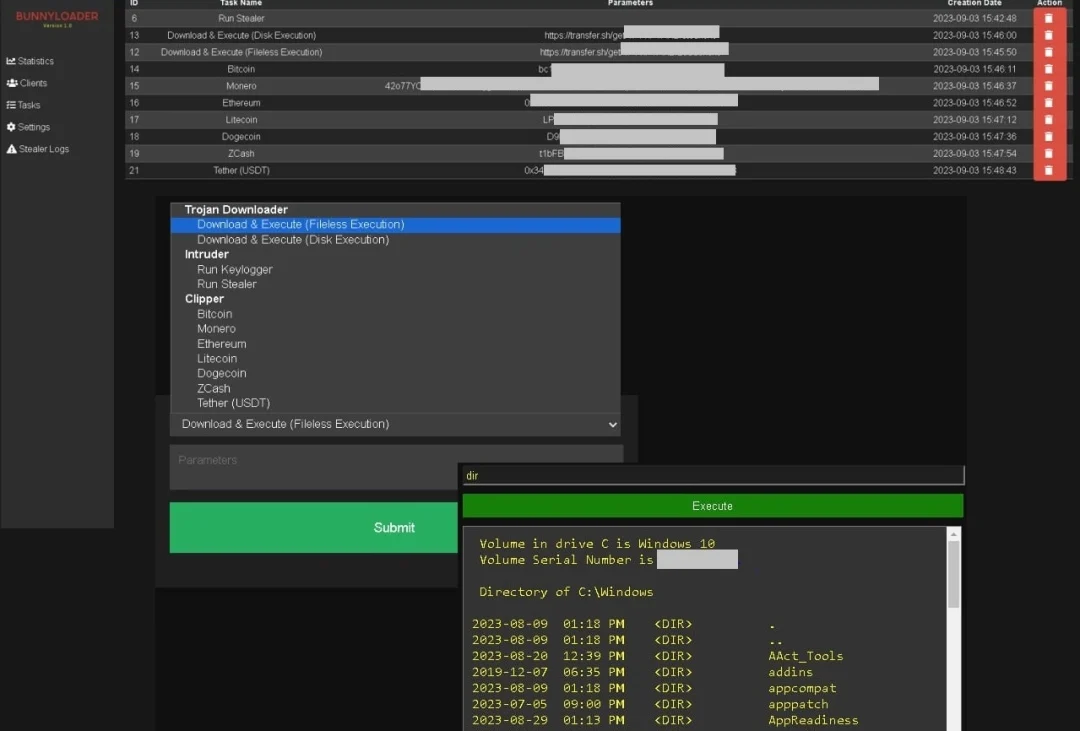
In a recent report, researchers say that after being executed on a compromised device, BunnyLoader creates a new value in the Windows Registry for persistence, hides its window, sets a mutex to avoid multiple instances of itself, and registers the victim into the control panel.
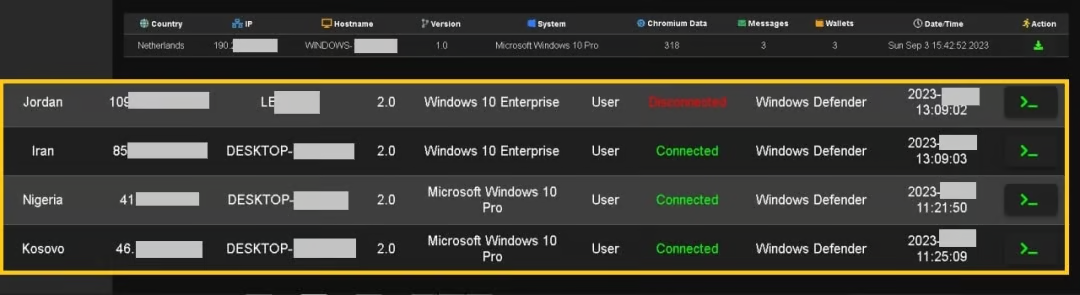
The malware performs several checks to determine if it’s running on a sandbox or simulated environment and throws a fake architecture incompatibility error if the result is positive.
Apart from the mentioned functions, the malware also features modules to steal data stored on web browsers (passwords, credit cards, browsing history), cryptocurrency wallets, VPNs, messaging apps, and more, essentially acting as a standard info-stealer.
