Source: www.techrepublic.com – Author: Franklin Okeke Image: Postmodern Studio/Adobe Stock Cisco announced yesterday its intention to acquire Splunk, a renowned name in data observability and security,...
Day: September 22, 2023
ProtonVPN Review (2023): Features, Pricing and Alternatives – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares ProtonVPN Fast facts Our rating: 4.0 stars out of of 5 Pricing: Starts at $5.99 per month Key features Swiss-protected...
New Variant of Banking Trojan BBTok Targets Over 40 Latin American Banks – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 22, 2023THNMalware / Cyber Threat An active malware campaign targeting Latin America is dispensing a new variant of a banking...
How to Interpret the 2023 MITRE ATT&CK Evaluation Results – Source:thehackernews.com
Source: thehackernews.com – Author: . Thorough, independent tests are a vital resource for analyzing provider’s capabilities to guard against increasingly sophisticated threats to their organization. And...
UK Approves Commercial Data Transfer Deal With US – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 General Data Protection Regulation (GDPR) , Geo Focus: The United Kingdom , Geo-Specific Agreement Says Organizations Don’t Need to Assess Risk...
Cloud Smart Roadshow Toronto: Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Presented by VMware 300 Minutes Learn...
Cloud Smart Roadshow Montreal : Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Presented by VMware 300 Minutes Learn...
MGM Resorts Says Hotels ‘Operating Normally’ After Attack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware But Digital Room Keys Still Unavailable; Slot Machines Have ‘Intermittent Issues’ Mathew J. Schwartz (euroinfosec)...
Cloud Smart Roadshow Tallahassee : Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Data Security & Resilience , Security Operations Presented by VMware 300 Minutes Learn how to navigate...
Cloud Smart Roadshow Minneapolis: Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Application Security , Cloud Data Security & Resilience , Cloud Security 300 Minutes Learn how to navigate...
Dutch Police Warns Users of Credentials Leak Site – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime 400 Potential WeLeakInfo Patrons Warned of Legal Costs of Criminal Wrongdoing Akshaya Asokan (asokan_akshaya) •...
Feds Warn About Snatch Ransomware – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware US Agency Advisory Sheds Light on the Group’s Activities Prajeet Nair (@prajeetspeaks) • September 21,...
7 Best Sophos Alternatives & Competitors in 2023 [Features, Pricing & Reviews] – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal In the ever-evolving cybersecurity landscape, businesses constantly seek robust security solutions to protect their digital assets. Sophos, a well-known name...
Apple Fixes 3 New Actively Exploited Zero-Day Vulnerabilities – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Apple released an emergency security update to patch three newly identified zero-days exploited actively by threat actors. The vulnerabilities affected...
New Threat Group: Sandman Targets Telecommunication Companies Across the World With Infostealers – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu A previously unknown threat group known as “Sandman” is making its presence felt. The group uses a modular information-stealing malware...
In Other News: New Analysis of Snowden Files, Yubico Goes Public, Election Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
China’s Offensive Cyber Operations in Africa Support Soft Power Efforts – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Chinese state-sponsored threat groups have targeted telecommunications, financial and government organizations in Africa in support of Beijing’s soft power agenda...
Air Canada Says Employee Information Accessed in Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Air Canada, the largest airline in the country, this week announced that the personal information of some employees was accessed...
BIND Updates Patch Two High-Severity DoS Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Internet Systems Consortium (ISC) has released security updates to address two remotely exploitable denial-of-service (DoS) vulnerabilities in the DNS...
Faster Patching Pace Validates CISA’s KEV Catalog Initiative – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Known Exploited Vulnerabilities (KEV) Catalog maintained by the US cybersecurity agency CISA has led to significant improvements in federal...
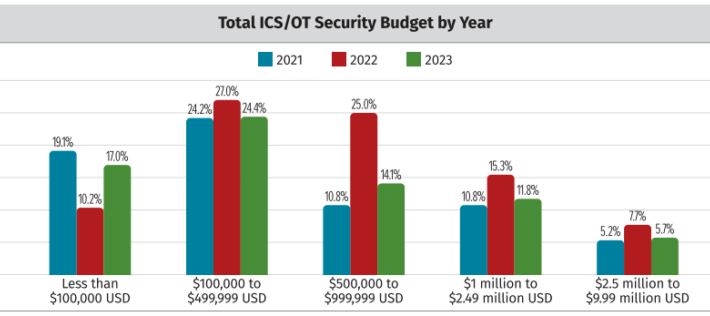
SANS Survey Shows Drop in 2023 ICS/OT Security Budgets – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A survey conducted by the SANS Institute shows that the budgets allocated by organizations for the security of industrial control...
Apple Patches 3 Zero-Days Likely Exploited by Spyware Vendor to Hack iPhones – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Apple announced on Thursday that its latest operating system updates patch three new zero-day vulnerabilities. Based on the previous work...
CISA and NFL Collaborate to Secure Super Bowl LVIII – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the National Football League (NFL), Allegiant Stadium and Super Bowl LVIII...
Over 700 Dark Web Ads Offer DDoS Attacks Via IoT in 2023 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The year 2023 has seen a surge of over 700 advertisements on the dark web offering Distributed Denial of Service (DDoS)...
Elusive Sandman APT Targets Telecom Giants With LuaJIT Toolkit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers at SentinelLabs, in collaboration with QGroup, have unveiled a new threat actor known as Sandman. This unidentified group has...
7 step checklist to avoid common cloud security misconfigurations – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Cloud computing provides a flexible and cost-effective way to access almost limitless compute power and data storage, ensuring that...
GUEST ESSAY: Caring criminals — why some ransomware gangs now avoid targeting hospitals – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Zac Amos Ransomware is a significant threat to businesses worldwide. There are many gangs that work together to orchestrate increasingly...
#mWISE: Why Zero Days Are Set for Highest Year on Record – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Will the “hot zero-day summer” we’ve been experiencing in 2023 become the new normal? With 62 zero-day vulnerabilities exploited since January,...
US Government IT Staffer Arrested on Espionage Charges – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A US government contractor working as an IT administrator at the State department is facing a maximum penalty of death or...
UK Security Agency Publishes New Crypto Designs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s National Cyber Security Centre (NCSC) looked to burnish its tech credentials this week with the publication of new research...












![7-best-sophos-alternatives-&-competitors-in-2023-[features,-pricing-&-reviews]-–-source:-heimdalsecurity.com](https://ciso2ciso.com/wp-content/uploads/2023/09/80749/7-best-sophos-alternatives-competitors-in-2023-features-pricing-reviews-source-heimdalsecurity-com.png)