The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Month: October 2023
The Coming AI Hackers – Council for the responsible use of AI by Bruce Schneier
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SANS DFIR – CHEAT SHEETS & NOTEBOOKS – The most complete reference !!!
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Microsoft Entra – The Comprensive Guide to Secure Azure AD & User Identities by Mohamed Mokhtar & Microsoft Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Governance Framework for National Cybersecurity Strategies by European Union Agency for Cybersecurity – enisa
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Risk Report 2023 by RiskLens
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SANS Institute – Incident Handler´s Handbook by Patrick Kral
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Russia´s Cyber Tactics – Lessons Learnead 2022 by Information Protection of Ukraine
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Global Cybersecurity Outlook 2023 Insight Report by WEF – World Economic Forum in collaboration with Accenture
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Digital Forensics and Incident Response (DFIR) Framework for Operational Technology (OT) by NIST – Eran Salfati and Michael Pease
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Insider Threat Mitigation Guide by Cybersecurity Insfrastructure Security Agency
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ANTI-FRAUD PLAYBOOK – THE BEST DEFENSES IS A GOOD OFFENSE BY ACFE – FRAUD RISK GOVERNANCE – Playbooks are not only for Cyber, they are also to combat business fraud.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ROUTING SECURITY – BGP INCIDENTS, MITIGATION, TECHNIQUES AND POLICY ACTIONS BY OECD
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
BASELINE CYBER SECURITY CONTROLS FOR SMALL AND MEDIUM ORGANIZATIONS V1.2 by Canadian Centre for CYBERSECURITY
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO2CISO Toolbox Series – Cyber Security Blogs / Cyber Security RSS Feeds List –
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
#EKOPARTY2022 – Ekoparty is a technical security conference born in 2001. +3000 guests, single track, workshops, trainings + ❤ – World-class experts, new breakthroughs, and professional training taught by the most recognized infosec professionals.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Protocols – SSL vs TLS – ALL YOU NEED TO KNOW.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Security Toolkit for Boards – Helping board members to get to grips with cyber security by NCSC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
11 STRATEGIES OF A WORLD-CLASS CYBERSECURITY OPERATIONS CENTERS HIGHLIGHTS BY MITRE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THE 2022 HORNETSECURITY RANSOMWARE ATTACKS ANALYSIS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Telecom Cybersecurity – 5G Protection Use Cases by SecurityGen
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SECURITY OF THE DOMAIN NAME SYSTEM (DNS) – AN INTRODUCTION FOR POLICY MAKERS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ESSET THREAT REPORT T2 2022
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THE DEFENDER´S ADVANTAGE – A GUIDE TO ACTIVATING CYBER DEFENSE BY MANDIANT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
MAPPING THE RANSOMWARE PAYMENT ECOSYSTEM BY ZOE BRAMMER – IST Institute of Security and Technology
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DevOps Tools and Insfrastructure Under Attack by Wallarm
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Manual on Social Media Intelligence (SOCMINT) for Law Enforcement Agencies by National Cyber Crume Research & Innovation Centre – Government of India
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
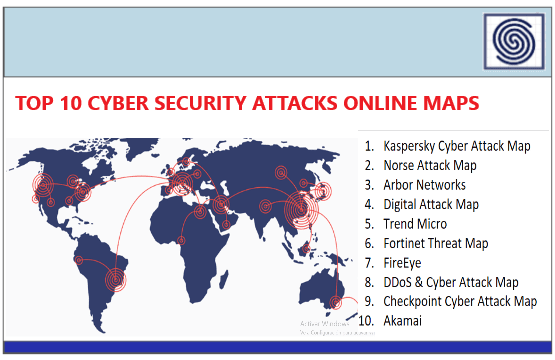
Top 10 Cyber Attack Maps to See Digital Threats 2022 by Tushar Subhra Dutta – Cyber Security News.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DevSecOps Fundamentals Guidebook – Tools & Activities by American Deparment of Defense
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NSA CYBERSECURITY – YEAR IN REVIEW REPORT 2022. You must read IT !
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...