Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) revealed today the top ten most common...
Year: 2023
New OS Tool Tells You Who Has Access to What Data – Source:thehackernews.com
Source: thehackernews.com – Author: . Ensuring sensitive data remains confidential, protected from unauthorized access, and compliant with data privacy regulations is paramount. Data breaches result in...
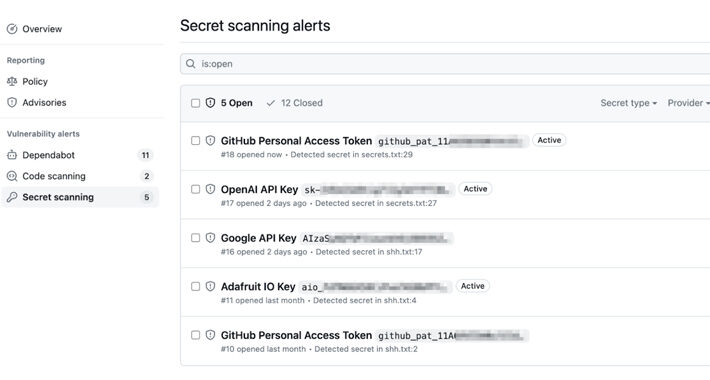
GitHub’s Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 06, 2023NewsroomProgramming / Software Security GitHub has announced an improvement to its secret scanning feature that extends validity checks to...
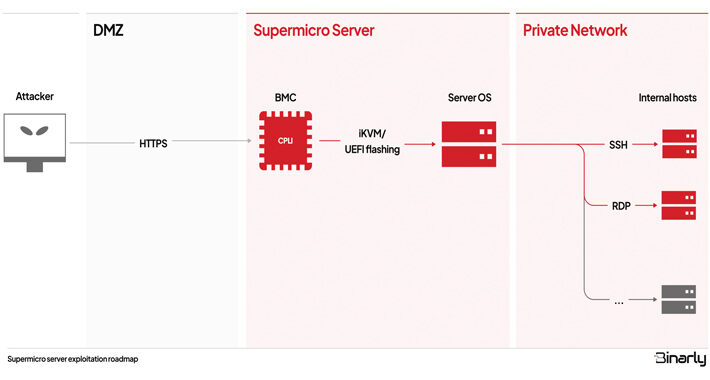
Supermicro’s BMC Firmware Found Vulnerable to Multiple Critical Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 06, 2023NewsroomServer Security / Vulnerability Multiple security vulnerabilities have been disclosed in the Intelligent Platform Management Interface (IPMI) firmware for...
Hospital Lobbyists Press Senator on Online Tracking Limits – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , HIPAA/HITECH , Privacy Sen. Bill Cassidy Considering Sector Feedback on Recent RFI Marianne Kolbasuk McGee (HealthInfoSec)...
Joe Sullivan: What’s a Breach? ‘It’s a Complicated Question’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Incident & Breach Response , Security Operations The Question is Also One for the Legal Team to Own, Says Uber’s Former...
Clorox Expects Double-Digit Sales Drop Following Cyberattack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Ransomware Bleach Manufacturing Giant Spent $25M Cleaning Up Huge Cyberattack in Initial Weeks Michael...
Breach Roundup: Still Too Much ICS Exposed on the Internet – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Also, Apple and Qualcomm Issue Emergency Patches Anviksha More (AnvikshaMore)...
Attackers Exploiting Atlassian Confluence Software Zero-Day – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Breach Notification , Cybercrime Critical Privilege Escalation Bug Helps Create Admin Accounts Mihir Bagwe (MihirBagwe) •...
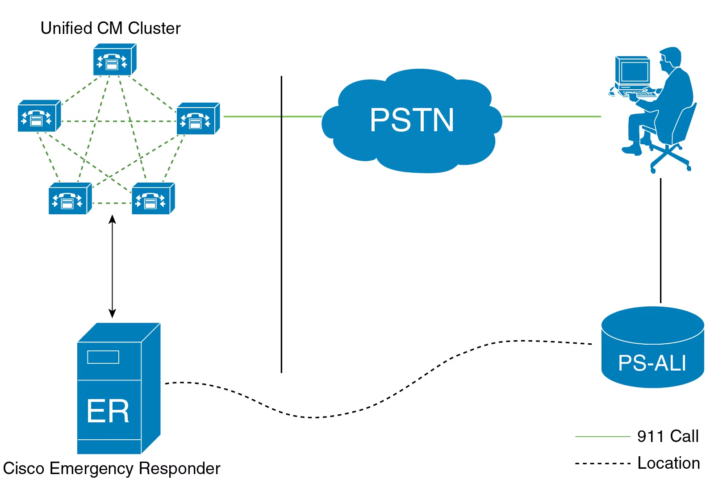
Cisco Plugs Gaping Hole in Emergency Responder Software – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine A remotely exploitable vulnerability in the Cisco Emergency Responder software could allow an unauthenticated attacker to log in to an...
