Source: krebsonsecurity.com – Author: BrianKrebs The U.S. government today announced a coordinated crackdown against QakBot, a complex malware family used by multiple cybercrime groups to lay...
Day: August 29, 2023
Data From The Qakbot Malware is Now Searchable in Have I Been Pwned, Courtesy of the FBI – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Today, the US Justice Department announced a multinational operation involving actions in the United States, France, Germany, the Netherlands, and...
Chinese Hacking Group Exploits Barracuda Zero-Day to Target Government, Military, and Telecom – Source:thehackernews.com
Source: thehackernews.com – Author: . A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway (ESG) appliances to breach...
DarkGate Malware Activity Spikes as Developer Rents Out Malware to Affiliates – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 29, 2023The Hacker NewsMalware / Cyber Threat A new malspam campaign has been observed deploying an off-the-shelf malware called DarkGate....
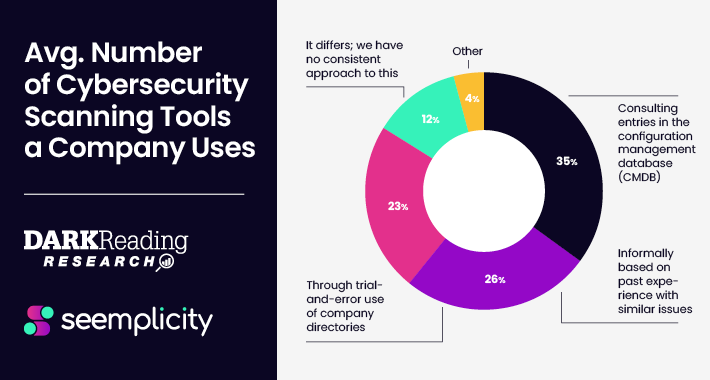
Survey Provides Takeaways for Security Pros to Operationalize their Remediation Life Cycle – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 29, 2023The Hacker NewsRemedial Operations Ask any security professional and they’ll tell you that remediating risks from various siloed security...
Identity Theft from 1965 Uncovered through Face Recognition – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting story: Napoleon Gonzalez, of Etna, assumed the identity of his brother in 1965, a quarter century after his sibling’s...
Ransomware Attack Specialist Tied to Citrix NetScaler Hacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Governance & Risk Management , Patch Management Multiple Highly Automated Campaigns Have Dropped Persistent Web Shells,...
LIVE Webinar | How to Build an Impactful Business Case for a Defensible GRC Program – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Mohit Lal Mug Senior Director, Customer Success, SDG Corp Mohit leads the pre-sales & customer success functions for TruOps and works...
Ransomware Attack Cleanup Costs: $11M So Far for Rackspace – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Incident & Breach Response , Ransomware Fallout From Crypto-Locking Malware Attacks and Data Exfiltration Remains Costly...
Operation ‘Duck Hunt’ Dismantles Qakbot – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Ransomware 52 Servers, Nearly $9 Million Worth of Cryptocurrency Seized Michael Novinson (MichaelNovinson) ,...
LIVE Webinar | How to Build an Impactful Business Case for a Defensible GRC Program – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Mohit Lal Mug Senior Director, Customer Success, SDG Corp Mohit leads the pre-sales & customer success functions for TruOps and works...
The Reality of Cyberinsurance in 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The cyberinsurance industry is maturing. In its early days, it simply accepted cyber risk with few questions asked. It lost...
Did Microsoft Just Upend the Enterprise Browser Market? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine NEWS ANALYSIS: Redmond plants its feet firmly in the enterprise browser space, sending major ripples through Silicon Valley’s bustling venture-backed...
UN Warns Hundreds of Thousands in Southeast Asia Roped Into Online Scams – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press The U.N. human rights office says criminal gangs have forced hundreds of thousands of people in Southeast Asia into participating...
