Source: securityaffairs.com – Author: Pierluigi Paganini
Long-existing Bandook RAT targets Windows machines

A new variant of the Bandook remote access trojan (RAT) was spotted in attacks aimed at Windows machines.
Reseachers from Fortinet observed a new variant of a remote access trojan dubbed Bandook that has been used in phishing attacks against Windows users.
Bandook has been active since 2007, it has been continuously developed since then and was employed in several campaigns by different threat actors. The new variant observed in October spreads via phishing messages using a PDF file. This PDF file includes a shortened URL that downloads a password-protected .7z file. Upon extracting the malware from the archive, the malicious code injects its payload into msinfo32.exe.
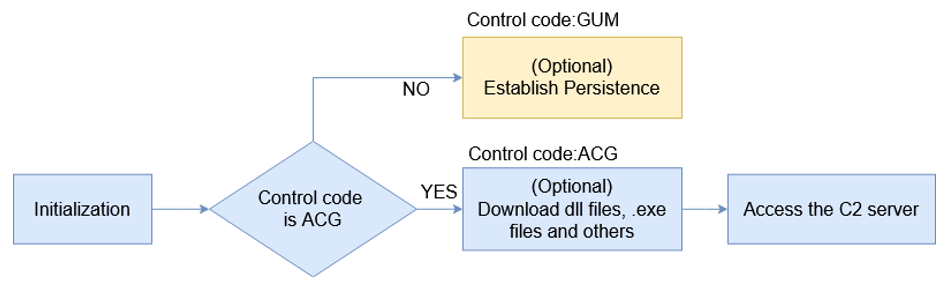
The injector decrypts the payload in the resource table and injects it into msinfo32.exe. The behavior of the payload is determined by a registry key created before the injection.
“Once injected, the payload initializes strings for the key names of registries, flags, APIs, etc. After this, it uses the PID of the injected msinfo32.exe to find the registry key and then decodes and parses the key value to perform the task specified by the control code.” reads the analysis published by the Fortinet.

The payload supports 139 actions, most of them already implemented in previous variants. Recent variants include additional commands for C2 communications.
Bandook supports common capabilities, such as file manipulation, registry manipulation, download, information stealing, file execution, invocation of functions in dlls from the C2, controlling the victim’s computer, process killing, and uninstalling the malware.
“A large number of commands for C2 communication can be found in this malware. However, the tasks performed by its payload are fewer than the number in the command. This is because multiple commands are used for a single action, some commands call functions in other modules, and some are only used to respond to the server.” concludes the report. “Though the entire system is not observed in this attack, FortiGuard will continue monitoring malware variants and provide appropriate protections.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Bandook)
Original Post URL: https://securityaffairs.com/157065/malware/bandook-rat-targets-windows.html
Category & Tags: Breaking News,Malware,Bandook RAT,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News – Breaking News,Malware,Bandook RAT,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,Security Affairs,Security News
Views: 1