Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek talks to leading Chief Information Security Officers in the payments industry about their role and experience as CISOs. In...
Day: June 22, 2023
DOJ Launches Cyber Unit to Prosecute Nation-State Threat Actors – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The United States Department of Justice (DOJ) has created a new litigating section to increase its ability to disrupt and...
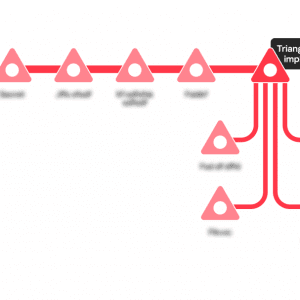
Analyzing the TriangleDB implant used in Operation Triangulation – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Kaspersky provided more details about Operation Triangulation, including the exploitation chain and the implant used by the threat actors. Kaspersky...
Russia-linked APT28 hacked Roundcube email servers of Ukrainian entities – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked APT28 group hacked into Roundcube email servers belonging to multiple Ukrainian organizations. A joint investigation conducted by Ukraine’s Computer...
New Condi DDoS botnet targets TP-Link Wi-Fi routers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers discovered a new strain of malware called Condi that targets TP-Link Archer AX21 (AX1800) Wi-Fi routers. Fortinet FortiGuard Labs Researchers discovered a...
BrandPost: Reducing Cyber Risks by Upskilling Your Security Talent – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | CISOs today face an expanding attack surface, increasingly threats, and a cybersecurity skills gap. An integrated and automated approach to...
BrandPost: Taking a Centralized Approach to Cloud Security – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | CISOs today face an expanding attack surface, increasingly threats, and a cybersecurity skills gap. An integrated and automated approach to...
Why you should review the security of your MSSQL servers – Source: www.csoonline.com
Source: www.csoonline.com – Author: MS SQL Server is by far the most common DBMS that attackers target, probably due to its tight integration with Windows. Brute-force...
Ransomware attacks pose communications dilemmas for local governments – Source: www.csoonline.com
Source: www.csoonline.com – Author: Experts say it’s crucial that local governments communicate with the public following a ransomware attack but must walk a fine line between...
BrandPost: Reducing waste in value generation centers with OT security – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | Cybersecurity has a communication problem. It’s understood that action is needed to improve the global security posture, but ineffective communication...
Baffle launches new user interface to simplify application data security – Source: www.csoonline.com
Source: www.csoonline.com – Author: Baffle Manager 2.0 adds REST APIs, secrets store, certificate store, and SSO to fully automate data protection over SaaS workflows.s iStock Data...
This is what OpenAI’s AI app store will look like… – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: OpenAI, the company behind ChatGPT (the chatbot that has dazzled the internet), wants to create a marketplace that will...
News Alert: NowSecure Achieves SOC 2 Type 2 certification for 4th consecutive year – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Chicago, Ill., June 21, 2023 – NowSecure, the recognized experts in mobile security and privacy, announced today that it has completed...
News Alert: IRONSCALES beta-launches a new generative AI tool to improve email security – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Atlanta, Ga. June 20, 2023 – IRONSCALES, the leading enterprise cloud email security platform protecting more than 10,000 global organizations worldwide,...
News Alert: Survey shows vast majority of IT pros consider ‘passwordless’ access a top priority – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Santa Clara, Calif. – June 21, 2023 – Axiad, a leading provider of organization-wide passwordless orchestration, today announced the results of...
GUEST ESSAY: Taking a fresh approach to privileged access management — to curtail abuse – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Ravi Srivatsav To be productive in an interconnected work environment, employees need immediate access to numerous platforms, both on- and...
News Alert: Dropblock mobile app gives developers, businesses secure data storage and sharing – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido London, UK, June 15, 2023 – Dropblock for mobile launches today, a free, Web3 storage application offering individuals, developers, and business...
Ethical Problems in Computer Security – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Tadayoshi Kohno, Yasemin Acar, and Wulf Loh wrote excellent paper on ethical thinking within the computer security community: “Ethical Frameworks...
#InfosecurityEurope: From Passion to Profession, Becky Pinkard’s Dedication to Cybersecurity – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Becky Pinkard describes herself as an outsider who found her place, and was able to express her true identity, in the...
US Senate Leader Champions More AI Security, Explainability – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Guardrails Needed to Stop AI Misuse...
Chinese Hackers Targeted G7 Summit Through MS Office Flaw – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering APT Group Masqueraded as Indonesia’s Foreign Ministries in Emails...
Advanced Threat Hunting: Cutting-Edge Techniques for Seasoned Cyber Defenders – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
DOJ’s New Cyber Unit to Focus on Nation-State Cybercrimes – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Standards, Regulations & Compliance US Justice Department Aims to Accelerate Disruption...
State Fines Kaiser Permanente $450K for PHI Mailing Blunder – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , HIPAA/HITECH , Privacy System Update Error Triggered the Mailing of 337,747 Letters to Old Addresses Marianne...
iOttie discloses data breach after site hacked to steal credit cards – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Car mount and mobile accessory maker iOttie warns that its site was compromised for almost two months to steal online...
Exploit released for Cisco AnyConnect bug giving SYSTEM privileges – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Proof-of-concept exploit code is now available for a high-severity flaw in Cisco Secure Client Software for Windows (formerly AnyConnect Secure...
APT37 hackers deploy new FadeStealer eavesdropping malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The North Korean APT37 hacking group uses a new ‘FadeStealer’ information-stealing malware containing a ‘wiretapping’ feature, allowing the threat actor...
Apple fixes zero-days used to deploy Triangulation spyware via iMessage – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Apple addressed three new zero-day vulnerabilities exploited in attacks installing Triangulation spyware on iPhones via iMessage zero-click exploits. “Apple is...
UPS discloses data breach after exposed customer info used in SMS phishing – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Multinational shipping company UPS is alerting Canadian customers that some of their personal information might have been exposed via its...
FTC: Amazon trapped millions into hard-to-cancel Prime memberships – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Federal Trade Commission (FTC) says Amazon allegedly used dark patterns to trick millions of users into enrolling in its...