Source: www.govinfosecurity.com – Author: 1 Business Email Compromise (BEC) , Fraud Management & Cybercrime Scammers Used Malware and Spoofed Domain Name to Trick UK Financial Services...
Month: August 2023
Protection is No Longer Straightforward – Why More Cybersecurity Solutions Must Incorporate Context – Source: www.securityweek.com
Source: www.securityweek.com – Author: Matt Wilson It is well known that when it comes to cybersecurity, today’s modern network demands solutions that go beyond simple one-size-fits-all...
Identity-Based Attacks Soared in Past Year: Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs CrowdStrike on Tuesday released its 2023 Threat Hunting Report, warning that threat actors have doubled down on identity-based attacks over...
ICS Patch Tuesday: Siemens Fixes 7 Vulnerabilities in Ruggedcom Products – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Siemens released a dozen advisories covering more than 30 vulnerabilities this Patch Tuesday, but Schneider Electric has only published one...
UK Think Tank Proposes Greater Ransomware Reporting From Cyberinsurance to Government – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Royal United Services Institute (RUSI) is an independent UK think tank that has been in existence since 1831. It...
Black Hat Preview: The Business of Cyber Takes Center Stage – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine LAS VEGAS — Once the undisputed hub for the most groundbreaking technical security research, the Black Hat conference no longer...
How ransomware attacks can be a test of leadership – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Antoine Calendrier, Head of Crisis and Trust Services for Asia Pacific, Edelman. Ransomware attacks are on the rise and they...
Microsoft Shares Guidance and Resources for AI Red Teams – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Microsoft on Monday published a summary of its artificial intelligence (AI) red teaming efforts, and shared guidance and resources that...
Cyberinsurance Firm Resilience Raises $100 Million to Expand Its Cyber Risk Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Resilience Cyber Insurance Solutions has raised $100 million through a Series D funding round to support global expansion of its cyber...
North Korean Hackers Targeted Russian Missile Developer – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A Russian defense industrial base organization specializing in missiles and military spacecraft appears to have been targeted by two important...
News alert: SandboxAQ launches new open source framework to simplify cryptography management – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Palo Alto, Calif., Aug. 8, 2023 – SandboxAQ today announced Sandwich, an open source framework and meta-library of cryptographic algorithms that simplifies modern...
#BHUSA: Ransomware Threat Activity Cluster Uncovered – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Sophos X-Ops has exposed a new connection between seemingly unrelated ransomware attacks. The findings, based on several ransomware attacks in the...
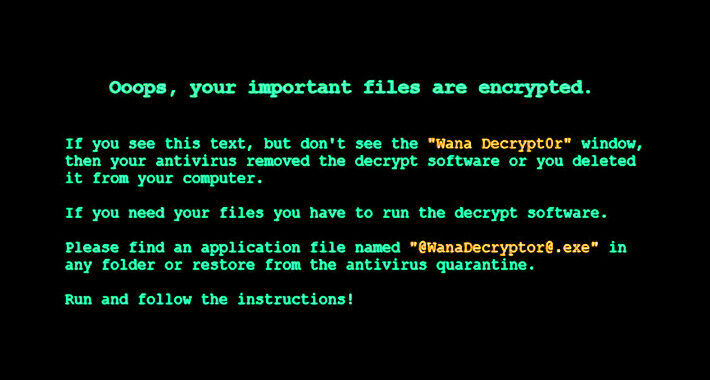
Vietnamese-Origin Ransomware Operation Mimics WannaCry Traits – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 An unidentified threat actor, reportedly originating from Vietnam, has been observed engaging in a ransomware campaign that commenced no later than...
UK Voters’ Data Exposed in Electoral Commission Cyber-Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s Electoral Commission has revealed it has been the victim of a “complex cyber-attack,” exposing the personal details of millions...
#BHUSA: Identity Compromise the Cause of Most Breaches – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Identity theft has established itself as the main initial access method for threat actors, according to CrowdStrike. In its 2023 Threat...
North Korean Hackers Compromise Russian Missile Maker – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have discovered a likely North Korean cyber-espionage campaign targeting the IT network of a Russian manufacturer of intercontinental ballistic...
Two-Thirds of UK Sites Vulnerable to Bad Bots – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The majority (66%) of UK websites are unable to block simple bot attacks, exposing their businesses to fraud, account compromise and...
