Unmanned aircraft systems (UAS), more commonly known as “drones,” are automated airborne vehicles sometimes described as flying robots or flying cell phones or computers. Drones have...
Day: September 7, 2023
API Vulnerabilities: 74% of Organizations Report Multiple Breaches – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 API security company Traceable has unveiled its 2023 State of API Security Report. In collaboration with the Ponemon Institute, the study...
DGA Behavior Shifts Raise Cybersecurity Concerns – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Researchers at Akamai have unearthed a concerning shift in the behavior of dynamically seeded Domain Generation Algorithm (DGA) families within Domain...
Zero-Day Flaw Exposes Atlas VPN User IPs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Reddit user known as “Educational-Map-8145” has exposed a critical zero-day flaw affecting the Linux client of Atlas VPN, a popular virtual...
UK and US Sanction 11 Russians Tied to Trickbot/Conti Ransomware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US and the UK have sanctioned 11 individuals accused of being linked with the Trickbot malware and the Conti ransomware...
IBM Reports Patient Data Breach at Johnson & Johnson Subsidiary – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Sensitive patient data may have been accessed following a breach of the Janssen CarePath platform, a subsidiary of pharmaceutical giant Johnson...
Chinese Hacker Steals Microsoft Signing Key, Spies on US Government – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A China-based threat actor gained access to a Microsoft account (MSA) cryptographic key, as early as 2021, and used it to...
Apple discloses 2 new actively exploited zero-day flaws in iPhones, Macs – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Apple discloses 2 new actively exploited zero-day flaws in iPhones, Macs Pierluigi Paganini September 07, 2023 Apple rolled out emergency...
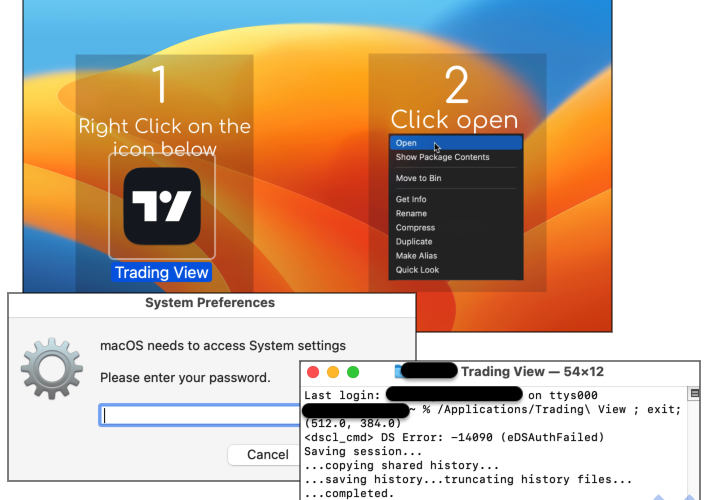
A malvertising campaign is delivering a new version of the macOS Atomic Stealer – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A malvertising campaign is delivering a new version of the macOS Atomic Stealer Pierluigi Paganini September 07, 2023 Researchers spotted...
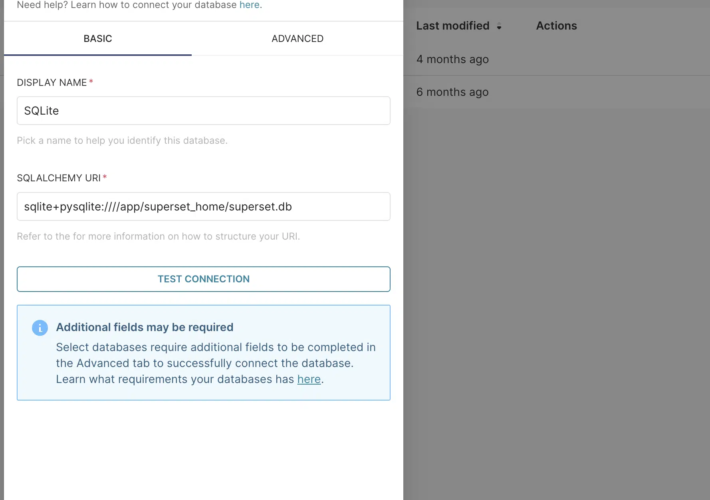
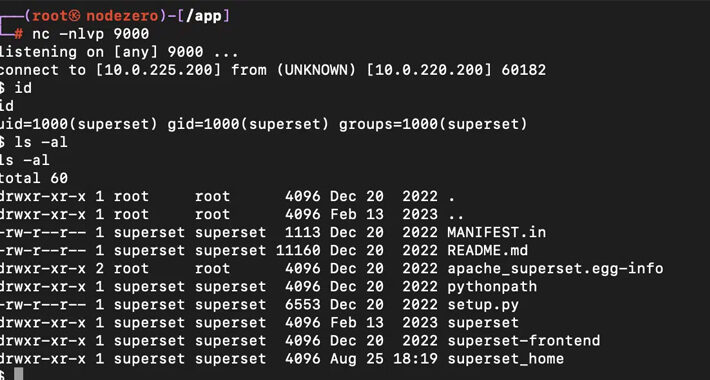
Two flaws in Apache SuperSet allow to remotely hack servers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Two flaws in Apache SuperSet allow to remotely hack servers Pierluigi Paganini September 07, 2023 A couple of security vulnerabilities...
