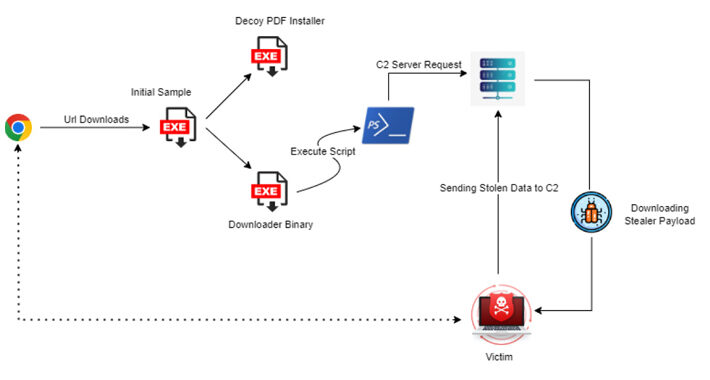
Source: thehackernews.com – Author: . Aug 10, 2023THNMalware / Cyber Threat Malicious actors are using a legitimate Rust-based injector called Freeze[.]rs to deploy a commodity malware...
Day: August 10, 2023
New Statc Stealer Malware Emerges: Your Sensitive Data at Risk – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 10, 2023THNMalware / Cyber Threat A new information malware strain called Statc Stealer has been found infecting devices running Microsoft...
Encryption Flaws in Popular Chinese Language App Put Users’ Typed Data at Risk – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 10, 2023THNPrivacy / Encryption A widely used Chinese language input app for Windows and Android has been found vulnerable to...
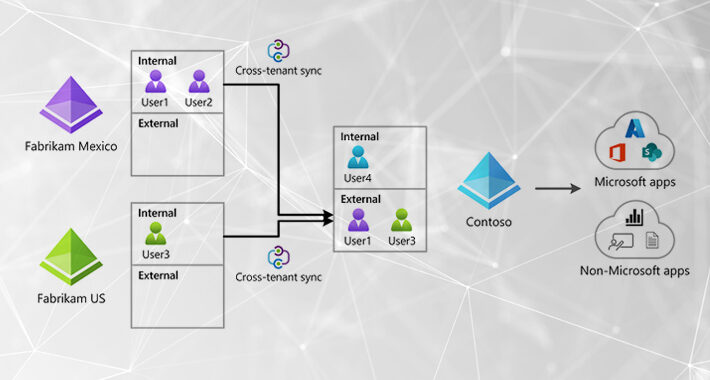
Emerging Attacker Exploit: Microsoft Cross-Tenant Synchronization – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 10, 2023The Hacker NewsThreat Detection / Attack Signal Attackers continue to target Microsoft identities to gain access to connected Microsoft...
Quick Glossary: Cybersecurity Attack Response and Mitigation – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Your computer network is under constant attack. The hard reality is that one of those cyberattacks will succeed, and you had better...
Cryptographic Flaw in Libbitcoin Explorer Cryptocurrency Wallet – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • August 10, 2023 10:43 AM @ Bruce, If I remember rightly it was 94 or...
Highly targeted phishing lures, masqueraded as legitimate Teams chats – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: More than 270 million people use Microsoft Teams every month, and this isn’t the first time that hackers have...
New York Introduces First-Ever Statewide Cybersecurity Strategy – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Governor Kathy Hochul has introduced New York’s first-ever statewide cybersecurity strategy, reinforced by a $600m commitment. The strategy emerges as a...
APT31 Linked to Recent Industrial Attacks in Eastern Europe – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The threat actor APT31 (AKA Judgment Panda and Zirconium) has been linked to recent industrial attacks in eastern Europe, according to...
#BHUSA: Only 22% of Firms Have Mature Threat Intelligence Programs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Only 22% of organizations have achieved a fully matured threat intelligence program, revealed a new report by cybersecurity solutions provider OPSWAT....
Potent Trojans Targeting MacOS Users – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Threat actors are becoming more efficient at targeting Mac users through MacOS tailored malware, according to Bitdefender’s macOS Threat Landscape Report....
#BHUSA: DARPA Challenges AI Pros to Safeguard US Infrastructure – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 “I’m going to do something I’ve never done before.” Those were Jeff Moss’s words during his August 9 opening speech of...
