Source: www.bleepingcomputer.com – Author: Lawrence Abrams

Google is downplaying reports of malware abusing an undocumented Google Chrome API to generate new authentication cookies when previously stolen ones have expired.
In late November 2023, BleepingComputer reported on two information-stealing malware operations named Lumma and Rhadamanthys, claiming they could restore expired Google authentication cookies stolen in attacks.
These cookies could then be loaded into threat actors’ browsers to gain access to an infected user’s Google accounts.
Since then, four other information stealers have adopted the same technique, including Stealc on December 1, Medusa on December 11, RisePro on December 12, and Whitesnake on December 26.
Last week, cybersecurity firm CloudSEK revealed that these information-stealing malware operations are abusing a Google OAuth “MultiLogin” API endpoint to generate new, working authentication cookies when a victim’s original stolen Google cookies expire.
This API is believed to be designed for synchronizing accounts across different Google services by accepting a vector of account IDs and auth-login tokens.
BleepingComputer’s attempts to learn more about this API from Google have been unsuccessful, and the only documentation can be found in Google Chrome’s source code.
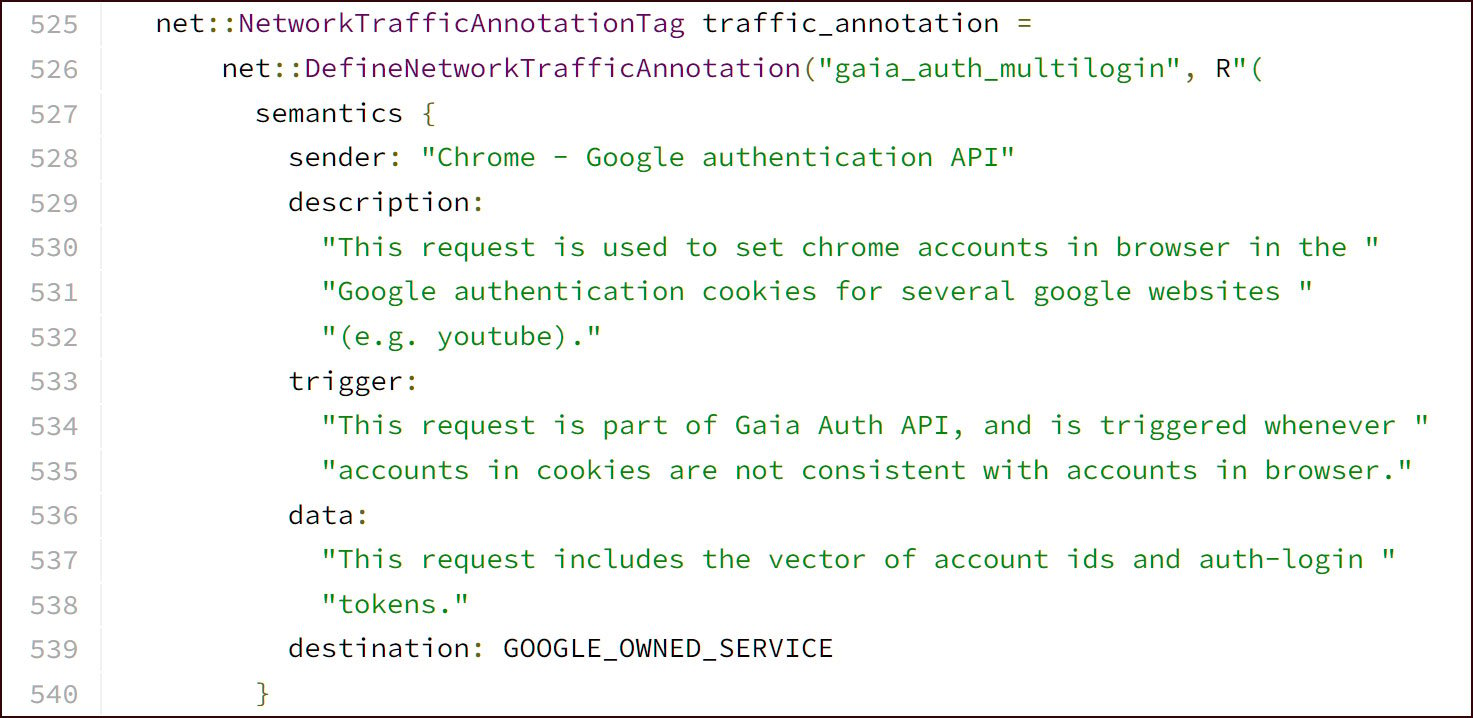
CloudSEK researcher Pavan Karthick told BleepingComputer that the information-stealing malware abusing this feature will now steal multiple tokens from Google Chrome.
These tokens include any authentication cookies for Google sites and a special token that can be used to refresh, or generate, new authentication tokens.
As regular authentication cookies expire after a certain amount of time, they eventually become unusable to the threat actor.
However, as long as the user has not logged out of Google Chrome or revoked all sessions associated with their accounts, the threat actors can use this special “Refresh” token to generate brand new authentication tokens when the previous ones have expired.
These new tokens allow them to continue accessing the accounts for far longer than would usually be allowed.
Not just your standard cookie theft
Unfortunately, Google sees this API abuse as just your regular, garden-variety malware-based cookie theft.
“Google is aware of recent reports of a malware family stealing session tokens,” Google told BleepingComputer in a statement last week.
“Attacks involving malware that steal cookies and tokens are not new; we routinely upgrade our defenses against such techniques and to secure users who fall victim to malware. In this instance, Google has taken action to secure any compromised accounts detected.”
However, sources familiar with this issue have told BleepingComputer that Google believes the API is working as intended and and that no vulnerability is being exploited by the malware.
Google’s solution to this issue is simply having users log out of their Chrome browser from the affected device or kill all active sessions via g.co/mydevices. Doing so will invalidate the Refresh token and make it unusable with the API.
As the info-stealing malware stole your credentials, you should also change your Google password out of caution, especially if you use the same credentials at other sites.
“In the meantime, users should continually take steps to remove any malware from their computer, and we recommend turning on Enhanced Safe Browsing in Chrome to protect against phishing and malware downloads,” Google further recommends.
While these recommended steps will mitigate the impact of information-stealing malware infections, most people infected with this type of malware will not know when to do these steps.
When people are infected with information-stealing malware, they typically do not know until their accounts are accessed without permission and abused in some detectable manner.
For example, an employee for Orange España, the country’s second-largest mobile phone provider, had their passwords stolen by information-stealing malware.
However, no one knew until stolen credentials were used to log into the company’s RIPE account and modify their BGP configuration, causing a 50% performance hit and Internet outages for Orange customers.
While Google says that they have detected those who were impacted by this API abuse and notified them, what happens for future victims?
Furthermore, how will users users know they should log out of their browser to invalidate authentication tokens when they do not even know they were infected in the first place.
For this reason, a better solution would be to restrict access to this API in some manner to prevent abuse by the malware-as-a-service operations. Unfortunately, it does not seem like this is happening.
BleepingComputer has asked Google what plans they have to mitigate this API abuse but has not received a response to these questions.
Original Post URL: https://www.bleepingcomputer.com/news/security/google-malware-abusing-api-is-standard-token-theft-not-an-api-issue/
Category & Tags: Security – Security
Views: 2




















































