Source: securityaffairs.com – Author: Pierluigi Paganini A researcher recently discovered that a Bangladesh government website leaks the personal data of citizens. The researcher Viktor Markopoulos discovered...
Month: July 2023
A man has been charged with a cyber attack on the Discovery Bay water treatment facility – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A man from Tracy, California, has been charged with a computer attack on the Discovery Bay water treatment facility. Rambler...
Progress warns customers of a new critical flaw in MOVEit Transfer software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Progress released security patches for a new critical SQL injection vulnerability affecting its MOVEit Transfer software. Progress is informing customers...
CISA and FBI warn of Truebot infecting US and Canada based organizations – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA and the FBI warned today of a new Truebot variant employed in attacks against organizations in the United States and...
Vishing Goes High-Tech: New ‘Letscall’ Malware Employs Voice Traffic Routing – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 07, 2023Swati KhandelwalMobile Security / Malware Researchers have issued a warning about an emerging and advanced form of voice phishing...
Another Critical Unauthenticated SQLi Flaw Discovered in MOVEit Transfer Software – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 07, 2023Swati KhandelwalVulnerability / Cyber Threat Progress Software has announced the discovery and patching of a critical SQL injection vulnerability...
Mastodon Social Network Patches Critical Flaws Allowing Server Takeover – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 07, 2023Swati KhandelwalVulnerability / Social Media Mastodon, a popular decentralized social network, has released a security update to fix critical...
After Zero-Day Attacks, MOVEit Turns to Security Service Packs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Faced with a barrage of ransomware attacks hitting zero-days in its MOVEit product line, Progress Software late Thursday announced plans...
In Other News: Healthcare Product Flaws, Free Email Security Testing, New Attack Techniques – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
Former Contractor Employee Charged for Hacking California Water Treatment Facility – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A 53-year-old man from Tracy, California, has been charged for allegedly hacking into the systems of a water treatment facility...
Iranian Cyberspies Target US-Based Think Tank With New macOS Malware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire In a recent attack against a US-based think tank, Iranian cyberespionage group Charming Kitten was observed porting a PowerShell backdoor...
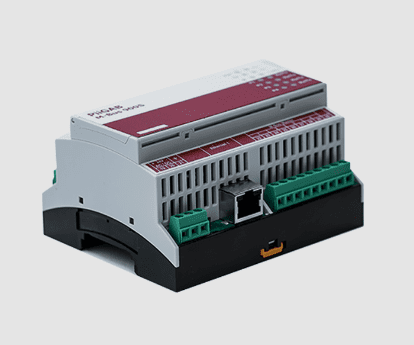
Vulnerabilities in PiiGAB Product Could Expose Industrial Organizations to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Potentially serious vulnerabilities discovered by researchers in a PiiGAB product could expose industrial organizations to remote hacker attacks. PiiGAB is...
OWASP SwSec 5D Tool Provides SDLC Maturity Ratings, Aids Software Supply Chain – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Open Source Foundation for Application Security (OWASP) announced a five-dimensional secure software development maturity reference framework (SwSec 5D) in...
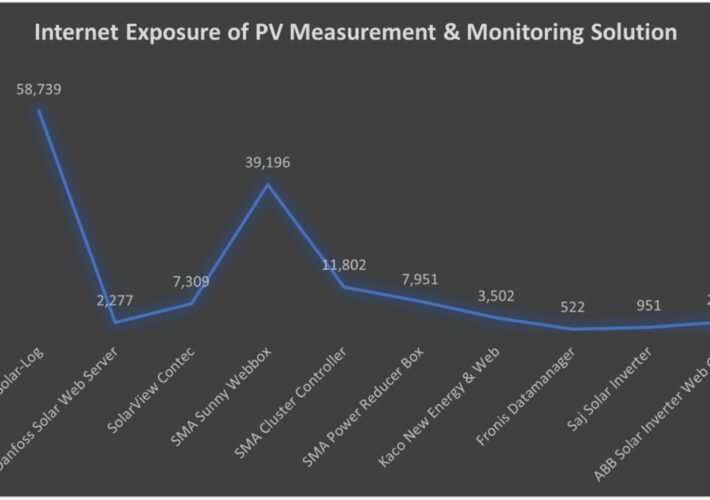
Security Firm Finds Over 130k Internet-Exposed Photovoltaic Diagnostics Systems – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire More than 130,000 photovoltaic monitoring and diagnostic solutions are accessible from the public internet, which could make them susceptible to...
Two Apps Hosted on Google Play Caught Sending User Data to Chinese Servers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Two file management applications hosted on Google Play, with more than 1.5 million combined downloads, were caught sending user data...
CISA warns govt agencies to patch actively exploited Android driver – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA ordered federal agencies today to patch a high-severity Arm Mali GPU kernel driver privilege escalation flaw added to its list of...
Critical TootRoot bug lets attackers hijack Mastodon servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Mastodon, the free and open-source decentralized social networking platform, has patched four vulnerabilities, one of them critical that allows hackers...
Barracuda working on fix for ongoing Email Gateway login issues – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Bing Image Creator Email and network security firm Barracuda is working to fix an ongoing issue that triggers invalid...
The Need for Risk-Based Vulnerability Management to Combat Threats – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 Cyber attacks are increasing as the number of vulnerabilities found in software has increased by over 50% in the...
MOVEit Transfer customers warned to patch new critical flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas MOVEit Transfer, the software at the center of the recent massive spree of Clop ransomware breaches, has received an update...
Friday Squid Blogging: Giant Squid Nebula – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Pretty: A mysterious squid-like cosmic cloud, this nebula is very faint, but also very large in planet Earth’s sky. In...
The AI Dividend – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The AI Dividend For four decades, Alaskans have opened their mailboxes to find checks waiting for them, their cut of...
StackRot: A New Linux Kernel Flaw Allows Privilege Escalation – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu A new vulnerability has been found by security researchers. Dubbed StackRot, the Linux Kernel flaw is impacting versions 6.1 through...
Malicious Insider Explained: The Call is Coming from Inside the House – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Alina Georgiana Petcu For the most part, today’s modern workplace has grown accustomed to cyberattacks directed by third parties that are external...
Top Data Breaches in 2023: Alarming Incidents Impacting Companies – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian The year 2023 has witnessed a surge in data breaches and cyberattacks, posing significant challenges for organizations striving to safeguard...
CISA, FBI: A New Version of the Truebot Malware Is Actively Used in Attacks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu A new warning was issued by CISA and the FBI! Organizations across the United States and Canada have been targeted...
Top Suspect in 2015 Ashley Madison Hack Committed Suicide in 2014 – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs When the marital infidelity website AshleyMadison.com learned in July 2015 that hackers were threatening to publish data stolen from 37 million...
Owning cyber resilience — whose job is it anyway? – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The frequency and severity of cyber disruptions highlight the need for robust cyber resilience planning. Recent statistics reveal some...
Do you know why people are really afraid of AI? Answers here. – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau In this forward-looking, tell-all interview, Mazhar Hamayun, a Check Point Regional Architect, provides insight into the profound concerns surrounding the rapid...
The best ways to balance risks and benefits of artificial intelligence – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Artificial intelligence, once on the periphery of technological advancements, has become firmly established as an indispensable tool across organizations....