In today’s fast-paced world, identity management has become a crucial aspect of every organization. From securing sensitive data to ensuring compliance with regulations, effective Identity Lifecycle Management (ILM) is essential for businesses of all sizes. However, implementing an ILM strategy can be challenging without proper guidance and knowledge. In this article, we’ll share the best practices for effective ILM that will help you streamline your processes and ensure success in managing identities throughout their lifecycle – from creation to retirement. So, buckle up and get ready to learn some tips and tricks that will take your ILM strategy to the next level!
What Is Identity Lifecycle Management?
An organization needs access to essential information, apps, and processes to perform assigned tasks whenever it hires a new employee, engages a new contractor, or hires a third party. Identity does not only apply to humans, but also to services, systems, SSH keys, API keys, and IoT devices.
Identity lifecycle management (ILM) is the process of managing the identity of an individual or organization from birth to death. This includes creating and maintaining an accurate and up-to-date record of the individual or organization’s identity, as well as managing any changes to that identity over time.
1. Accurate and up-to-date records
One of the key challenges with ILM is keeping track of all the different data points associated with an individual or organization’s identity. This data can come from a variety of sources, both internal and external, so it’s important to have a system in place for collecting and storing this information.
2. Managing changes over time
Another challenge with ILM is that identities often change over time – for example, when someone changes their name. It’s important to have a process in place for tracking these changes and updating the records accordingly.
3. Security and privacy
Given the sensitive nature of identity information, it’s crucial to have strong security measures in place to protect this data. This includes both physical and cybersecurity, as well as ensuring compliance with relevant privacy laws and regulations.
4. Scalability
As your organization grows, so too will the number of identities you need to manage. It’s important to have an ILM strategy that can scale along with.
ILM Strategy Best Practices
An effective ILM strategy can provide many benefits to an organization, including improved security, reduced costs, and increased efficiency. Here are some tips for creating a successful ILM strategy:
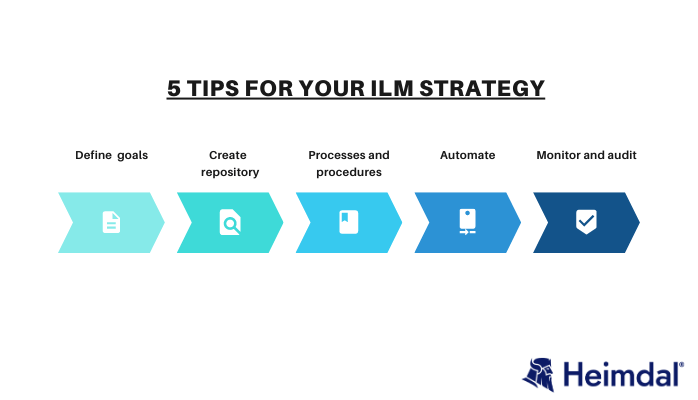
- Define your goals. What do you hope to achieve with your ILM strategy? Be sure to consider the needs of all stakeholders when setting goals.
- Create a centralized repository. A central location for identity data will make it easier to manage and secure.
- Establish processes and procedures. Well-defined processes and procedures will help ensure that your ILM strategy is executed effectively.
- Automate where possible. Automation can help improve efficiency and reduce errors in identity data management.
- Monitor and audit regularly. Regular monitoring and auditing will help you identify any problems with your ILM strategy so that you can make necessary changes.
Additionally, there are a few best practices that should be followed.
- First, it is important to understand the needs of your organization and what type of data needs to be protected. This will help you to determine which ILM solution will best fit your needs.
- Secondly, you need to consider the different stages of the ILM process and how each stage can be implemented within your organization.
- Lastly, you should develop a plan for how you will monitor and evaluate the effectiveness of your ILM strategy on an ongoing basis.
Provisioning – creating new employees, contractors, third parties, and machine identities should follow the Principle of Least Privilege (POLP) these days. In other words, once an identity is verified— via, for example, Single Sign-On (SSO) and Multi-Factor Authentication (MFA) —the user or machine will only be given access to the data required for their job or to perform specific tasks.
Updating/changes –in order for human user privileges to change, sensitive data access levels must be adjusted accordingly. Throughout the identity lifecycle, Role-Based Access Controls (RBAC) dictated by stated policies help maintain proper user access. As part of the lifecycle process, revoke access when it is no longer needed.
Controlling privilege scope creep – human users can accumulate access privileges over time, which in some cases may mean giving them far more access than they need to complete a given task. Local admin accounts are prime targets for attackers who want to compromise them and escalate privileges so that they can traverse the network undetected.
Deprovisioning – the deprovisioning of accounts on a timely basis is necessary to minimize the risk of unauthorized access. The same holds true for machine identities associated with service accounts.
The Role of Policies and Regulations in ILM
Policies and regulations play an important role in identity lifecycle management (ILM), as they provide the framework within which ILM activities must take place. Without policies and regulations in place, it would be difficult to manage identities effectively.
