Source: www.techrepublic.com – Author: TechRepublic Academy on August 31, 2023, 5:00 AM EDT Protect Your Email With This Top-Rated Tool — Just $40 for Labor Day...
Month: August 2023
RFP Templates and Guidebook – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: A request for proposal is a common method for soliciting vendor quotes and answers about potential product or service offerings. They specifically...
SapphireStealer Malware: A Gateway to Espionage and Ransomware Operations – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 31, 2023THNMalware / Cyber Threat An open-source .NET-based information stealer malware dubbed SapphireStealer is being used by multiple entities to...
North Korean Hackers Deploy New Malicious Python Packages in PyPI Repository – Source:thehackernews.com
Source: thehackernews.com – Author: . Three additional rogue Python packages have been discovered in the Package Index (PyPI) repository as part of an ongoing malicious software...
North Korean hackers behind malicious VMConnect PyPI campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas North Korean state-sponsored hackers are behind the VMConnect campaign that uploaded to the PyPI (Python Package Index) repository malicious packages,...
LogicMonitor customers hacked in reported ransomware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Network monitoring company LogicMonitor confirmed today that certain customers of its SaaS platform have fallen victim to cyberattacks linked to...
Free Key Group ransomware decryptor helps victims recover data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Researchers took advantage of a weakness in the encryption scheme of Key Group ransomware and developed a decryption tool that...
GRU hackers attack Ukrainian military with new Android malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney Hackers working for the Main Directorate of the General Staff of the Armed Forces of the Russian Federation,...
Classiscam fraud-as-a-service expands, now targets banks and 251 brands – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney The “Classiscam” scam-as-a-service operation has broadened its reach worldwide, targeting many more brands, countries, and industries, causing more...
Forever 21 Breach Notification Leaves Unanswered Questions – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Security Operations 539,207 Employees Warned This Week About 8-Week Breach Discovered in March Mathew J. Schwartz (euroinfosec) •...
What’s Behind Disturbing Breach Trends in Healthcare? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 While the volume of major health data breaches reported to regulators is declining, a disturbing trend is developing that reflects the...
Five Eyes Fingers Moscow in Ukrainian Android Hacking – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Endpoint Security , Fraud Management & Cybercrime Western Intelligence Alliance Publishes Details of ‘Infamous Chisel’ Campaign...
CrowdStrike CEO: Point Product Vendors Are Being Left Behind – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Detection & Response (EDR) , Endpoint Protection Platforms (EPP) , Endpoint Security George Kurtz Says Clients Spot ‘Point Products Masquerading...
Cryptohack Roundup: Cypher Comp Plan – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: A WinRAR Exploit, Balancer Exploits and the DEA Scammed...
Japan’s cyber security agency suffers email breach – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Japan’s National Center of Incident Readiness and Strategy for Cybersecurity (NISC) has experienced a breach. Sensitive network data may...
Black Hat Fireside Chat: How ‘enterprise browsers’ serve as a checkpoint to stop ChatGPT leakage – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido For a couple of decades now, the web browser has endured in workplace settings as the primary...
BYOD Security Gap: Survey Finds 49% of European Firms Unprotected – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A recent survey conducted by Jamf, a provider of enterprise-level management and security solutions for Apple ecosystems, has revealed that 49%...
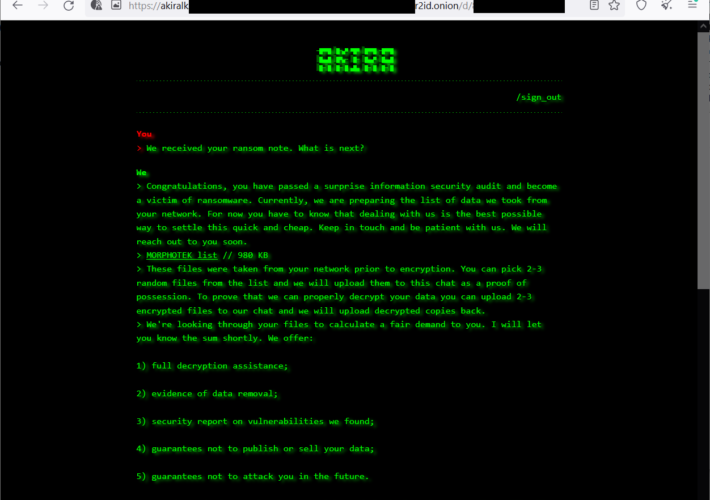
Akira Ransomware gang targets Cisco ASA without Multi-Factor Authentication – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Akira Ransomware gang targets Cisco ASA without Multi-Factor Authentication Experts warn of ongoing credential stuffing and brute-force attacks targeting Cisco...
