Source: www.bitdefender.com – Author: Graham Cluley The official Twitter account of the US Securities and Exchange Commission (SEC) was hacked yesterday, with scammers posting an unauthorised...
Day: January 10, 2024
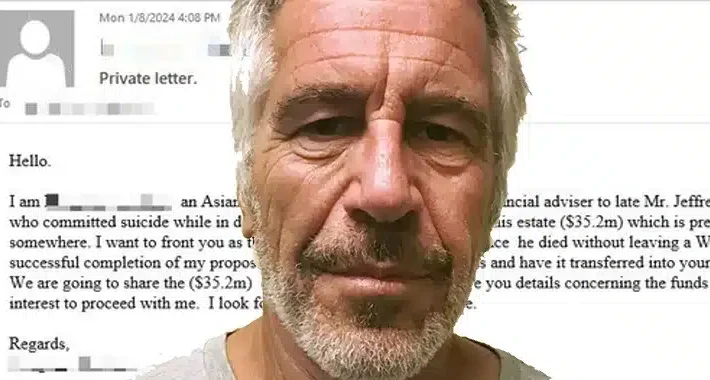
Jeffrey Epstein email scams rear their ugly head – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The security boffins at Bitdefender have detected what they describe as a “resurgence” in email scams related to notorious sex...
Believing they would be paid a fortune for having sex with women, hundreds of Indian men scammed out of cash – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Geeta Pandey at BBC News reports: In early December Mangesh Kumar (name changed) was scrolling on Facebook when he came...
NoaBot: Latest Mirai-Based Botnet Targeting SSH Servers for Crypto Mining – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 10, 2024NewsroomServer Security / Cryptocurrency A new Mirai-based botnet called NoaBot is being used by threat actors as part of...
Getting off the Attack Surface Hamster Wheel: Identity Can Help – Source:thehackernews.com
Source: thehackernews.com – Author: . IT professionals have developed a sophisticated understanding of the enterprise attack surface – what it is, how to quantify it and...
Volexity Catches Chinese Hackers Exploiting Ivanti VPN Zero-Days – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Ivanti confirms active zero-day exploits, ships pre-patch mitigations, but says comprehensive fixes won’t be available until January 22. The post...
ExtraHop Banks $100M in Growth Funding, Adds New Execs – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Seattle network detection and response firm secures $100 million in growth funding and adds to its executive team. The post...
HMG Healthcare Says Data Breach Impacts 40 Facilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The compromised information includes names, contact information, dates of birth, health information, medical treatment details, Social Security numbers, and employee...
French Computer Hacker Jailed in US – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP A computer hacker who was part of a criminal gang that stole data from hundreds of millions of people and sold...
Anecdotes Raises $25 Million for Enterprise GRC Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Anecdotes has raised $25 million in Series B funding, which brings the total investment to $55 million, for its compliance...
Kyocera Device Manager Vulnerability Exposes Enterprise Credentials – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire An improper input validation flaw in Kyocera Device Manager allows attackers to capture credentials, compromise accounts. The post Kyocera Device...
SAP’s First Patches of 2024 Resolve Critical Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire SAP has released patches for critical vulnerabilities in Business Application Studio, Web IDE, and Edge Integration Cell. The post SAP’s...
Dutch Engineer Used Water Pump to Get Billion-Dollar Stuxnet Malware Into Iranian Nuclear Facility: Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs An engineer recruited by intelligence services used a water pump to deliver Stuxnet, which reportedly cost $1-2 billion to develop....
China Says State-Backed Experts Crack Apple’s AirDrop – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Chinese state-backed experts have found a way to identify people who use Apple’s encrypted AirDrop messaging service, according to the Beijing...
Android’s January 2024 Security Update Patches 58 Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Android’s first security update of 2024 resolves high-severity elevation of privilege and information disclosure vulnerabilities. The post Android’s January 2024...
Best Practices for Implementing a IS Awareness Program
Establishing and maintaining information-security awareness through a security awareness program is vital to an organization’s progress and success. A robust and properly implemented security awareness program...
Azure Penetration Testing Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Automotive Cyberthreat
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Attack Against Google Cloud Native App
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ARP Spoofing: Protegiendo-se contra interseptaçã de datos sensíveis
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Process Ghosting Attack
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Physical Security Performance Goals for Faith-Based Communities
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Argo CD End User Threat Model
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
APT Report 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
PCI DSS v4.x: Targeted Risk Analysis Guidance
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OWASP API Security Top 10 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Aproximación a laInteligencia Artificialy la ciberseguridadINFORME DE BUENAS PRÁCTICAS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Anti-Reverse – The “Ultimate”Anti-Debugging Reference
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OSINT Tools for diving deep in to the Dark Web
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Here’s Some Bitcoin: Oh, and You’ve Been Served! – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A California man who lost $100,000 in a 2021 SIM-swapping attack is suing the unknown holder of a cryptocurrency wallet that...