Policies and regulations help to ensure that data is collected and managed in a consistent manner, and that processes are carried out in a way that is fair and transparent. They also help to protect people’s privacy and ensure that their personal data is handled securely.
In order to be effective, policies and regulations must be fit for purpose and regularly reviewed. They should also be communicated clearly to all those who need to comply with them.
Challenges with Implementing an ILM Strategy
One of the challenges with implementing an ILM strategy is that there are many moving parts. To be successful, you need to have a clear understanding of each component and how it works together. Additionally, you need to have a plan for managing and maintaining each component over time.
Furthermore, identity lifecycle management can be complex and resource intensive. There are many steps involved, from initial data collection to ongoing maintenance. This can make it difficult to implement an ILM strategy effectively without dedicated resources.
Finally, it’s important to keep in mind that an ILM strategy is not a one-time project. It’s an ongoing process that needs to be regularly reviewed and updated as your organization changes. This can be challenging, but it’s essential to ensure that your ILM strategy remains effective over time.
How to Automate Your ILM Processes
Enterprise identity lifecycle management (ILM) is a critical part of ensuring the security and compliance of your organization. ILM processes help you manage the identities of your users, both internally and externally. Automating your ILM processes can help you save time and resources, while still maintaining a high level of security.
When automating your ILM processes, there are a few key things to keep in mind:
- Make sure you have a clear understanding of your organization’s needs. What kind of data do you need to collect? How often will you need to update this data? What are your compliance requirements? Answering these questions will help you determine which ILM processes need to be automated.
- Choose an identity management solution that offers robust automation capabilities. Not all identity management solutions are created equal – make sure you select one that can meet your specific needs.
- Configure your automation settings carefully. Depending on the sensitivity of the data involved, you may want to consider setting up different levels of automation. For example, you may want to automatically provision new accounts but require manual approval for account changes or deletions.
How Does PAM Help Govern the Identity Lifecycle?
It’s important that any organization uses Privileged Access Management (PAM) solutions to implement controls that govern both user and service account identities. This is especially true as more organizations than ever move to the cloud. SSO and MFA are typically associated with human identities, but they do not assure effective privilege management after authentication and authorization.
RBAC helps to govern what the user can do once an identity is verified and access is granted. PAM solutions are designed to secure access to sensitive data by ensuring the enforcement of least privilege.
But machine identities on endpoints, servers, and applications that use services to access other systems and use different types of identities to authenticate must also be properly controlled. That means incorporating machine identities as part of your PAM solution to enforce least privilege and comply with policies governing access. Within the broader context of the identity lifecycle, there are certain considerations you should incorporate that relate specifically to service accounts.
- Creation/approval process: As new applications are being deployed, ensure you have an automated service account creation and approval process. Align this with your review and audit process to ensure that more sensitive applications have strict security controls.
- Service dependency mapping: Map and record dependencies because making changes to one service account can impact others as part of your privilege management plan.
- Continuous discovery: Discover service accounts that may have been created outside of an approved process or lifecycle. After that, review them to ensure the correct security policies have been applied.
- Security and governance risk assessments: Map compliance requirements to the appropriate security access controls, implement them, and report on governance.
- Automated auditing and reporting: Monitor, record, and report on service accounts usage and changes as part of your privileged access review and audit. This helps distinguish between authorized and unauthorized changes.
- Updating and reviewing security controls: Group service accounts according to similar risks and categories. Review along with other privileged accounts to ensure that the correct security controls are set for each service account.
- Expiration/review process: Set a review date or expiration date to determine whether the application is still required. This should be done as part of the creation process as well as part of continuous discovery.
- Remove unused/expired service accounts: Continuously remove unused services accounts to reduce the privileged security attack surface. Deprovisioning is a critical stage of the life cycle that’s often overlooked with service accounts.
How Can Heimdal® Help?
In order to enhance your organization’s security, Heimdal recommends integrating our cutting-edge Privileged Access Management solution into your IAM strategy. On top of that, adding the Application Control module to the mix, substantially increases the cybersecurity of your organization since it’s the only tool that can automatically escalate and de-escalate admin rights on infected machines.
Managing privileges is a fundamental aspect of any cybersecurity strategy. Privileged Access Management tools are essential for scalability, as well as managing user rights, fast software installs, logs, audit trails, and achieving data protection compliance.
System admins waste 30% of their time manually managing user
rights or installations
Heimdal® Privileged Access
Management
Is the automatic PAM solution that makes everything
easier.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Conclusion
Identity Lifecycle Management is an important part of any organization’s security strategy. By following the best practices outlined in this article, you can ensure that your ILM strategy is successful and secure. This includes understanding user access requirements, properly managing privileged accounts, and implementing a system for monitoring user activity. With careful planning and ongoing maintenance, organizations can make sure their ILM strategy remains up-to-date and secure so they are better equipped to protect their valuable data.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Views: 1





















