All stolen data are compressed into a ZIP archive before they are exfiltrated to the threat actor’s command and control (C2) server.
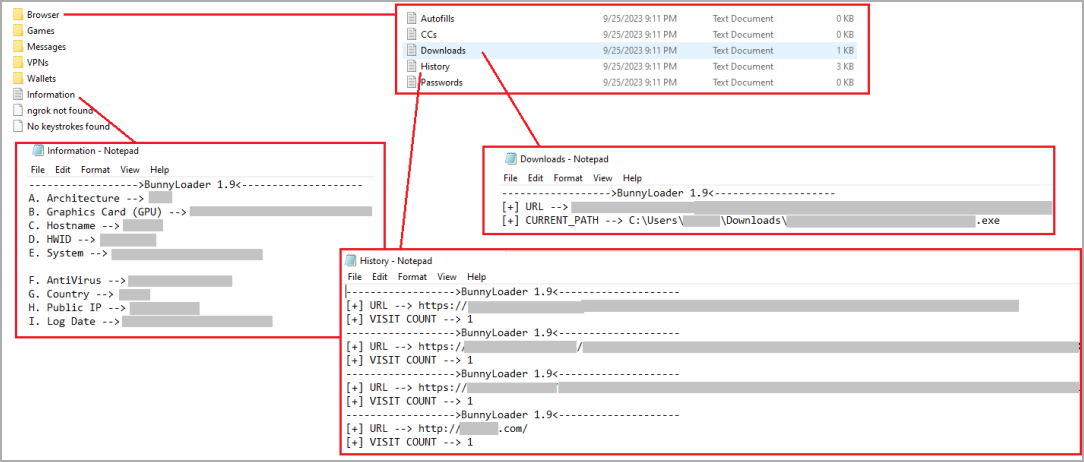
According to the researchers, BunnyLoader supports writing payloads to the disk before executing them, and can also run them from the system memmory (fileless) using the process hollowing technique.
Rapid development
Zscaler monitored the malware’s development and announcements on multiple hacking forums and noticed that it went through numerous updates since its initial release.
Here’s a summary of BunnyLoader’s development timeline:
- v1.0 (Sept 4): Initial release.
- v1.1 (Sept 5): Fixed client bug, introduced log compression before upload, and added ‘pwd’ command for reverse shell.
- v1.2 (Sept 6): Enhanced stealer with browser history recovery, NGRok auth-token recovery, and supported additional Chromium browser paths.
- v1.3 (Sept 9): Added credit card recovery for 16 card types and fixed C2 bugs.
- v1.4 (Sept 10): Implemented AV evasion.
- v1.5 (Sept 11): Introduced VPN recovery to stealer, fileless loader bug fixes, and log loading optimizations.
- v1.6 (Sept 12): Added downloads history viewer and anti-sandbox techniques.
- v1.7 (Sept 15): Enhanced AV evasion.
- v1.8 (Sept 15): Implemented keylogger functionality and resolved various bugs.
- v1.9 (Sept 17): Enhanced stealer with game recovery, more Chromium browser paths, and added a desktop wallet recovery.
- v2.0 (Sept 27): Updated C2 GUI, fixed critical vulnerabilities, including SQL injection and XSS, introduced exploit attempt detection, and further optimized stealer and fileless loader functionalities.
In its current state, BunnyLoader is sold for $250, while the “private stub” version, which features stronger anti-analysis, in-memory injection, AV evasion, and additional persistence mechanisms, sells for $350.
This low price, combined with the rapid development cycle, make BunnyLoader a lucrative choice for cybercriminals seeking early-bird deals on emerging malware projects before they gain prominence and increase their rates.
Zscaler’s report provides technical details that can help detect the malware before it establishes persistence as well as indicators of compromise that could prevent an infection.
Original Post URL: https://www.bleepingcomputer.com/news/security/new-bunnyloader-threat-emerges-as-a-feature-rich-malware-as-a-service/
Category & Tags: Security – Security
Views: 0




















































