The Conti ransomware gang is using BazarCall phishing attacks as an initial attack vector to access targeted networks.
BazarCall attack, aka call back phishing, is an attack vector that utilizes targeted phishing methodology and was first used by the Ryuk ransomware gang in 2020/2021.
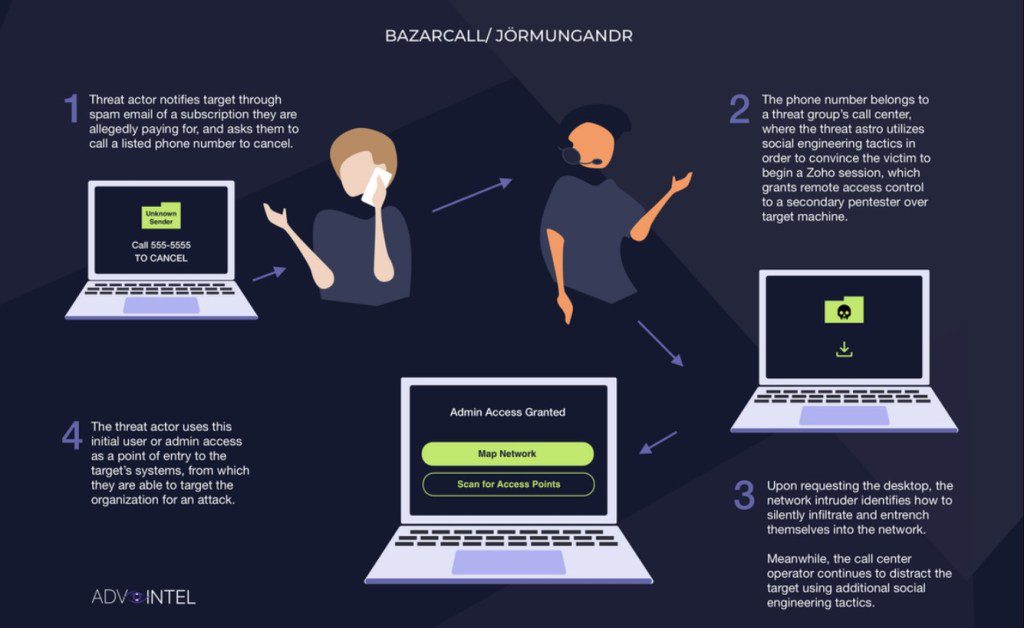
The BazarCall attack chain is composed of the following stages:
Stage One. Attackers send a mail to the victims that notify them that they have subscribed to a service for which payment is automatic. The email includes a phone number to call to cancel the subscription.Stage Two. The victim is tricked into contacting a special call center. When operators receive a call, they use a variety of social engineering tactics, to convince victims to give remote desktop control, to help them cancel their subscription service.Stage Three. Once accessed the victim’s desktop, the attacker silently extended a foothold in the user’s network, weaponizing legitimate tools that are known to be in Conti’s arsenal. The initial operator remains on the line with the victim, pretending to assist them with the remote desktop access by continuing to utilize social engineering tactics.Stage Four. The initiated malware session yields the adversary access as an initial point of entry into the victim’s network.
The researchers at cybersecurity firm AdbIntel state that currently at least three autonomous threat groups are adopting and independently developing their own targeted phishing tactics derived from the call back phishing methodology. The three groups are tracked as Silent Ransom, Quantum, and Roy/Zeon, they emerged after the Conti gang opted to shut down its operation in May 2022.
In March 2022, formed members of the Conti, who were experts in call back phishing attacks, created “Silent Ransom” when it became an autonomous group.
Silent Ransom’s previous bosses, tracked as Conti Team Two, who were the main Conti subdivision, rebranded as Quantum and launched their own version of call back phishing campaigns. On June 13, 2022, AdvIntel researchers uncovered a massive operation called “Jörmungandr”.
The third iteration of the BazarCall group was observed in late June 20 and goes by the name of Roy/Zeon. The group is composed of old-Guard members of Conti’s “Team One,” which created the Ryuk operation. This group has the advanced social engineering capabilities of the three groups.
It involved large investments into hiring spammers, OSINT specialists, designers, call center operators, and expanding the number of network intruders. As a highly skilled (and most likely government-affiliated) group, Quantum was able to purchase exclusive email datasets and manually parse them to identify relevant employees at high-profile companies.
The adoption of Callback phishing campaigns has impacted the strategy of ransomware gangs, experts observed targeted attacks aimed at Finance, Technology, Legal, and Insurance industries. The industries are considered privileged targets in almost all internal manuals, which were shared between ex-Conti members.
“Since its resurgence in March earlier this year, call back phishing has entirely revolutionized the current threat landscape and forced its threat actors to reevaluate and update their methodologies of attack in order to stay on top of the new ransomware food chain.” concludes the report published by Advintel. “Although the first to begin using this TTP as its primary initial attack vector, Silent Ransom is no longer the only threat group utilizing the highly specified phishing operations that they pioneered. Other threat groups, seeing the success, efficiency, and targeting capabilities of the tactic have begun using reversed phishing campaign as a base and developing the attack vector into their own.”
Follow me on Twitter: @securityaffairs and Facebook
(SecurityAffairs – hacking, Conti)
The post BazarCall attacks have revolutionized ransomware operations appeared first on Security Affairs.
Leer másSecurity Affairs
Views: 0