Paramount Global disclosed a data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Paramount Global disclosed a data breach Multinational mass media conglomerate Paramount Global suffered a data breach after an unauthorized party...
National Safety Council data leak: Credentials of NASA, Tesla, DoJ, Verizon, and 2K others leaked by workplace safety organization – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini National Safety Council data leak: Credentials of NASA, Tesla, DoJ, Verizon, and 2K others leaked by workplace safety organization The...
Abusing Windows Container Isolation Framework to avoid detection by security products – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Abusing Windows Container Isolation Framework to avoid detection by security products Researchers demonstrated how attackers can abuse the Windows Container...
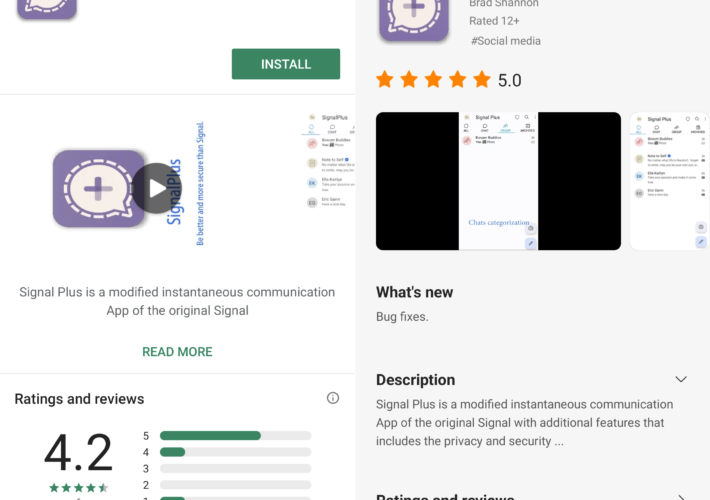
Chinese GREF APT distributes spyware via trojanized Signal and Telegram apps on Google Play and Samsung Galaxy stores – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Chinese GREF APT distributes spyware via trojanized Signal and Telegram apps on Google Play and Samsung Galaxy stores China-linked APT...
Threat actors started exploiting Juniper flaws shortly after PoC release – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors started exploiting Juniper flaws shortly after PoC release Threat actors started using the exploit chain in attacks on...
Energy Department Offering $9M in Cybersecurity Competition for Small Electric Utilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The US Department of Energy on Wednesday announced a competition that can help smaller electric utilities obtain funding and technical...
Vulnerability in WordPress Migration Plugin Exposes Websites to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A vulnerability in several extensions for the All-in-One WP Migration plugin potentially exposes WordPress websites to attacks leading to sensitive...
Apple Preparing iPhone 14 Pro Phones for 2024 Security Research Device Program – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Apple on Wednesday announced that it is now accepting applications for the 2024 iPhone Security Research Device Program (SRDP). Intended...
Five Eyes Report: New Russian Malware Targeting Ukrainian Military Android Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Five Eyes agencies have issued a joint report on the malware used recently by Russian state-sponsored hackers to target Android...
Splunk Patches High-Severity Flaws in Enterprise, IT Service Intelligence – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Splunk on Wednesday announced patches for multiple high-severity vulnerabilities in Splunk Enterprise and IT Service Intelligence, including flaws in third-party...
Lawsuit Accuses University of Minnesota of Not Doing Enough to Prevent Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A lawsuit filed on behalf of a former student and former employee at the University of Minnesota accuses the university...
500k Impacted by Data Breach at Fashion Retailer Forever 21 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Fashion retailer Forever 21 has started informing more than 500,000 individuals that their personal information was compromised in a data...