The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: August 12, 2024
Cybersecurity_Political_Organisations_Election_Candidates
Political organisations and election candidates have become targets for threat actors that wish to disrupt and interfere in the democratic process. This can be part of...
Cyber Technology Practice Playbook Part I: Common Adversary Attacks – A practical guide for executives to navigate best practices in cyber risk management
Standardized guidelines & best practices THE NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY (NIST) CREATED A VOLUNTARY FRAMEWORK consisting of standard guidelines and best practices to address...
Cyber Security on Azure An IT Professional’s Guide to Microsoft Azure Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Security Monitoring and Logging Guide
This Guide presents details about how to monitor and log cyber security events, some of which are potential indicatorsof compromise (IOC) that can lead to cyber...
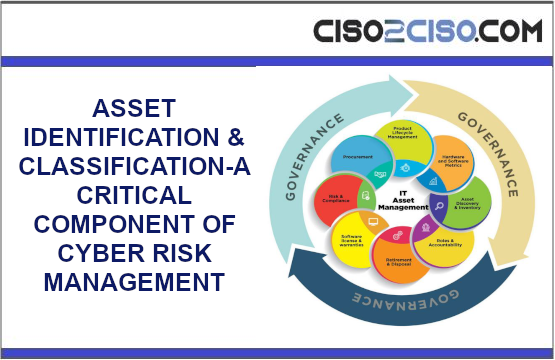
ASSET IDENTIFICATION & CLASSIFICATION-A CRITICAL COMPONENT OF CYBER RISK MANAGEMENT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CybercrimeTrends 2024 The latest threats and security best practices
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Threat Intelligence Guide – What Is Cyber Threat Intelligence and How Is It Used?
This guide provides an introduction to Cyber Threat Intelligence — CTI. It provides accessible advice on the theory and practice of CTI products and services. It...
Cyber Security Politics Socio-Technological Transformations and Political Fragmentation
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...