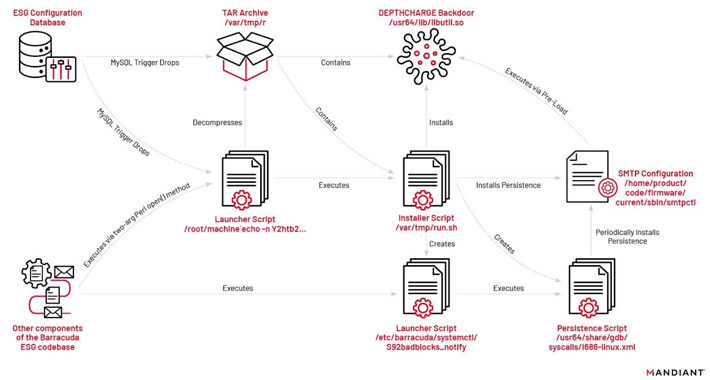
Chinese APT Was Prepared for Remediation Efforts in Barracuda ESG Zero-Day Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Chinese cyberespionage group exploiting Barracuda Email Security Gateway (ESG) appliances was preparing for remediation efforts, deploying persistent backdoors on...
Meta Fights Sprawling Chinese ‘Spamouflage’ Operation – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Meta on Tuesday said it purged thousands of Facebook accounts that were part of a widespread online Chinese spam operation trying...
Personal, Health Information of 1.2 Million Stolen in PurFoods Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Meal delivery service PurFoods says the personal and protected health information of more than 1.2 million individuals was stolen in...
LockBit 3.0 Ransomware Variants Surge Post Builder Leak – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The leak of the LockBit 3.0 ransomware builder has triggered a surge in personalized variants, impacting various organizations. Writing in an...
New Ransomware Campaign Targets Citrix NetScaler Flaw – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts at Sophos X-Ops have uncovered a wave of attacks targeting unpatched Citrix NetScaler systems exposed to the internet. Describing...
Mom’s Meals Warns of Major Data Breach Affecting Over 1.2 Million Individuals – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Mom’s Meals, a medical meal delivery service operated by PurFoods in the U.S., has alerted its users about a significant...
How to Manage XDR Alerts with Heimdal – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Adelina Deaconu Heimdal XDR offers you full visibility into network traffic, user behavior, and endpoint activity. It makes investigating threats much easier,...
Nordic Users Targeted by National Danish Police Phishing Attack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Vladimir Unterfingher A new type of cyber-attack is currently spreading like wildfire in the Nordics, targeting email addresses indiscriminate of user profiles...
How to Implement an XDR Software? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Traditional security solutions are no longer enough to protect your business from sophisticated attacks. As a cybersecurity professional, you have...
Eggs-cellent email: How cooking with eggs showcases the promise & peril of email security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Jeremy Fuchs is the Content Marketing Specialist for Harmony Email & Collaboration. Previously, he worked at Avanan, which was acquired by...
10 SASE benefits that you should be aware of – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The Secure Access Service Edge (SASE) framework emerged in 2019, as industry analysts observed new use cases and buying...
GUEST ESSAY: Where we stand on mitigating software risks associated with fly-by-wire jetliners – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Vance Hilderman The threat of bad actors hacking into airplane systems mid-flight has become a major concern for airlines and...
Report Reveals Growing Disparity in Cyber Insurance Landscape – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Delinea’s 2023 State of Cyber Insurance Report has revealed a growing disconnect between carriers and enterprises seeking robust coverage. Insights from...
Microsoft Warns of Adversary-in-the-Middle Uptick on Phishing Platforms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Written by Microsoft has observed a proliferation of adversary-in-the-middle (AiTM) techniques deployed through phishing-as-a-service (PhaaS) platforms, the company explained in a...
Four in Five Cyber-Attacks Powered by Just Three Malware Loaders – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity provider ReliaQuest observed that cyber-criminals used seven different malware loaders to deploy their intrusion campaigns in the first half of...
FIN8-linked actor targets Citrix NetScaler systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini FIN8-linked actor targets Citrix NetScaler systems A financially motivated actor linked to the FIN8 group exploits the CVE-2023-3519 RCE in...