Source: securityaffairs.com – Author: Pierluigi Paganini The French government is going to grant law enforcement the power to spy on suspects through smartphones and other devices....
Month: July 2023
6 Best VPNs for iPhone in 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke on July 10, 2023, 1:51 PM EDT 6 Best VPNs for iPhone in 2023 Which VPN works best on iPhones?...
How to Use an SSH Config File on macOS for Easier Connections to Your Data Center Servers – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen on July 10, 2023, 5:30 AM EDT How to Use an SSH Config File on macOS for Easier Connections to...
What Are Mobile VPN Apps and Why You Should Be Using Them – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: When you think of VPNs, chances are pretty good your thoughts go to the tried and true virtual private networks of old,...
Microsoft finally fixes broken Surface Pro X laptop cameras – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is finally rolling out a driver update to address a known issue causing built-in cameras on ARM-based Windows devices...
RomCom hackers target NATO Summit attendees in phishing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A threat actor referred to as ‘RomCom’ has been targeting organizations supporting Ukraine and guests of the upcoming NATO Summit...
VMware warns of exploit available for critical vRealize RCE bug – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan VMware warned customers today that exploit code is now available for a critical vulnerability in the VMware Aria Operations for...
Amazon’s AppStore is getting more apps and games on Windows 11 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar In collaboration with Microsoft, Amazon has announced the general availability of its AppStore on Windows 11 for all developers. This...
Microsoft: Windows 11 21H2 reaching end of service in October – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft warned customers today that multiple editions of Windows 11, version 21H2, will reach the end-of-service (EOS) in three months,...
Apple releases emergency update to fix zero-day exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Apple has issued a new round of Rapid Security Response (RSR) updates to address a new zero-day bug exploited in...
Former employee charged for attacking water treatment plant – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A former employee of Discovery Bay Water Treatment Facility in California was indicted by a federal grand jury for intentionally...
Hands on with Windows Copilot – A Bing.com web wrapper – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar In its quest to create “Windows Assistant for PCs”, Microsoft introduced Windows Copilot, a feature aiming to streamline work across...
Razer investigates data breach claims, resets user sessions – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Gaming gear company Razer reacted to recent rumors of a massive data breach with a short statement on Twitter, letting...
Microsoft Edge’s Bing AI sidebar will remember previous conversations – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Microsoft’s Edge browser continues to enhance its ‘Copilot experience’ with the Bing AI-powered sidebar. The feature offers various features, such...
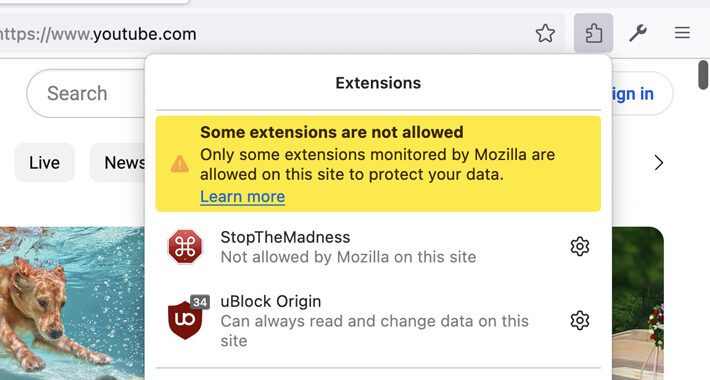
New Mozilla Feature Blocks Risky Add-Ons on Specific Websites to Safeguard User Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 10, 2023THNBrowser Security Mozilla has announced that some add-ons may be blocked from running on certain sites as part of...
New TOITOIN Banking Trojan Targeting Latin American Businesses – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 10, 2023THNEnterprise Security / Malware Businesses operating in the Latin American (LATAM) region are the target of a new Windows-based...
Global Retailers Must Keep an Eye on Their SaaS Stack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 10, 2023The Hacker NewsSaaS Security Brick-and-mortar retailers and e-commerce sellers may be locked in a fierce battle for market share,...
RomCom RAT Targeting NATO and Ukraine Support Groups – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 10, 2023THNCyber Threat / Malware The threat actors behind the RomCom RAT have been suspected of phishing attacks targeting the...
Hackers Steal $20 Million by Exploiting Flaw in Revolut’s Payment Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Malicious actors exploited an unknown flaw in Revolut’s payment systems to steal more than $20 million of the company’s funds in...
Meta’s Twitter rival Threads; user privacy strategies that can protect your account – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Up until last Thursday, OpenAI’s ChatGPT held the record for the fastest stratospheric platform growth ever, reaching 10 million...
MY TAKE: ‘IOWN’ makes the business case for fostering diversity, respecting individual privacy – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido To tap the full potential of massively interconnected, fully interoperable digital systems we must solve privacy and...
RomCom Group Targets Ukraine Supporters Ahead of NATO Summit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The RomCom threat actor has reportedly launched a targeted cyber campaign aimed at organizations and individuals supporting Ukraine just days before...
Crimeware Group Asylum Ambuscade Ventures Into Cyber-Espionage – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Asylum Ambuscade, a crimeware group, has been observed changing tactics and moving to cyber espionage. The group, initially exposed by researchers...
Android OS Tools Fuel Cybercrime Spree, Prey on Digital Users – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cyber-criminals have increasingly utilized specialized mobile Android OS device spoofing tools to bypass anti-fraud controls and impersonate compromised account holders. According...
Central Bankers Develop Framework For Securing Digital Currencies – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 An international financial institution owned by the world’s central banks has published a new framework designed to help members mitigate cyber...
Martin Lewis Shocked at Deepfake Investment Scam Ad – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading UK TV personality has hit out at a lack of regulation for fraudulent internet advertising, after a deepfake likeness...
Cyber Extortion Cases Surge 39% Annually – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Incidents of online extortion reported to the police increased by nearly two-fifths in 2022 compared to a year previously, according to...
TPG to Acquire Forcepoint’s Government Cybersecurity Business Unit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Private equity giant TPG on Monday announced plans to acquire Forcepoint’s Global Governments and Critical Infrastructure (G2CI) business unit in...
Critical Infrastructure Services Firm Ventia Takes Systems Offline Due to Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Critical infrastructure services provider Ventia over the weekend announced that it has taken some of its systems offline to contain...
A Cybersecurity Wish List Ahead of NATO Summit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend As tomorrow’s NATO Summit in Vilnius, Lithuania approaches, SecurityWeek questions what NATO should do about cybersecurity. The Russia/Ukraine conflict offers...