Source: thehackernews.com – Author: . Jul 20, 2023THNCyber Attack / Malware The defense sector in Ukraine and Eastern Europe has been targeted by a novel .NET-based...
Day: July 20, 2023
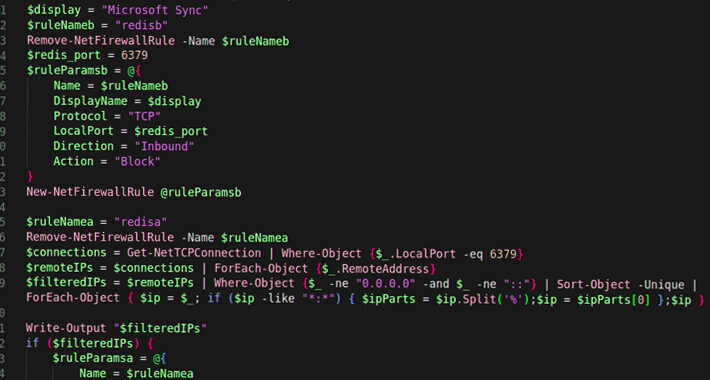
New P2PInfect Worm Targeting Redis Servers on Linux and Windows Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNMalware / Cyber Threat Cybersecurity researchers have uncovered a new cloud targeting, peer-to-peer (P2P) worm called P2PInfect that targets...
Microsoft Expands Cloud Logging to Counter Rising Nation-State Cyber Threats – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNCloud Security / Cyber Espionage Microsoft on Wednesday announced that it’s expanding cloud logging capabilities to help organizations investigate...
Adobe Rolls Out New Patches for Actively Exploited ColdFusion Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNSoftware Security / Vulnerability Adobe has released a fresh round of updates to address an incomplete fix for a...
Practice Your Security Prompting Skills – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Practice Your Security Prompting Skills Gandalf is an interactive LLM game where the goal is to get the chatbot...
5 ways you can leverage AI to defeat cyber crime – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Artificial intelligence doesn’t just bolster cyber security. It serves as a resource-leveling force-multiplier, expanding what’s possible. AI can offer...
MY TAKE: As network perimeters shift and ecosystems blend, the role of MSSPs solidifies – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Deepening interoperability of AI-infused systems – in our buildings, transportation grids, communications systems and medical equipment — portend amazing breakthroughs for...
Smashing Security podcast #331: Boris Johnson’s WhatsApps, and sextorting party girls – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Former Prime Minister Boris Johnson wants to hand over his WhatsApp messages – or does he? And a couple of...
Child identity theft: how do I keep my kids’ personal data safe? – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Phil Muncaster Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Tony Anscombe There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for...
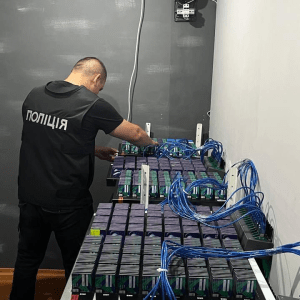
Ukrainian Police Shutter Propaganda-Spreading Bot Farm – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Media Bot Accounts Also Used to Illegally Distribute Ukrainians’ Personal...
Reporting Cyber Incidents Within 72 Hours: Challenges Ahead – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Security Operations , Standards, Regulations & Compliance Stanley Mierzwa of Kean University on Upcoming Reporting Requirements Marianne Kolbasuk...
Ransomware Detection | What MSPs Need to Know – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Russian Hackers Probe Ukrainian Defense Sector With Backdoor – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Novel .NET Backdoor DeliveryCheck Sends a Variety...
Live Webinar | Unmasking Pegasus: Understand the Threat & Strengthen Your Digital Defense – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Jim Coyle U.S. PUBLIC SECTOR SECURITY STRATEGIST, Lookout Jim Coyle is a U.S. public sector security strategist at Lookout Security, utilizing...
White House Unveils Cyber Trust Label for Smart Devices – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Governance & Risk Management , Internet of Things Security Proposed Cybersecurity-Labeling Program to Certify Consumer IoT Devices Prajeet...
Microsoft Expands Logging Access After Chinese Hack Blowback – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development E3 Licensees Unlock Access to More...
Famed Hacker Kevin Mitnick Dead at 59 – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Kevin Mitnick, a hacker who famously served time in prison for various computer and communications-related crimes, has died after a...
Microsoft Bows to Pressure to Free Up Cloud Security Logs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Facing intense pressure to free up access to cloud security logs, Microsoft on Wednesday said it would expand logging defaults...
Recycling Giant Tomra Takes Systems Offline Following Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Norwegian recycling giant Tomra has taken some of its systems offline after falling victim to what it describes as “an...
Two Jira Plugin Vulnerabilities in Attacker Crosshairs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Attackers are apparently trying to exploit two path traversal vulnerabilities in the ‘Stagil navigation for Jira – Menus & Themes’...
Virtual Event Today: 2023 Cloud & Data Security Summit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Mike Lennon SecurityWeek’s 2023 Cloud & Data Security Summit kicks off today! This fully immersive 3D virtual event will take place on Wednesday,...
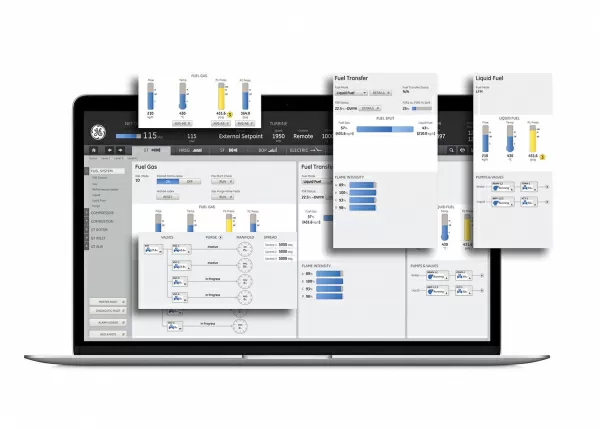
Recently Patched GE Cimplicity Vulnerabilities Reminiscent of Russian ICS Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Over a dozen vulnerabilities patched recently by GE in its Cimplicity product are reminiscent of industrial control system (ICS) attacks...
Security Awareness Training Isn’t Working – How Can We Improve It? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Security awareness training isn’t working to the level it needs to. It doesn’t protect all industries and all people all...
Oracle Releases 508 New Security Patches With July 2023 CPU – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Oracle on Tuesday announced the release of 508 new security patches as part of the July 2023 CPU, including more...
Exploitation of New Citrix Zero-Day Likely to Increase, Organizations Warned – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Citrix on Tuesday announced patches for three vulnerabilities, including an actively exploited zero-day that allows remote code execution. The zero-day,...
Chrome 115 Patches 20 Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Tuesday announced the release of Chrome 115 to the stable channel, with patches for 20 vulnerabilities, including 11...
Ukraine’s cyber police dismantled a massive bot farm spreading propaganda – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Cyber Police Department of the National Police of Ukraine dismantled a massive bot farm and seized 150,000 SIM cards....
US Gov adds surveillance firms Cytrox and Intellexa to Entity List for trafficking in cyber exploits – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. government added surveillance technology vendors Cytrox and Intellexa to an economic blocklist for trafficking in cyber exploits. The...
Citrix warns of actively exploited zero-day in ADC and Gateway – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Citrix is warning customers of an actively exploited critical vulnerability in NetScaler Application Delivery Controller (ADC) and Gateway. Citrix is...