Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Day: August 19, 2023
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
In Other News: US Hacking China, Unfixed PowerShell Gallery Flaws, Free Train Tickets – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
Jenkins Patches High-Severity Vulnerabilities in Multiple Plugins – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Open source software development automation server Jenkins this week announced patches for high- and medium-severity vulnerabilities impacting multiple plugins. The...
Stealthy ‘LabRat’ Campaign Abuses TryCloudflare to Hide Infrastructure – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A newly discovered financially motivated operation is relying on signature-based tools and stealthy cross-platform malware to remain undetected, and abuses...
Companies Respond to ‘Downfall’ Intel CPU Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Several major companies have published security advisories in response to the recently disclosed Intel CPU vulnerability named Downfall. Discovered by...
Israel, US to Invest $4 Million in Critical Infrastructure Security Projects – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Government agencies in Israel and the US have announced plans to invest $3.85 million in projects meant to improve the...
Federally Insured Credit Unions Required to Report Cyber Incidents Within 3 Days – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The National Credit Union Administration (NCUA) is updating cyberattack reporting rules, requiring all federally insured credit unions to report incidents...
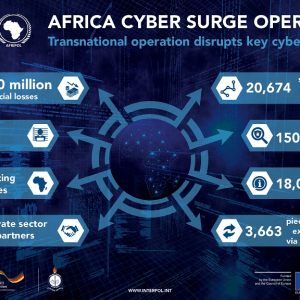
Africa Cyber Surge II: $40 million, 20,000 networks & 25 countries – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The Africa Cyber Surge II operation has led to the take-down of rogue networks that were responsible for financial...
A third of companies hit with ransomware didn’t have to pay…Here’s how they did it – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Pete Nicoletti, Check Point Field CISO, Americas One in ten victims of ransomware pay ransoms of over $1 million. With...
QR Code Campaign Targets Major Energy Firm – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A significant phishing campaign employing QR codes has recently come to light, with a major US-based energy company as one of...
Cybersecurity Study Reveals Web App Vulnerability Crisis – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A recent cybersecurity study has brought to light a concerning vulnerability crisis affecting web applications. CyCognito’s semi-annual State of External Exposure...
Interpol-Led Africa Cyber Surge II Nets 14 Cybercrime Suspects – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A collaborative effort led by Interpol, known as Africa Cyber Surge II, has yielded significant results in combating cybercrime across the...
UK’s AI Safety Summit Scheduled For Early November – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s much-anticipated summit on AI safety will reportedly be held in November, with cybersecurity experts welcoming the government’s focus on...
Chinese Hackers Use DLL Hijacking to Target Asian Gamblers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have spotted a new Chinese espionage campaign targeting Asian gambling companies, which they suspect is the work of the...
Proxyjacking and Cryptomining Campaign Targets GitLab – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have discovered a new financially motivated cyber-threat campaign designed to make money from cryptomining and proxyjacking while staying hidden...
WinRAR flaw enables remote code execution of arbitrary code – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A flaw impacting the file archiver utility for Windows WinRAR can allow the execution of commands on a computer by...
#OpFukushima: Anonymous group protests against the plan to dump Fukushima RADIOACTIVE wastewater into Pacific – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini #OpFukushima: The famous collective Anonymous has launched cyberattacks against Japan nuclear websites over Fukushima water plan. The hacker collective Anonymous...
Massive phishing campaign targets users of the Zimbra Collaboration email server – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A massive social engineering campaign is targeting users of the Zimbra Collaboration email server to steal their login credentials. ESET...
Africa Cyber Surge II law enforcement operation has led to the arrest of 14 suspects – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini An international law enforcement operation across 25 African countries has led to the arrest of 14 cybercriminals. A coordinated law...
Bronze Starlight targets the Southeast Asian gambling sector – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of an ongoing campaign attributed to China-linked Bronze Starlight that is targeting the Southeast Asian gambling sector. SentinelOne...
The Week in Ransomware – August 18th 2023 – LockBit on Thin Ice – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams While there was quite a bit of ransomware news this week, the highlighted story was the release of Jon DiMaggio’s...
WinRAR flaw lets hackers run programs when you open RAR archives – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A high-severity vulnerability has been fixed in WinRAR, the popular file archiver utility for Windows used by millions, that can...
Hotmail email delivery fails after Microsoft misconfigures DNS – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Hotmail users worldwide have problems sending emails, with messages flagged as spam or not delivered after Microsoft misconfigured the domain’s...
Interpol arrests 14 suspected cybercriminals for stealing $40 million – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An international law enforcement operation led by Interpol has led to the arrest of 14 suspected cybercriminals in an operation...
ExpressVPN Review (2023): Features, Pricing and Alternatives – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke This is a comprehensive ExpressVPN Review, covering features, pricing, and more. Use this guide to find out if it is...