Over 200 Million Brits Have Data Compromised in Four Years – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 UK organizations lost billions in data breaches between 2019 and 2022, with hundreds of millions of their customers suffering compromise of...
43 Android apps in Google Play with 2.5M installs loaded ads when a phone screen was off – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts found 43 Android apps in Google Play with 2.5 million installs that displayed advertisements while a phone’s screen was...
Zoom trains its AI model with some user data, without giving them an opt-out option – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Zoom changed its terms of service requiring users to allow AI to train on all their data without giving them...
North Korea compromised Russian missile engineering firm NPO Mashinostroyeniya – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Two North Korea-linked APT groups compromised the infrastructure of the major Russian missile engineering firm NPO Mashinostroyeniya. Cybersecurity firm SentinelOne...
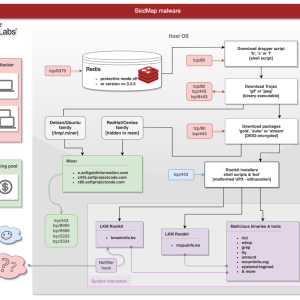
A new sophisticated SkidMap variant targets unsecured Redis servers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A new campaign targets Redis servers, this time the malware employed in the attacks is a new variant of the...
You Can’t Rush Post-Quantum-Computing Cryptography Standards – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier I just read an article complaining that NIST is taking too long in finalizing its post-quantum-computing cryptography standards. This process...
Microsoft Signing Key Stolen by Chinese – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier A bunch of networks, including US Government networks, have been hacked by the Chinese. The hackers used forged authentication tokens...
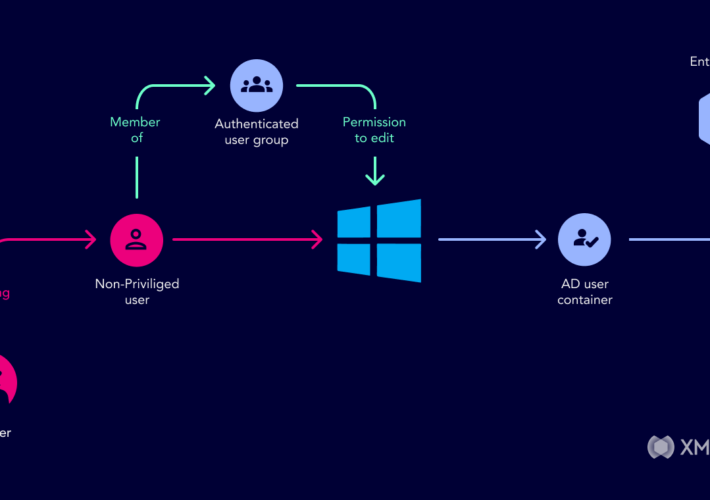
Understanding Active Directory Attack Paths to Improve Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning and...
New Yashma Ransomware Variant Targets Multiple English-Speaking Countries – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 08, 2023THNEndpoint Security / Malware An unknown threat actor is using a variant of the Yashma ransomware to target various...
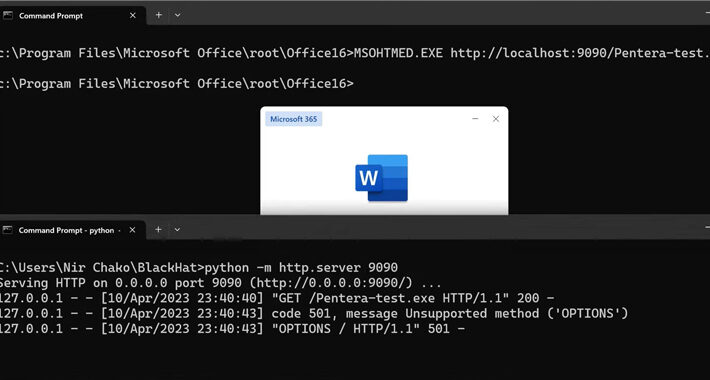
LOLBAS in the Wild: 11 Living-Off-The-Land Binaries That Could Be Used for Malicious Purposes – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 08, 2023THNMalware / Cyber Threat Cybersecurity researchers have discovered a set of 11 living-off-the-land binaries-and-scripts (LOLBAS) that could be maliciously...
Keep your sensitive data secure by using Encrypted Forms 2.0 from Jotform – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Graham Cluley Security News is sponsored this week by the folks at Jotform. Thanks to the great team there for...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....