CISA adds actively exploited flaw in .NET, Visual Studio to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added zero-day vulnerability CVE-2023-38180 affecting .NET and Visual Studio to its Known Exploited Vulnerabilities catalog. US Cybersecurity and...
US Govt launches Artificial Intelligence Cyber Challenge – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The US Government House this week launched an Artificial Intelligence Cyber Challenge competition for creating a new generation of AI...
Data of all serving police officers Police Service of Northern Ireland (PSNI) mistakenly published online – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Police Service of Northern Ireland (PSNI) mistakenly shared sensitive data of all 10,000 serving police officers in response to a...
Balada Injector still at large – new domains discovered – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Balada Injector is still at large and still evading security software by utilizing new domain names and using new...
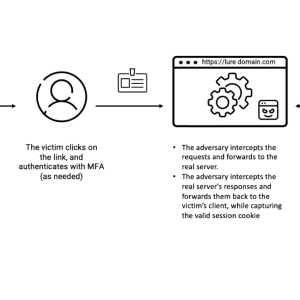
EvilProxy used in massive cloud account takeover scheme – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cloud account takeover scheme utilizing EvilProxy hit over 100 top-level executives of global organizations EvilProxy was observed sending 120,000 phishing...
Law Enforcement Takes Down Phishing-as-a-Service Site – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime as-a-service , Fraud Management & Cybercrime Authorities in Multiple Countries Arrest Operators of 16shop Mihir Bagwe (MihirBagwe) • August 9,...
US Restricts Investment in Chinese AI, Other Technologies – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Executive Order Targets Dual-Use AI, Semiconductors and Quantum IT David...
Live Webinar | SaaS: The Gaping Hole in Your Disaster Recovery Plan – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Live Webinar | Beyond Zero Trust: Incorporating SASE for Secure Remote Access – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Marcus Ward GM & Product Director, Datto Networking Marcus Ward is the GM and Product Director for Datto Networking and brings...
Lawsuits Mounting Against Florida Hospital in Wake of Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Governance & Risk Management , Healthcare So Far, 3 Proposed Class Actions Allege Negligence in Case Affecting 1.3M...
Ukraine Fends Off Sandworm Battlefield Espionage Ploy – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Endpoint Security , Fraud Management & Cybercrime Russian Military Hackers Planned Mobile Device Malware Campaign Mihir...
European Startup Pistachio Raises €3.25 Million for Cybersecurity Training Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Norway-based startup Pistachio on Thursday announced raising €3.25 million (roughly $3.5 million) for its AI-driven cybersecurity training platform. The Pistachio...
CISA Warns Organizations of Exploited Vulnerability Affecting .NET, Visual Studio – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The US Cybersecurity and Infrastructure Security Agency (CISA) has added a zero-day flaw affecting Microsoft’s .NET and Visual Studio products...
White House Offers Prize Money for Hacker-Thwarting AI – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP The White House on Wednesday launched a competition offering millions of dollars in prize money for creating new artificial intelligence systems...
Western Digital, Synology NAS Vulnerabilities Exposed Millions of Users’ Files – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Critical vulnerabilities discovered by IoT and industrial cybersecurity firm Claroty in Western Digital (WD) and Synology network-attached storage (NAS) products...
#BHUSA: ESET Unmasks Cyber-Espionage Group Targeting Embassies in Belarus – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 In a revelation made during Black Hat USA, cybersecurity provider ESET unveiled the discovery of a novel threat actor engaged in...
Fresh Blow to PSNI Security as Second Data Breach Disclosed – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A further breach of personal data of serving officers from the Police Service of Northern Ireland (PSNI) was confirmed on August...
Regulator: “Harmful” Web Design Could Break Data Protection Laws – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Information Commissioner’s Office (ICO) has warned UK companies that it will take enforcement action against those that use website design...

![new-attack-alert:-freeze[]rs-injector-weaponized-for-xworm-malware-attacks-–-source:thehackernews.com](https://ciso2ciso.com/wp-content/uploads/2023/08/73456/new-attack-alert-freezers-injector-weaponized-for-xworm-malware-attacks-sourcethehackernews-com-710x380.jpg)