Source: www.govinfosecurity.com – Author: 1 Application Security , Application Security & Online Fraud , DevSecOps Taking a Cybersecurity Mesh Platform Approach to Securing Applications Vince Hwang,...
Day: July 29, 2023
700,000 Sensitive Teacher, Student Records Exposed on Web – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Governance & Risk Management , Healthcare Researcher Says Hackers Could Have Seen Salary Info, Child Abuse Reports and...
US and Australia Warn Developers Over IDOR Vulnerabilities – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 API Security Flaws That Give Back-End Access to an Object Can Cause Large Breaches, Agencies Say Mihir Bagwe (MihirBagwe) • July...
FBI: Hackers Use AI for Sextortion, Explosives, Bad Websites – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development China Seeks to Level AI Playing Field by Stealing IP...
US, Australia Issue Warning Over Access Control Vulnerabilities in Web Applications – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire New guidance from the Australian Cyber Security Centre (ACSC), the US Cybersecurity and Infrastructure Security Agency (CISA), and National Security...
In Other News: Data Breach Cost Rises, Russia Targets Diplomats, Tracker Alerts in Android – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
Exploitation of Recent Citrix ShareFile RCE Vulnerability Begins – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat intelligence company Greynoise says it has observed the first attempts to exploit a recent critical remote code execution (RCE)...
Industry Reactions to New SEC Cyber Incident Disclosure Rules: Feedback Friday – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The US Securities and Exchange Commission (SEC) has adopted new cybersecurity incident disclosure rules for public companies, but there is...
Zimbra Patches Exploited Zero-Day Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Zimbra this week released patches for a cross-site scripting (XSS) vulnerability in Collaboration Suite that has been exploited in malicious...
CoinsPaid Blames North Korean Hackers for $37 Million Cryptocurrency Heist – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cryptocurrency payments firm CoinsPaid says North Korean hacking group Lazarus is likely responsible for the theft of approximatively $37 million...
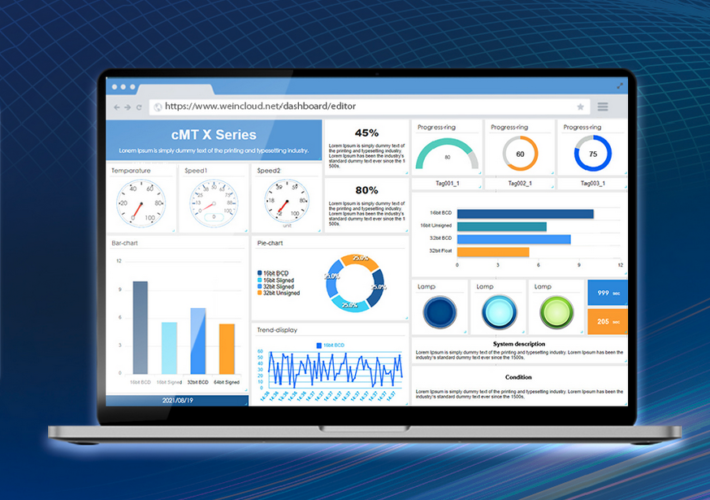
Weintek Weincloud Vulnerabilities Allowed Manipulation, Damaging of ICS Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Several vulnerabilities discovered by a researcher from industrial cybersecurity firm TXOne Networks in a Weintek product could have been exploited...
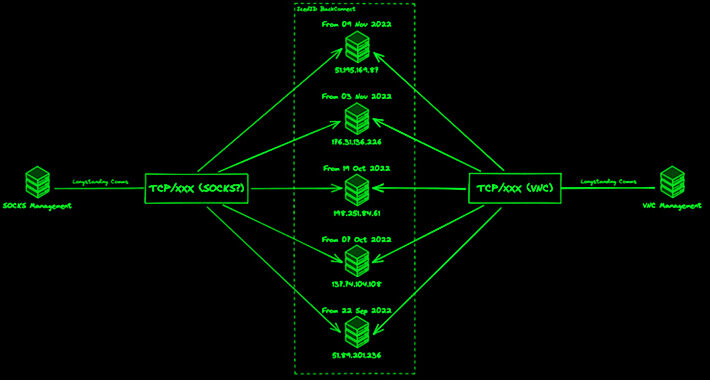
IcedID Malware Adapts and Expands Threat with Updated BackConnect Module – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 28, 2023THNMalware / Cyber Threat The threat actors linked to the malware loader known as IcedID have made updates to...
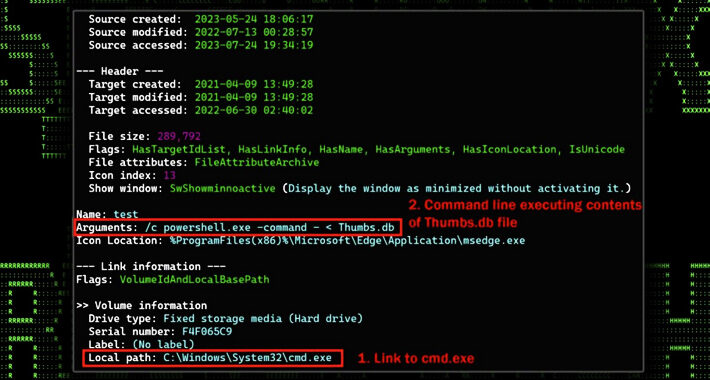
STARK#MULE Targets Koreans with U.S. Military-themed Document Lures – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 28, 2023THNCyber Attack / Malware An ongoing cyber attack campaign has set its sights on Korean-speaking individuals by employing U.S....