Source: www.cybertalk.org – Author: slandau Keely Wilkins is an Evangelist with the Office of the CTO as well as a Pre-Sales Security Engineer at Check Point....
Day: August 15, 2023
GUEST ESSAY: A call to decentralize social identities — to curtail social media privacy abuses – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Chris Were Social media giants have long held too much power over our digital identities. Related: Google, Facebook promote third-party...
Ivanti Avalanche impacted by critical pre-auth stack buffer overflows – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Two stack-based buffer overflows collectively tracked as CVE-2023-32560 impact Ivanti Avalanche, an enterprise mobility management (EMM) solution designed to manage,...
LinkedIn accounts hacked in widespread hijacking campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas LinkedIn is being targeted in a wave of account hacks resulting in many accounts being locked out for security reasons...
Almost 2,000 Citrix NetScaler servers backdoored in hacking campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu A threat actor has compromised close to 2,000 thousand Citrix NetScaler servers in a massive campaign exploiting the critical-severity remote...
Raccoon Stealer malware returns with new stealthier version – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney The developers of Raccoon Stealer information-stealing malware have ended their 6-month hiatus from hacker forums to promote a...
New CVE-2023-3519 scanner detects hacked Citrix ADC, Gateway devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Mandiant has released a scanner to check if a Citrix NetScaler Application Delivery Controller (ADC) or NetScaler Gateway Appliance was...
Back to school security against ransomware attacks on K-12 and colleges – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software A ransomware attack on an educational institution causes more than just class disruption. It can result in lost...
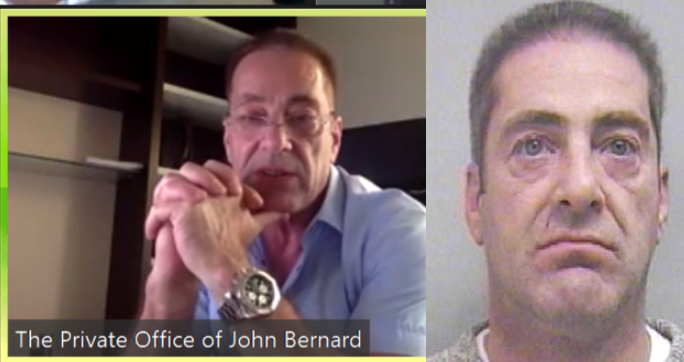
Diligere, Equity-Invest Are New Firms of U.K. Con Man – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs John Clifton Davies, a convicted fraudster estimated to have bilked dozens of technology startups out of more than $30 million through...
Discord.io Halts All Operations After Massive Data Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Discord.io has shut down operations after suffering a major data breach exposing the personal details of its 760,000 members. A statement...
Global IoT Trust Survey Reveals Security Concerns – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new study by IT security solutions provider Utimaco has revealed the prevailing lack of trust in Internet of Things (IoT)...
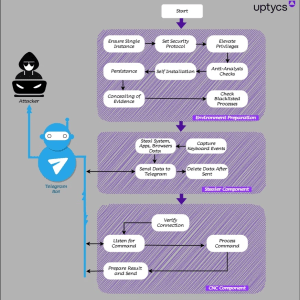
New QwixxRAT Trojan Spreads Through Messaging Apps – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new cybersecurity threat known as QwixxRAT, a Remote Access Trojan (RAT), was discovered by the Uptycs Threat Research team in...
UK Police Data Breach Exposes Victim Information – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Norfolk and Suffolk police in the UK have confirmed the accidental exposure of personal data belonging to more than 1000...
AI a Top Risk and the Preferred Solution to Financial Crime – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Generative AI tools are the most effective way to tackle financial crime, but also a number one threat, according to a...
PSNI: Leaked Data Will be Used to Target Police Officers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Sensitive details of 10,000 Northern Ireland police officers and staff are in the hands of paramilitary groups, the Police Service of...
Over 100,000 Users of Hacking Forums Infected With Malware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have discovered over 140,000 breached passwords associated with accounts on hacking forums after their owners were infected with info-stealing...
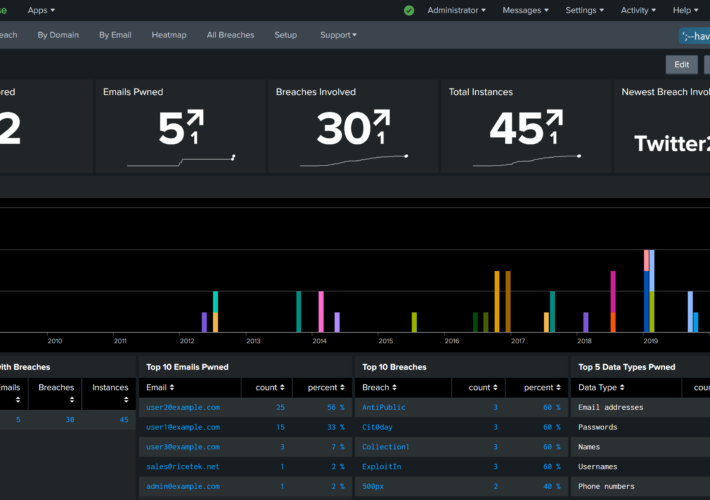
All New Have I Been Pwned Domain Search APIs and Splunk Integration – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I’ve been teaching my 13-year old son Ari how to code since I first got him started on Scratch many...
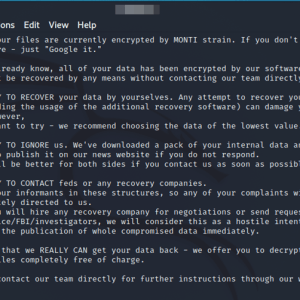
Monti Ransomware gang launched a new Linux encryptor – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Monti Ransomware operators returned, after a two-month pause, with a new Linux variant of their encryptor. The Monti ransomware operators...
Hacking ATMs by exploiting flaws in ScrutisWeb ATM fleet software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers found several flaws in the ScrutisWeb ATM fleet monitoring software that can expose ATMs to hack. Researchers from the...
QwixxRAT, a new Windows RAT appears in the threat landscape – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini QwixxRAT is a new Windows remote access trojan (RAT) that is offered for sale through Telegram and Discord platforms. The...
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...