Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Day: August 3, 2023
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: –
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: –
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
ESET Threat Report H1 2023 – Source:
Source: – Author: 1 A view of the H1 2023 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and...
Emotet: sold or on vacation? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Originally a banking trojan, Emotet later evolved into a full-blown botnet and went on to become one of the most dangerous cyberthreats...
What’s up with Emotet? – Source:
Source: – Author: 1 A brief summary of what happened with Emotet since its comeback in November 2021 Original Post URL: Category & Tags: –
Malicious Apps Use Sneaky Versioning Technique to Bypass Google Play Store Scanners – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 03, 2023THNMobile Security / Malware Threat actors are leveraging a technique called versioning to evade Google Play Store’s malware detections...
New Version of Rilide Data Theft Malware Adapts to Chrome Extension Manifest V3 – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 03, 2023THNBrowser Security / Malware Cybersecurity researchers have discovered a new version of malware called Rilide that targets Chromium-based web...
Hundreds of Citrix NetScaler ADC and Gateway Servers Hacked in Major Cyber Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 03, 2023THNVulnerability / Cyber Threat Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by malicious actors to...
A Penetration Testing Buyer’s Guide for IT Security Teams – Source:thehackernews.com
Source: thehackernews.com – Author: . The frequency and complexity of cyber threats are constantly evolving. At the same time, organizations are now collecting sensitive data that,...
Microsoft Flags Growing Cybersecurity Concerns for Major Sporting Events – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 03, 2023THNCyber Threat / Network Security Microsoft is warning of the threat malicious cyber actors pose to stadium operations, warning...
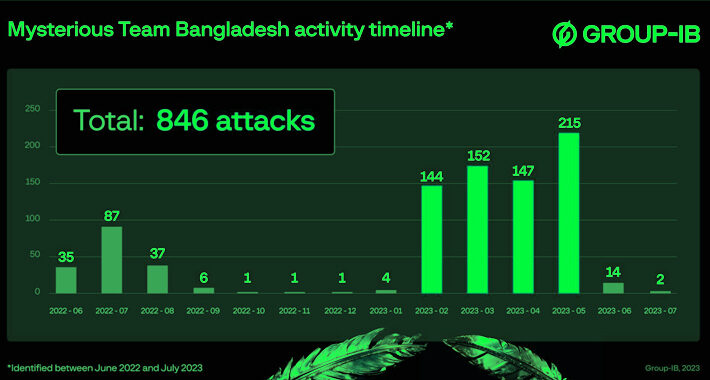
“Mysterious Team Bangladesh” Targeting India with DDoS Attacks and Data Breaches – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 03, 2023THNCyber Attack / Data Safety A hacktivist group known as Mysterious Team Bangladesh has been linked to over 750...
Irish DPC Will Conclude TikTok Privacy Probe Within Weeks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance European Data Protection Board Gives the Commission 1 Month Akshaya...
Modern-Day Hacktivist Chaos: Who’s Really Behind the Mask? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Russia Likely Continues to Run Fake Groups, Although Regional Players Also at...
ChatGPT and Generative AI: Balancing Risks and Rewards – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Rodman Ramezanian, global threat lead, Skyhigh Security Generative AI offers productivity gains, but if deployed without due security precautions, it can...
Cryptohack Roundup: WorldCoin Probes, Curve Finance Theft – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: LeetSwap Hack, Digital Assets Regulatory Proposal in NDAA Rashmi...
Ivanti Norway Hacks Began in April, Says US CISA – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Enterprise Mobility Management / BYOD Mobile Device Management Are ‘Attractive Targets,’ Warns Joint Advisory With Norway Mihir Bagwe...
Endor Labs Raises $70M to Push From Code to Pipeline Defense – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 DevSecOps , Events , Finance & Banking A 2023 RSA Innovation Sandbox Contest Finalist Has Its First Major Funding Round Michael...
Jericho Security Raises $3 Million for Awareness Training Powered by Generative AI – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Jericho Security today announced that it has raised $3 million in a pre-seed funding round led by global investment firm...
670 ICS Vulnerabilities Disclosed by CISA in First Half of 2023: Analysis – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The US Cybersecurity and Infrastructure Security Agency (CISA) disclosed 670 vulnerabilities affecting industrial control systems (ICS) and other operational technology...
Dozens of RCE Vulnerabilities Impact Milesight Industrial Router – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Dozens of vulnerabilities impacting the Milesight UR32L industrial router could be exploited to execute arbitrary code or commands, Cisco’s Talos...