Source: heimdalsecurity.com – Author: Adelina Deaconu Due to the constantly changing nature of cyber threats, businesses must implement strong security solutions. Here is where CrowdStrike competitors...
Month: August 2023
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
ESET Threat Report H1 2023 – Source:
Source: – Author: 1 A view of the H1 2023 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and...
Emotet: sold or on vacation? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Originally a banking trojan, Emotet later evolved into a full-blown botnet and went on to become one of the most dangerous cyberthreats...
What’s up with Emotet? – Source:
Source: – Author: 1 A brief summary of what happened with Emotet since its comeback in November 2021 Original Post URL: Category & Tags: – Views:...
Deepfaking it: What to know about deepfake-driven sextortion schemes – Source:
Source: – Author: 1 Criminals increasingly create deepfake nudes from people’s benign public photos in order to extort money from them, the FBI warns Original Post...
Russian Cyber Adversary BlueCharlie Alters Infrastructure in Response to Disclosures – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 02, 2023THNCyber Threat / Hacking A Russa-nexus adversary has been linked to 94 new domains, suggesting that the group is...
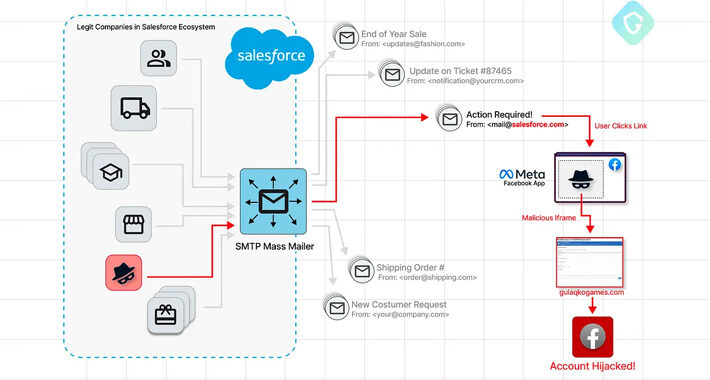
Phishers Exploit Salesforce’s Email Services Zero-Day in Targeted Facebook Campaign – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 02, 2023THNVulnerability / A sophisticated Facebook phishing campaign has been observed exploiting a zero-day flaw in Salesforce’s email services, allowing...
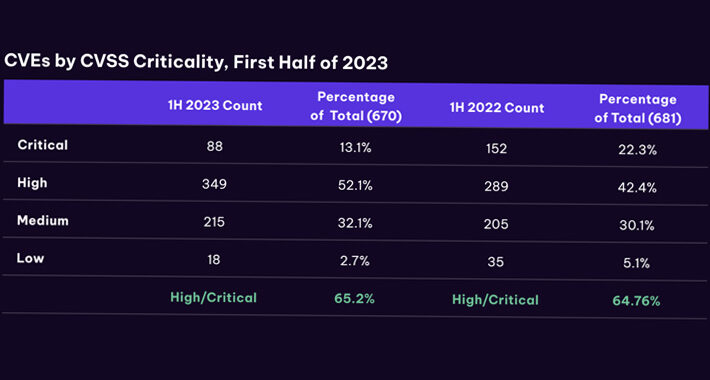
Industrial Control Systems Vulnerabilities Soar: Over One-Third Unpatched in 2023 – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 02, 2023THNICS/SCADA Security About 34% of security vulnerabilities impacting industrial control systems (ICSs) that were reported in the first half...
Top Industries Significantly Impacted by Illicit Telegram Networks – Source:thehackernews.com
Source: thehackernews.com – Author: . In recent years the rise of illicit activities conducted within online messaging platforms has become a growing concern for countless industries....
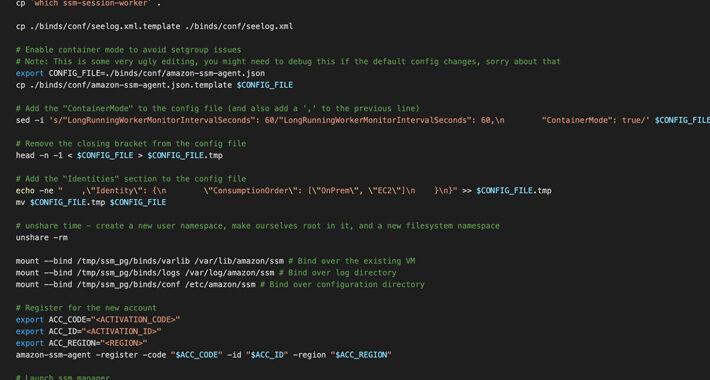
Researchers Uncover AWS SSM Agent Misuse as a Covert Remote Access Trojan – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 02, 2023THNCloud Security / Cyber Threat Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services (AWS) that...
Iranian Company Cloudzy Accused of Aiding Cybercriminals and Nation-State Hackers – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 02, 2023THNRansoware / Cyber Crime Services offered by an obscure Iranian company known as Cloudzy are being leveraged by multiple...
Norwegian Entities Targeted in Ongoing Attacks Exploiting Ivanti EPMM Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 02, 2023THNVulnerability / Cyber Attack Advanced persistent threat (APT) actors exploited a recently disclosed critical flaw impacting Ivanti Endpoint Manager...
Hackers use new malware to breach air-gapped devices in Eastern Europe – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Chinese state-sponsored hackers have been targeting industrial organizations with new malware that can steal data from air-gapped systems. Air-gapped systems...
Threat actors abuse Google AMP for evasive phishing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers are warning of increased phishing activity that abuses Google Accelerated Mobile Pages (AMP) to bypass email security measures...
CISA issues new warning on actively exploited Ivanti MobileIron bugs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today of state hackers exploiting two flaws in Ivanti’s Endpoint Manager...
Electric vehicle cyber security risks and best practices (2023) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Micki Boland is a global cyber security warrior and evangelist with Check Point’s Office of the CTO. Micki has over 20 years...
News Alert: Devo, Cybermindz partner to improve mental health of cybersecurity pros in the U.S. – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Cambridge, Mass. – Aug. 1, 2023 – Devo Technology, the cloud-native security analytics company, today announced its financial support for Cybermindz, a...
News Alert: Guardz uncovers new macOS malware – Hidden Virtual Network Computing (hVNC) – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel, Aug. 1, 2023 – Guardz, the cybersecurity company securing and insuring SMEs, today disclosed the existence of a Hidden Virtual...
News Alert: AppViewX – EMA study finds 79 percent of SSL/TLS certificates vulnerable to MiTM attacks – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido New York, NY, Aug. 1, 2023– AppViewX, a leader in automated machine identity management (MIM) and application infrastructure security, today announced the results...

![8-best-crowdstrike-competitors-&-alternatives-in-2023-[features,-pricing-&-reviews]-–-source:-heimdalsecurity.com](https://ciso2ciso.com/wp-content/uploads/2023/08/72007/8-best-crowdstrike-competitors-alternatives-in-2023-features-pricing-reviews-source-heimdalsecurity-com-710x360.png)