Source: thehackernews.com – Author: . Sep 25, 2023THNCyber Attack / Phishing Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as...
Day: September 25, 2023
Are You Willing to Pay the High Cost of Compromised Credentials? – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 25, 2023The Hacker NewsPassword Security / Cybersecurity Weak password policies leave organizations vulnerable to attacks. But are the standard password...
6 steps to stop ransomware from taking you hostage – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Ransomware is a growing threat, especially for US-based organizations. Cyber criminals increasingly focus on “triple extortion” ransomware attacks, which...
GUEST ESSAY: A roadmap for the finance teams at small businesses to improve cybersecurity – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Neil Taurins If you’re a small business looking for the secret sauce to cybersecurity, the secret is out: start with...
How Will SEC Rules Affect Reporting, Tracking of Incidents? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Security Operations , Standards, Regulations & Compliance TrustedSec’s Alex Hamerstone on New US Securities and Exchange Commission Rules...
Cloud Smart Roadshow Irving (Dallas): Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Cloud Security , Next-Generation Technologies & Secure Development Presented by VMware 300 Minutes...
Cloud Smart Roadshow San Diego: Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Cloud Data Security & Resilience , Next-Generation Technologies & Secure Development Presented by VMware ...
Data Breach Toll Tied to Clop Group’s MOVEit Attacks Surges – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response 2,050 Organizations Affected After Data Stolen From Secure File-Sharing Software...
Cloud Smart Roadshow San Jose: Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Presented by VMware 300 Minutes Learn how to navigate the cloud landscape with VMware, your compass for...
Cloud Smart Roadshow Los Angeles: Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Presented by VMware 300 Minutes Learn how to navigate the cloud landscape with VMware, your compass for...
Stealthy APT Gelsemium Seen Targeting Southeast Asian Government – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A stealthy advanced persistent threat (APT) actor known as Gelsemium has been observed targeting a government entity in Southeast Asia...
Nigerian Pleads Guilty in US to Million-Dollar BEC Scheme Role – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A Nigerian national residing in South Africa last week pleaded guilty in court in the United States to his role...
900 US Schools Impacted by MOVEit Hack at National Student Clearinghouse – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The National Student Clearinghouse, an educational nonprofit that provides reporting, verification, and research services to colleges and universities in North...
City of Dallas Details Ransomware Attack Impact, Costs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The City of Dallas has announced that an $8.5 million budget has been approved to support the restoration of its...
In-the-Wild Exploitation Expected for Critical TeamCity Flaw Allowing Server Takeover – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A critical vulnerability in the TeamCity CI/CD server could be exploited remotely, without authentication, to execute arbitrary code and gain...
Predator Spyware Delivered to iOS, Android Devices via Zero-Days, MitM Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Predator spyware has been delivered to iPhones and Android devices using iOS and Chrome zero-day vulnerabilities and man-in-the-middle (MitM)...
Internet and Email Usage Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This policy from TechRepublic Premium sets forth guidelines for the use of the internet, as well as internet-powered communication services, including email,...
Point of Sale Security Guide and Checklist – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: For retail businesses, the POS system is arguably their most important IT system. This TechRepublic Premium guide, and the accompanying checklist, will...
Sophisticated APT Clusters Target Southeast Asia – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Unit 42 researchers have unveiled a web of complex cyber-espionage attacks targeting a government in Southeast Asia. While initially thought to...
China-Linked EvilBamboo Targets Mobiles – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A prolonged and ongoing cyber-espionage campaign by the threat actor known as EvilBamboo (formerly Evil Eye) has been uncovered by cybersecurity...
Voting Equipment Giants Team Up For Security – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 In anticipation of the upcoming 2024 election, major US voting equipment manufacturers have announced an initiative to collaborate with cybersecurity experts...
Alert! Patch your TeamCity instance to avoid server hack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Alert! Patch your TeamCity instance to avoid server hack Pierluigi Paganini September 25, 2023 Experts warn of a critical vulnerability...
Is Gelsemium APT behind a targeted attack in Southeast Asian Government? – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Is Gelsemium APT behind a targeted attack in Southeast Asian Government? Pierluigi Paganini September 25, 2023 A stealthy APT group...
Nigerian National pleads guilty to participating in a millionaire BEC scheme – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Nigerian National pleads guilty to participating in a millionaire BEC scheme Pierluigi Paganini September 25, 2023 A Nigerian national pleaded...
