Source: www.securityweek.com – Author: Ionut Arghire A widespread phishing campaign ongoing since May 2023 has been targeting organizations in various industries, including a major US energy...
Month: August 2023
Cisco Patches High-Severity Vulnerabilities in Enterprise Applications – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco on Wednesday announced security updates for several enterprise applications to patch high-severity vulnerabilities leading to privilege escalation, SQL injection,...
Thousands of Systems Turned Into Proxy Exit Nodes via Malware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat actors are leveraging access to malware-infected Windows and macOS systems to deploy a proxy application, AT&T’s Alien Labs reports....
CISA Releases Cyber Defense Plan to Reduce RMM Software Risks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday announced the release of a strategic plan to help critical infrastructure...
Cybersecurity M&A Roundup for August 1-15, 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Twenty-five cybersecurity-related merger and acquisition (M&A) deals were announced in the first half of August 2023. The number of transactions...
Exploitation of Citrix ShareFile Vulnerability Spikes as CISA Issues Warning – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Exploitation attempts targeting a remote code execution flaw in Citrix’s ShareFile product have spiked just as the US Cybersecurity and...
7 Ways to Access Safe Mode in Windows 10 (2023 Update) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jesus Vigo on August 17, 2023, 9:51 AM EDT 7 Ways to Access Safe Mode in Windows 10 (2023 Update) Learn seven...
How to Retrieve and Generate Google 2FA Backup Codes – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Andy Wolber on August 17, 2023, 8:58 AM EDT How to Retrieve and Generate Google 2FA Backup Codes Learn how to retrieve...
WordPress Security Checklist – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Stories of virus and malware infections, data loss, system compromises and unauthorized access dominate headlines, and your WordPress website may be contributing...
Quick Glossary: Cybersecurity Countermeasures – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cybersecurity attacks are inevitable for modern businesses. Therefore, it is vital that businesses deploy countermeasures to mitigate the damage these attacks cause....
What is trap phishing? (2023) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In the complex and vast landscape of cyber security, a subtle danger lurks – trap phishing. As organizations and...
News Alert: Cynomi study shows MSPs offering virtual CISO services to rise fivefold next year – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel, Aug. 17, 2023 — Cynomi, the leading AI-powered virtual Chief Information Security Officer (vCISO) platform vendor for Managed...
LinkedIn under attack, hackers seize accounts – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley Security researchers have identified that a widespread LinkedIn malicious hacking campaign has seen many users locked out of their accounts...
FBI warns cryptocurrency app beta-testers of malware menace – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Are you the kind of person who runs the beta-test versions of mobile apps before they are officially released? If...
Smashing Security podcast #335: AI chat wars, and hacker passwords exposed – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley AI chatbots are under fire in Las Vegas, the secrets of hackers’ passwords are put under the microscope, and Graham...
CISA Launches Joint Initiative to Secure RMM Software – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Cybersecurity and Infrastructure Security Agency (CISA) has unveiled its Remote Monitoring and Management (RMM) Cyber Defense Plan. Created in...
Critical Flaws in PowerShell Gallery Enable Malicious Exploits – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Aqua Nautilus has uncovered critical vulnerabilities persisting within the PowerShell Gallery, resulting in a fertile ground for malicious actors to exploit...
Phishing Spree Targets Zimbra Collaboration Account Holders – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity researchers at ESET have exposed an ongoing mass-spreading phishing campaign that explicitly targets Zimbra Collaboration email server users. The campaign,...
Ransomware Surges With 1500 Confirmed Victims This Year – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 At least 1500 organizations have fallen victim to ransomware attacks globally in the first half of 2023, according to Rapid7’s 2023...
CISA Urges Patching of Actively Exploited Citrix Bug – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Cybersecurity and Infrastructure Security Agency (CISA) has warned that a Citrix flaw patched in June is being actively exploited...
AnonFiles Shuts Down After Massive User Abuse – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A popular anonymous file sharing service used by security researchers and threat actors has decided to close down, citing “extreme volumes”...
Google Fixes 26 Bugs Amid Fake Update Warning – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Google has released the latest version of its Chrome browser, addressing 26 vulnerabilities including eight critical flaws. Chrome 116 covers updates...
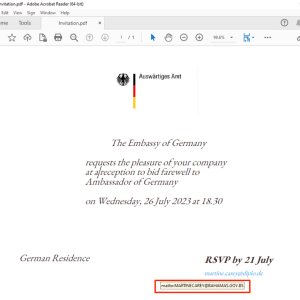
APT29 is targeting Ministries of Foreign Affairs of NATO-aligned countries – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked APT29 used the Zulip Chat App in attacks aimed at ministries of foreign affairs of NATO-aligned countries EclecticIQ researchers...
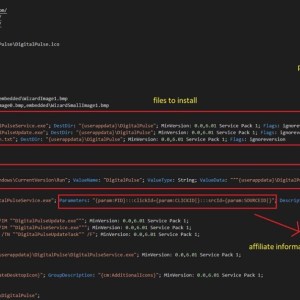
A massive campaign delivered a proxy server application to 400,000 Windows systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers discovered a massive campaign that delivered a proxy server application to at least 400,000 Windows systems. AT&T Alien Labs...
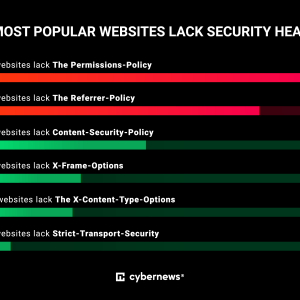
Alarming lack of cybersecurity practices on world’s most popular websites – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The world’s most popular websites lack basic cybersecurity hygiene, an investigation by Cybernews shows. Do you happen to love exploring...
Experts devise an exploit for Apple iOS 16 that relies on fake Airplane Mode – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers detailed a new exploit for Apple iOS 16 that can allow attackers to gain access to a device even...
Cleaning Products manufacturer Clorox Company took some systems offline after a cyberattack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cleaning products manufacturer Clorox Company announced that it has taken some systems offline in response to a cyberattack. The Clorox...
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....