GitHub Improves Secret Scanning Feature With Expanded Token Validity Checks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Software development giant GitHub on Wednesday announced an enhancement to its secret scanning feature, now allowing users to check the...
BlackBerry to Split Cybersecurity, IoT Business Units – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Canadian tech giant BlackBerry has announced plans to split its cybersecurity and IOT (Internet of Things) businesses and pursue an...
Red Cross Publishes Rules of Engagement for Hacktivists During War – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The International Committee of the Red Cross (ICRC) is urging hacking groups involved in conflict during war to abide by...
CISA, NSA Publish Guidance on IAM Challenges for Developers, Vendors – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US cybersecurity agency CISA and the NSA have published new guidance on implementing identity and access management (IAM), focusing...
Linux Foundation Announces OpenPubkey Open Source Cryptographic Protocol – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Linux Foundation on Wednesday announced OpenPubkey, an open source cryptographic protocol that should help boost supply chain security. OpenPubkey...
Qakbot Hackers Continue to Push Malware After Takedown Attempt – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The cybercriminals behind the Qakbot malware have been observed distributing ransomware and backdoors following the recent infrastructure takedown attempt by...
Shocking AI deepfakes convincingly imitate celebrities & fool online fans – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Are you prepared for a world in which a malicious entity creates manipulative, convincing deepfake videos of your top...
Addressing the People Problem in Cybersecurity – Source: www.securityweek.com
Source: www.securityweek.com – Author: Marc Solomon October marks the 20th anniversary of Cybersecurity Awareness Month – an annual campaign led by the Cybersecurity and Infrastructure Agency...
Hundreds Download Malicious NPM Package Capable of Delivering Rootkit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A recently observed malicious campaign has relied on typosquatting to trick users into downloading a malicious NPM package that would...
Sony Confirms Data Stolen in Two Recent Hacker Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Sony this week shared information on the impact of two recent unrelated hacker attacks believed to have been carried out...
SHARED INTEL Q&A: My thoughts and opinions about cyber threats — as discussed with OneRep – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Erin Kapcynski Editor’s note: I recently had the chance to participate in a discussion about the overall state of privacy...
Security Information and Event Management (SIEM). What It Is and How It Works. – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Elena Georgescu Wondering what is SIEM, what are its benefits and limitations, and what are the best practices you can apply for...
Political Disinformation and AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Elections around the world are facing an evolving threat from foreign actors, one that involves artificial intelligence. Countries trying to...
CISA and NSA Tackle IAM Security Challenges in New Report – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The CISA and the National Security Agency (NSA) have published new guidelines in a report called “Identity and Access Management: Developer...
Critical Glibc Bug Puts Linux Distributions at Risk – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers from the Qualys Threat Research Unit (TRU) have uncovered a new buffer overflow vulnerability within the GNU C Library’s...
China Poised to Disrupt US Critical Infrastructure with Cyber-Attacks, Microsoft Warns – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Chinese threat actors are positioning themselves to deploy major cyber-attacks against US critical national infrastructure (CNI) in the event of an...
Record Numbers of Ransomware Victims Named on Leak Sites – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The number of victims named on ransomware leak sites reached “unprecedented levels” in the four months from March to June 2023,...
Scammers Impersonate Companies to Steal Cryptocurrency from Job Seekers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have discovered a major new scam operation designed to trick job seekers into parting with cryptocurrency, by getting them...
US Government Proposes SBOM Rules for Contractors – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Three US government agencies have proposed new rules for federal contractors which would require them to develop and maintain a software...
GoldDigger Android Trojan Drains Victim Bank Accounts – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have discovered a prolific new Android Trojan designed to covertly harvest user information including banking app credentials, with a...