Chinese cyberspies obtained Microsoft signing key from Windows crash dump due to a mistake – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Chinese cyberspies obtained Microsoft signing key from Windows crash dump due to a mistake Pierluigi Paganini September 07, 2023 Microsoft...
CISA warns of critical Apache RocketMQ bug exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added to its catalog of known exploited vulnerabilities (KEV) a critical–severity...
Iranian hackers breach US aviation org via Zoho, Fortinet bugs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney State-backed hacking groups have breached a U.S. aeronautical organization using exploits targeting critical Zoho and Fortinet vulnerabilities, a...
Google is enabling Chrome real-time phishing protection for everyone – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Google announced today that it is deprecating the standard Google Chrome Safe Browsing feature and moving everyone to its Enhanced...
Apple zero-click iMessage exploit used to infect iPhones with spyware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Citizen Lab says two zero-days fixed by Apple today in emergency security updates were actively abused as part of a...
Cisco BroadWorks impacted by critical authentication bypass flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A critical vulnerability impacting the Cisco BroadWorks Application Delivery Platform and Cisco BroadWorks Xtended Services Platform could allow remote attackers...
Google Looker Studio abused in cryptocurrency phishing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cybercriminals are abusing Google Looker Studio to create counterfeit cryptocurrency phishing websites that phish digital asset holders, leading to account...
Microsoft: North Korean hackers target Russian govt, defense orgs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says North Korean hacking groups have breached multiple Russian government and defense targets since the start of the year....
The Hacker Tool to Get Personal Data from Credit Bureaus – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The new site 404 Media has a good article on how hackers are cheaply getting personal information from credit bureaus:...
Apple discloses 2 new zero-days exploited to attack iPhones, Macs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Apple released emergency security updates to fix two new zero-day vulnerabilities exploited in attacks targeting iPhone and Mac users, for...
Google: State hackers attack security researchers with new zero-day – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google’s Threat Analysis Group (TAG) says North Korean state hackers are again targeting security researchers in attacks using at least...
Windows cryptomining attacks target graphic designer’s high-powered GPUs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney Cybercriminals are leveraging a legitimate Windows tool called ‘Advanced Installer’ to infect the computers of graphic designers with...
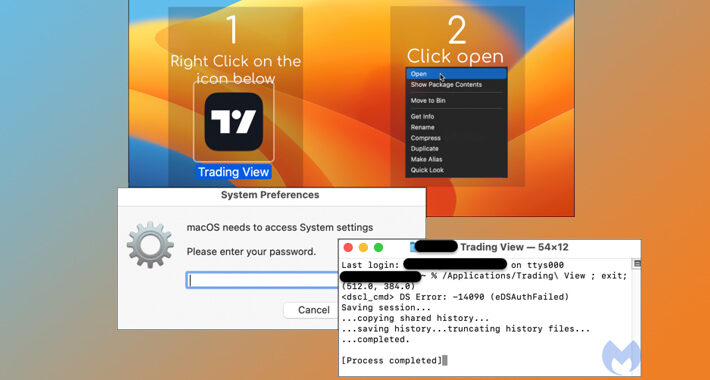
Mac Users Beware: Malvertising Campaign Spreads Atomic Stealer macOS Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 07, 2023THNMalvertising / Endpoint Security A new malvertising campaign has been observed distributing an updated version of a macOS stealer...
The State of the Virtual CISO Report: MSP/MSSP Security Strategies for 2024 – Source:thehackernews.com
Source: thehackernews.com – Author: . By the end of 2024, the number of MSPs and MSSPs offering vCISO services is expected to grow by almost 5...
Alert: Apache Superset Vulnerabilities Expose Servers to Remote Code Execution Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 07, 2023THNServer Security / Vulnerability Patches have been released to address two new security vulnerabilities in Apache Superset that could...
Minneapolis School District Reveals Full Extent of Data Breach – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa Minneapolis Public Schools (MPS) recently disclosed the full extent of a data breach from earlier this year, affecting more than...
Vulnerabilities Uncovered: Critical Remote Code Execution Risks in ASUS Routers – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa ASUS routers have come under the spotlight due to three critical remote code execution vulnerabilities. These vulnerabilities pose a significant...
Thousands of dollars stolen from Texas ATMs using Raspberry Pi – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley A Texas court has heard how last month a gang of men used a Raspberry Pi device to steal thousands...
Smashing Security podcast #338: Catfishing services, bad sports, and another cockup – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley AI news is bad news, an online service to catch your cheating partner, and an IoT-enabled dick cage fails to...
Check Point Buys Startup Atmosec to Secure SaaS Applications – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Integration on Tap With Perimeter 81, Harmony Connect to Deliver Single-Vendor SASE Michael Novinson (MichaelNovinson) • September 6, 2023 ...