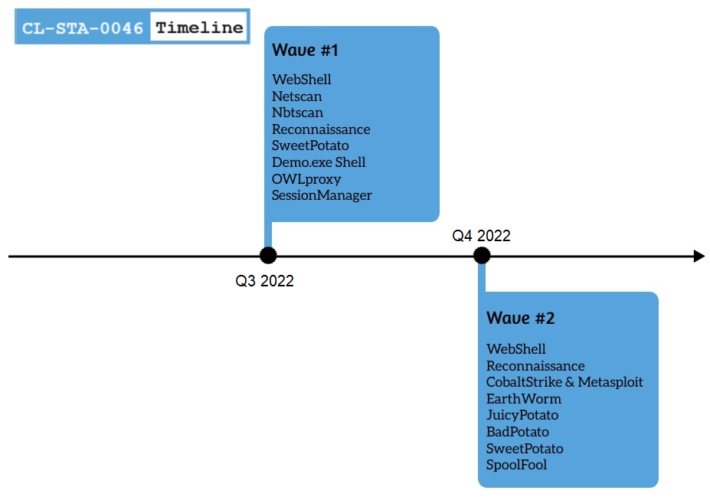
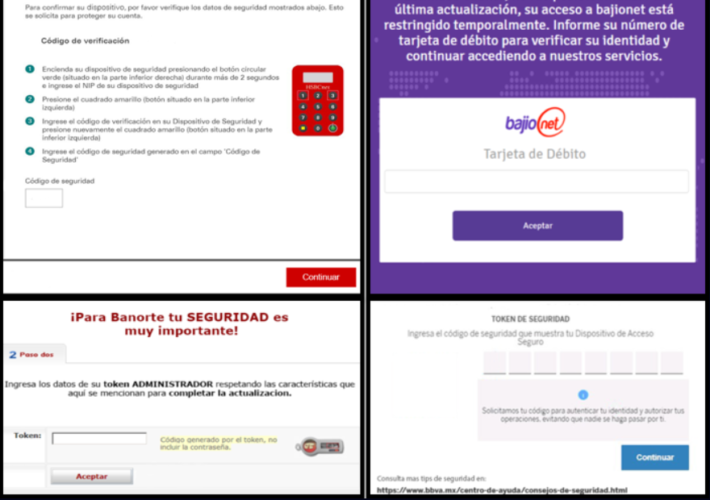
New variant of BBTok Trojan targets users of +40 banks in LATAM – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini New variant of BBTok Trojan targets users of +40 banks in LATAM Pierluigi Paganini September 25, 2023 A new variant...
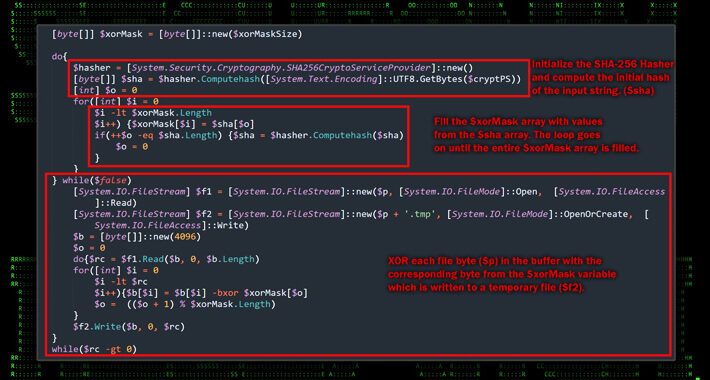
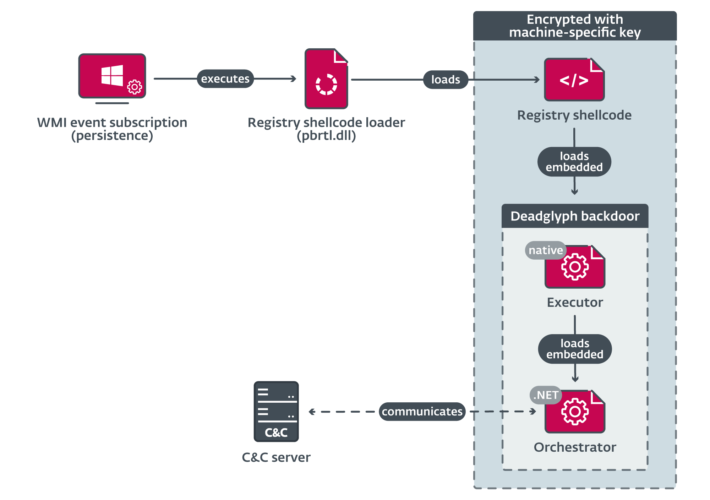
Deadglyph, a very sophisticated and unknown backdoor targets the Middle East – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Deadglyph, a very sophisticated and unknown backdoor targets the Middle East Pierluigi Paganini September 24, 2023 Researchers discovered a previously...
Web3 Platform Mixin Network Hit by $200m Crypto Hack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Hong Kong-based decentralized finance (DeFi) project Mixin Network lost around $200m in cryptocurrency in what could already be one of the...
BEC Scammer Pleads Guilty to Part in $6m Scheme – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Nigerian extradited to the US had pleaded guilty to his part in a multimillion-dollar business email compromise (BEC) conspiracy. Kosi...
Researchers Spot Novel “Deadglyph” Backdoor – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have revealed a sophisticated new modular backdoor which they believe is the work of the United Arab Emirates’ Stealth...
Almost 900 US Schools Breached Via MOVEit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The MOVEit saga continues to claim more victims, after an education non-profit revealed that 890 US schools signed up with it had...