Source: www.databreachtoday.com – Author: 1.
Cybercrime
,
Cybercrime as-a-service
,
Endpoint Security
Don’t Panic: Apparent macOS Beta Testing is Highly Buggy, Poses No Immediate Threat
Mathew J. Schwartz
(euroinfosec)

Apple users: Don’t fear new ransomware designed to target macOS devices.
See Also: Webinar Live Tomorrow | The Evolution of Network Architecture: What You Don’t Know Can Hurt You
That’s the critical consensus for a fresh strain of crypto-locking malware developed by the notorious LockBit group that is designed to infect laptops and desktops running Apple’s operating system.
The ransomware sample was first detailed Friday by researchers at MalwareHunterTeam, which said it’s designed to infect Macintosh devices running Apple silicon chips – first introduced in November 2020 in higher-end devices. The sample initially spotted by researchers was compiled on March 20. Subsequently, via VirusTotal, researchers found versions of the ransomware dating from November 2022.
“We believe this is the first time a large ransomware threat group has developed a payload for Apple products,” said the anti-malware researchers behind the vx-underground project.
There’s no evidence this macOS version of LockBit has ever been used for any actual, in-the-wild attacks, says Brett Callow a threat analyst at security firm Emsisoft.
Historically, malware writers have focused on Windows and to a lesser extent Linux, given their market penetration. While Mac malware occasionally surfaces, it’s often seen as more of a novelty – for security researchers – and little more than a nuisance for enterprise users or consumers.
In part, that’s because Apple has added a raft of protections designed to keep malware off of systems running version 13.3 – aka Ventura – and earlier versions of its operating system. This includes GateKeeper, which prevents untrusted apps from executing without explicit user approval; transparency, consent and control – aka TCC – safeguards, which block apps from accessing core OS and document files without explicit consent; and system integrity protection, or SIP, which blocks the execution of unauthorized code.
No Apples Currently at Risk
The primary problem facing LockBit’s current Mac-targeting malware is simple: it doesn’t work.
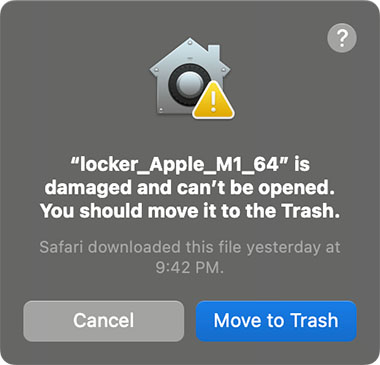
Mac security researcher Patrick Wardle says LockBit’s developers appear to have recompiled versions or modules from their existing ransomware designed to target devices running Windows, Linux or VMware ESXi operating systems, with imperfect results. Notably, the latest sample he studied is so buggy that it regularly crashes due to buffer overflows. In addition, he said, the code is unsigned, meaning it can’t be easily executed, and has no ability to defeat GateKeeper, or the TCC or SIP protections, which means it can’t encrypt many files.
“This sample is far from ready for primetime,” Wardle said in a blog post.
Despite the technical shortcomings, the sample he studied already had the group’s shakedown message ready to roll. “If you don’t pay the ransom, the data will be published on our TOR darknet sites,” it reads in part. “The sooner you pay the ransom, the sooner your company will be safe.”
Assuming the data-theft claims aren’t just bluster, how LockBit-wielding attackers might exfiltrate data from macOS systems also remains unclear, given the aforementioned protections.
Real Tests, or PR Move?
Still, LockBit has a reputation on the technical side for building sophisticated malware designed to quickly infect systems in a manner that victims can’t crack. In its bid to attract new affiliates, or business partners, the group regularly trumpets the supposed speed and reliability of its wares.
At the same time and like many other big-name groups, LockBit has a predilection for rampant self-promotion, often via the group’s public-facing LockBitSupp persona. The group is no stranger to half-truths or about-face maneuvers of convenience, especially as it attempts to make itself look bigger and badder than rivals, in part to scare victims into paying quickly and quietly.
LockBitSupp told Bleeping Computer Sunday that the group’s Mac encryptor is “actively being developed.”
Whether its macOS tests are anything more than a half-baked experiment or empty PR move remains unclear.
Wardle says the mandate is to prepare for more of this sort of malicious code development. “The fact that a large ransomware gang – LockBit – has apparently set its sights on macOS should give us all pause for concern … and, if nothing else, make sure we’re adequately prepared for future attacks that likely will be more polished and thus pose a greater risk,” he said.
Original Post url: https://www.databreachtoday.com/blogs/lockbit-ransomware-tests-taking-bite-out-apple-users-p-3440
Category & Tags: –
Views: 0




















































